Automatic protecting method for computer system based on Bluetooth device authentication
A computer system and bluetooth device technology, applied in the field of information security, can solve the problems of inability to achieve real-time monitoring and high cost, and achieve the effects of low cost, transparent operation, and simplified operation mode.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The key technologies and specific implementation methods of the present invention will be described in detail below in conjunction with the accompanying drawings.
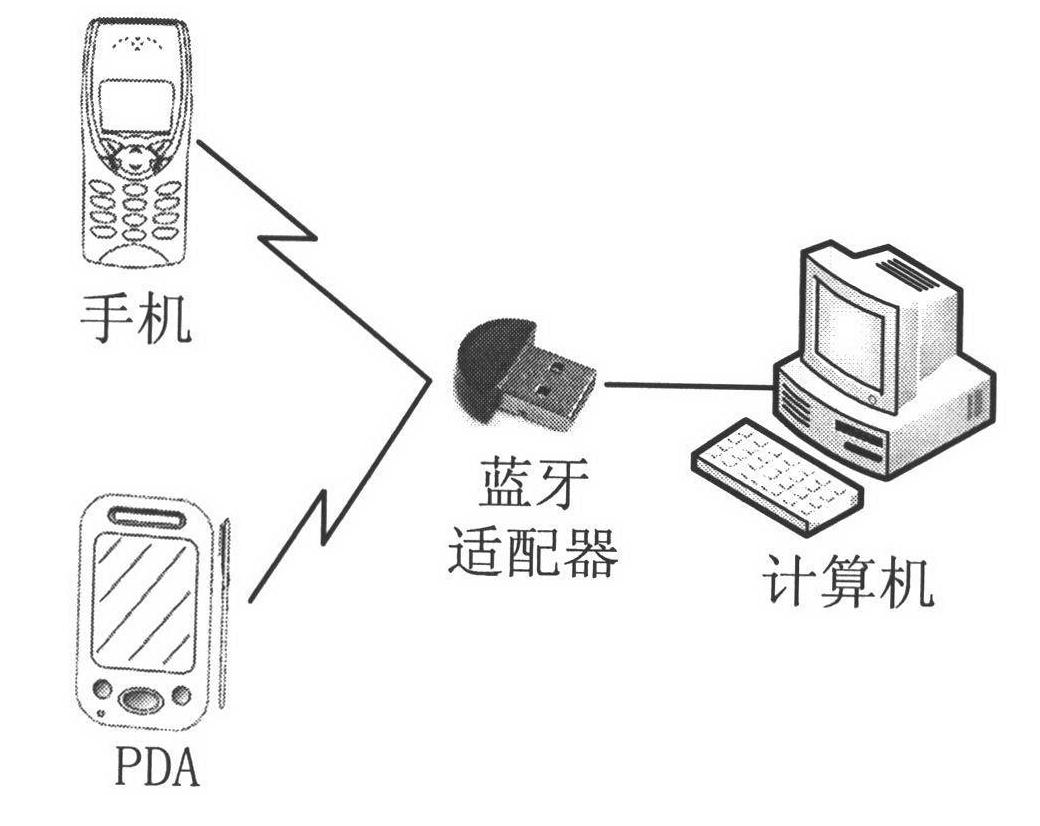
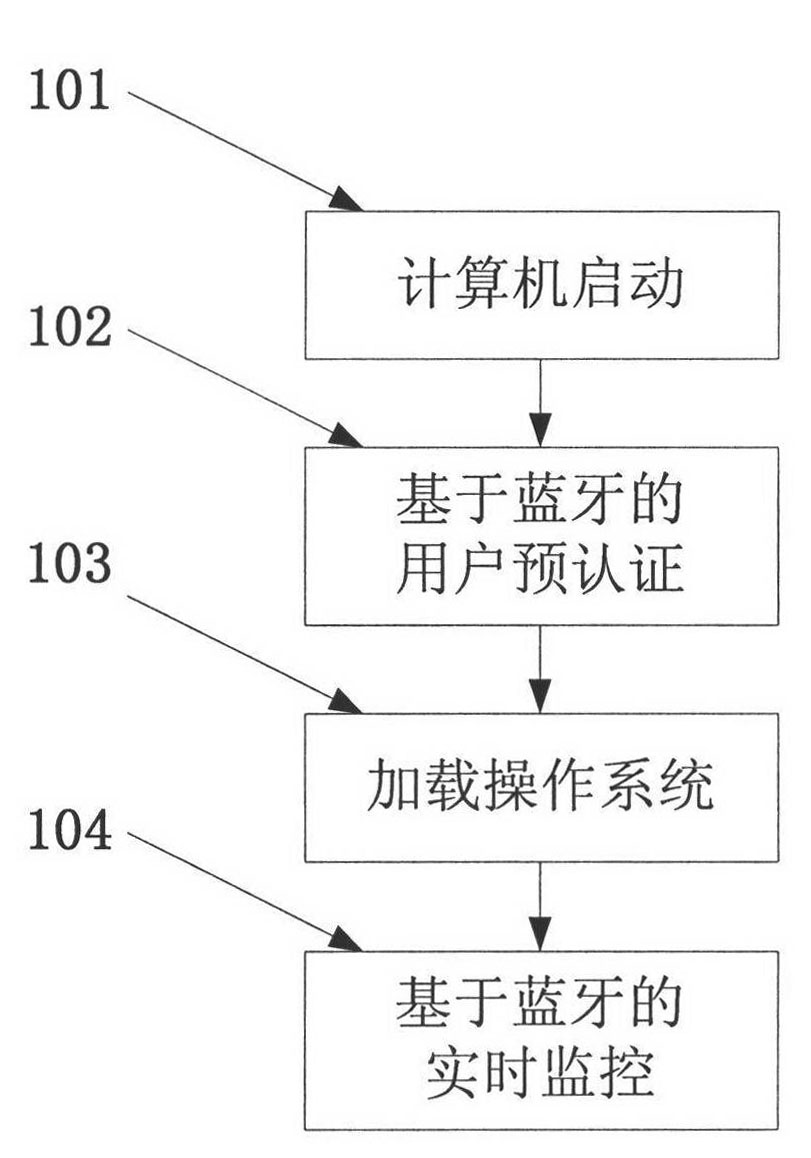
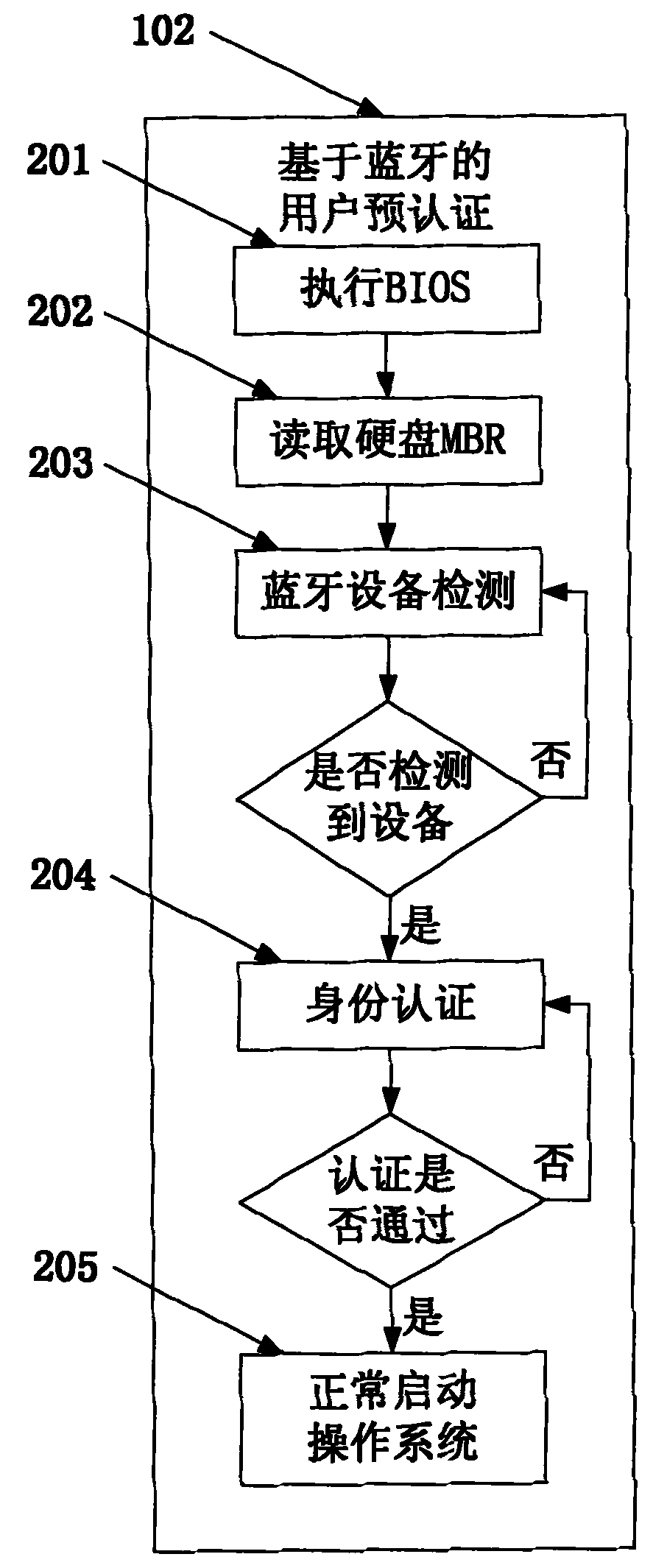
[0064] Such as figure 1 As shown, the application scenario of the present invention includes a user's mobile phone or PDA, a Bluetooth adapter and a computer, and the Bluetooth adapter can be a general-purpose USB Bluetooth adapter. The computer equipped with protection software automatically executes the BIOS after booting, and then interacts with the Bluetooth of the user's mobile phone or PDA through the Bluetooth adapter connected to it, obtains the Bluetooth address and IMSI number of the user's device, and waits for the user to enter the PIN code. The user enters the PIN code on the mobile phone or PDA, and the computer calculates the authentication key through a specific algorithm to complete the device authentication between the mobile phone Bluetooth and the computer Bluetooth adapter, as well as th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com