Information security protecting system and method of mobile terminal
A mobile terminal and information security technology, applied in computer security devices, digital data protection, instruments, etc., can solve problems such as high system resources and poor user experience, and achieve strong scalability, good user experience, and comprehensive protection Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
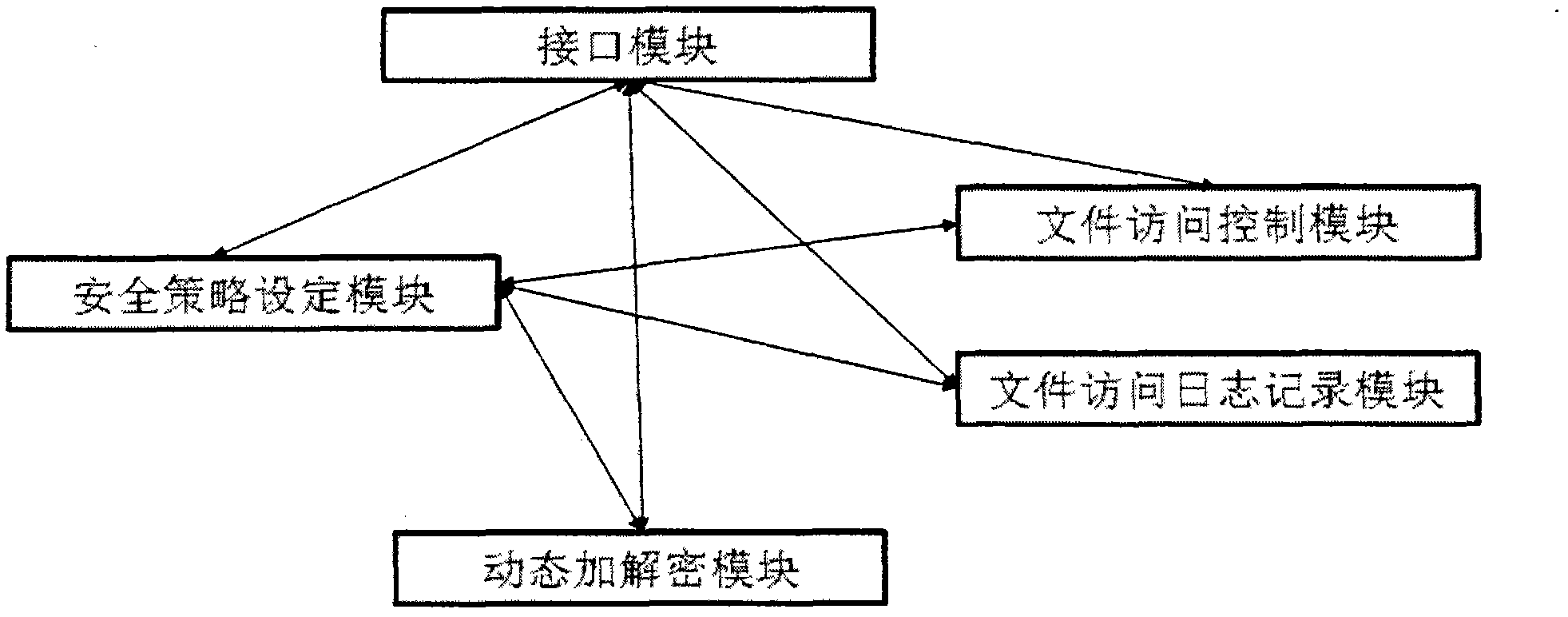
[0023] The application of the present invention is illustrated by taking an Android smart phone as an example.
[0024] The Android system is divided into four levels: Applications (application layer), Application Frameworks (application framework layer), Libraries and Android Runtime (class library and real-time runtime library layer), Linux Kernel (Linux kernel layer).
[0025] 1. Applications (application layer)
[0026] Android will pre-install a set of core applications, including email client, SMS service, calendar schedule, map service, browser, contacts and other applications. All applications are written in the Java programming language.
[0027] At the application layer, all applications that store information based on files can implement dynamic encryption and decryption protection for files operated by the applications by calling the API provided by the interface module of the present invention.
[0028] 2. Application Frameworks (application framework layer)
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com