Novel file-static-structure-attribute-based malware detection method
A static structure, malware technology, applied in the direction of platform integrity maintenance, instrumentation, electrical digital data processing, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
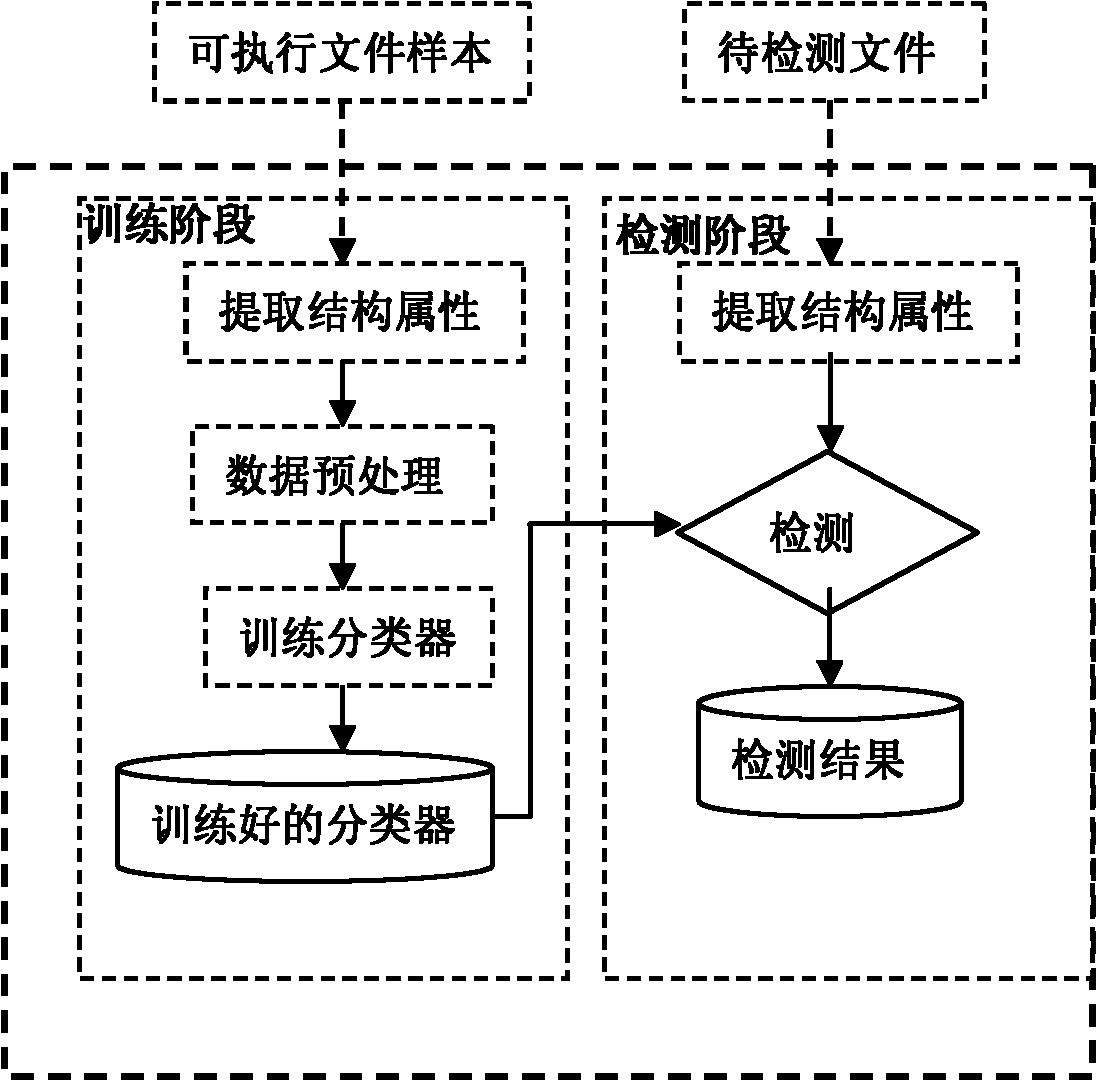
[0068] Detection model and basic idea:
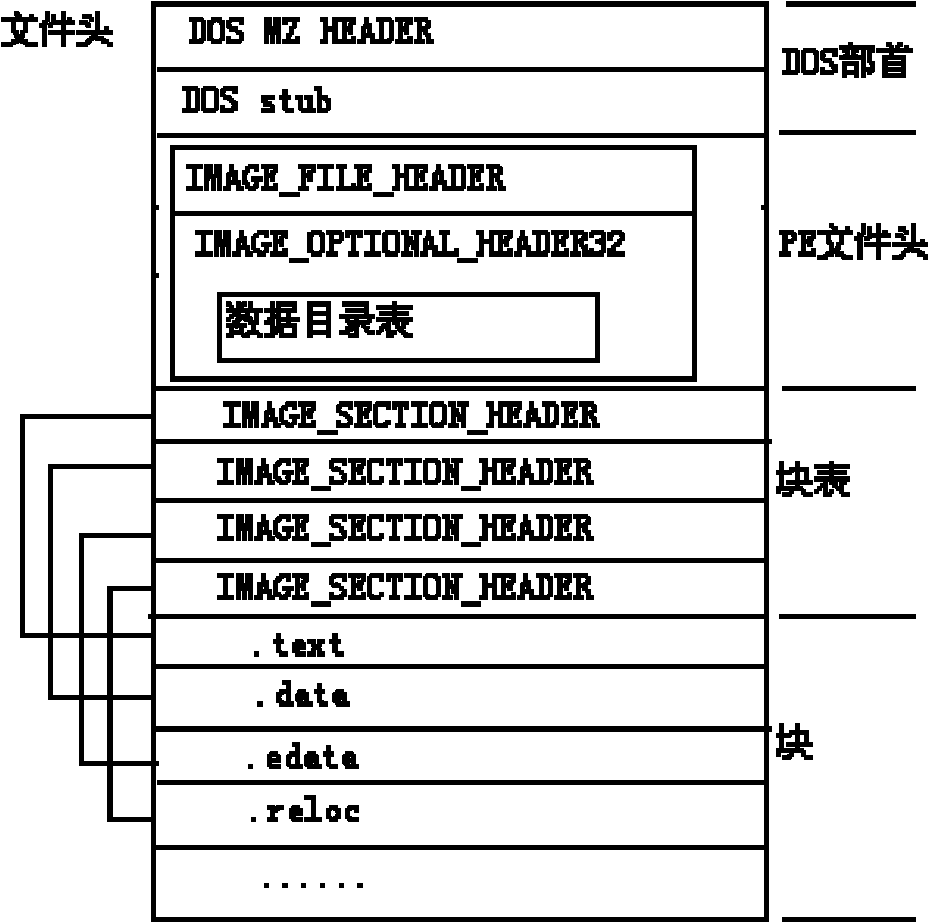
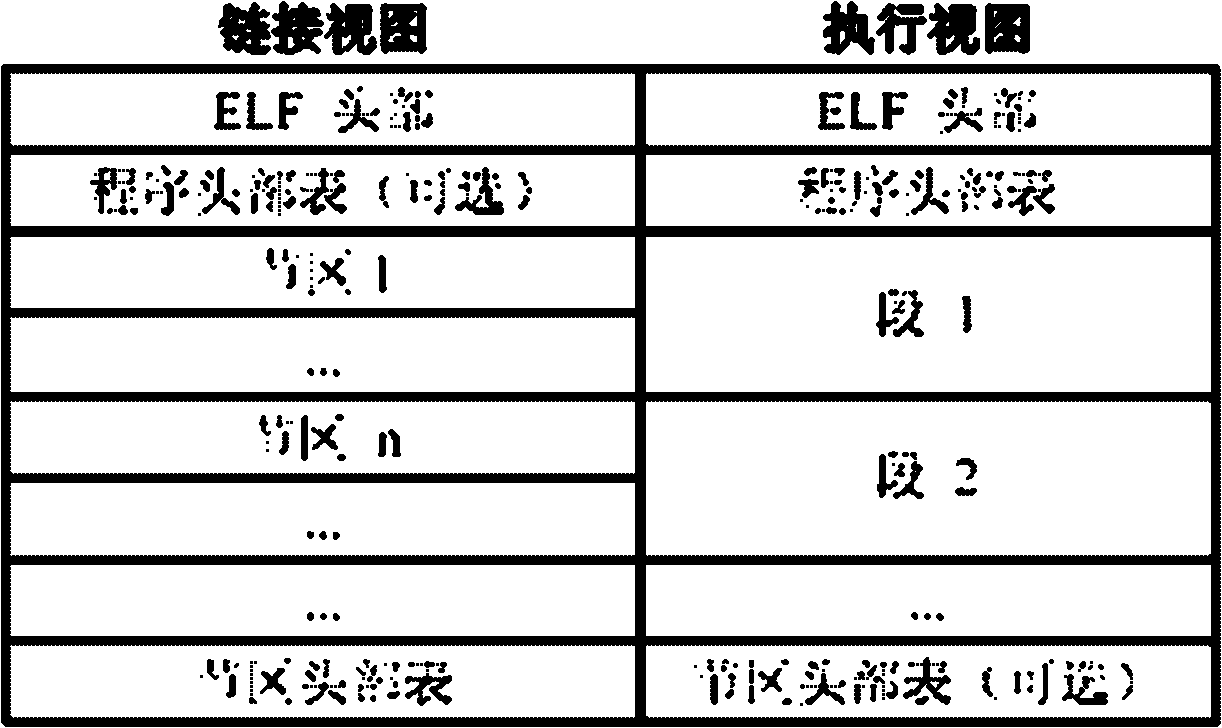
[0069] The idea on which the present invention is based is that the behavior and nature of the software will definitely be reflected in the static structural attributes of the software, and by analyzing the static structural attributes of the software, the attributes that have a good degree of discrimination between malicious software and normal software are extracted , using a classification algorithm to learn, so that malware and normal files can be correctly identified. The present invention analyzes the PE files under the WINDOWS platform and the ELF files under the LINUX platform, and analyzes the static structural attributes of the files from the concept of software structural integrity. These attributes can measure the credibility of software; Various types of software, including software, use statistical methods to obtain the value distribution characteristics of these structural attributes in similar software. These results pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com