Asymmetric double image encryption method based on joint of fourier transformation and phase cutting
A technology of Fourier transform and inverse Fourier transform, which is applied in the field of security encryption of asymmetric images, can solve problems such as the increase of system complexity, and achieve the effect of strong anti-deciphering ability and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
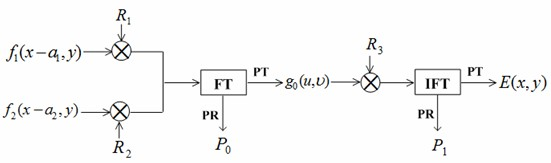
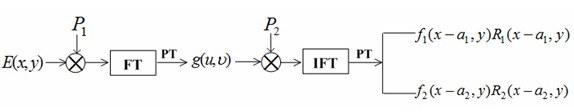
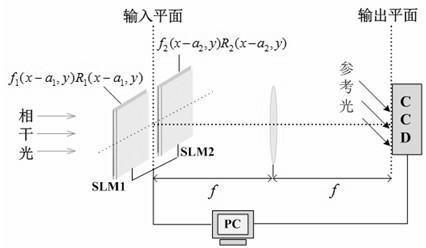
[0060] The present invention is described in detail below in conjunction with embodiment and with reference to accompanying drawing: the encryption decryption process of the method for the present invention can pass image 3 , Figure 4 The optoelectronic hybrid system shown is realized. Spatial light modulators (spatial light modulators, SLM) have the ability to display complex amplitude signals. The encryption process is divided into two steps:
[0061] (1) During the encryption process, the computer-controlled SLM1 and SLM2 are used to display the input information f 1 (x-a 1 ,y)×R 1 (x-a 1 , y) and f 2 (x-a 2 ,y)×R 1 (x-a 2 , y), that is, the input information is:
[0062] u 0 (x, y) = [f 1 (x-a 1 ,y)×R 1 (x-a 1 ,y)]+[f 2 (x-a 2 ,y)×R 2 (x-a 2 ,y)].
[0063] Under the irradiation of unit amplitude plane light wave, the joint Fourier transform of the input information can be realized by using the convex lens, and the result of the transformation is the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com