Method for binding hardware encryption trans-flash (TF) card with mobile phone subscriber identity module (SIM) card
A hardware encryption and mobile phone technology, applied in electrical components, user identity/authority verification, security devices, etc., can solve problems such as saving only pictures, audio files and video files, not being able to save many files, and occupying memory independently , to achieve the effects of saving design costs, large data storage capacity, and simplifying the manufacturing process and structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
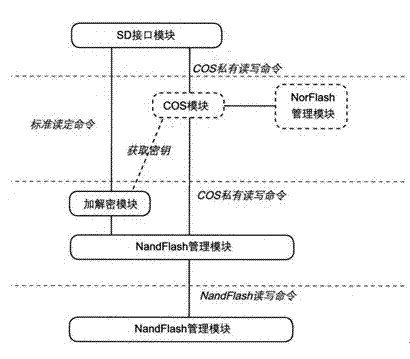
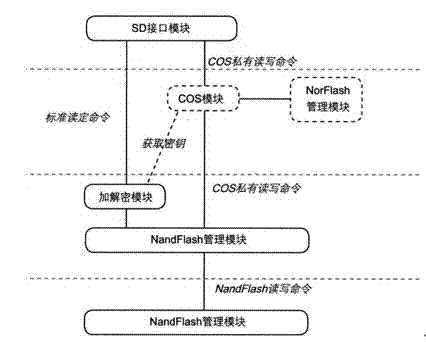
[0015] The hardware encrypted TF card is bound to the SIM card of the mobile phone to realize the unique pairing function of the hardware encrypted TF card and the SIM card.
[0016] The host or mobile phone only needs to upgrade the software to support the TF card hardware encryption technology, and does not need to add or change the hardware; it can be applied to data security access, identity authentication and mobile e-commerce; to realize the terminal remote query center server information; when the SIM card is changed , the hardware encryption TF card program is automatically closed, and any external access to the TF card is denied.
[0017] Adopt Micro SD (TF card 15mm×11mm×1mm) before packaging, built-in SD / SDIO module, encryption and decryption module, COS module, NandFlash management module and NandFlash medium, among which, SD / SDIO module is connected through encryption and decryption module and COS module respectively The NandFlash management module is connected to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com