Memory redundancy eliminating method
A redundancy elimination and memory technology, applied in the direction of memory address/allocation/relocation, etc., can solve the problem of data redundancy in memory, and achieve the effect of improving memory usage efficiency and improving usage efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
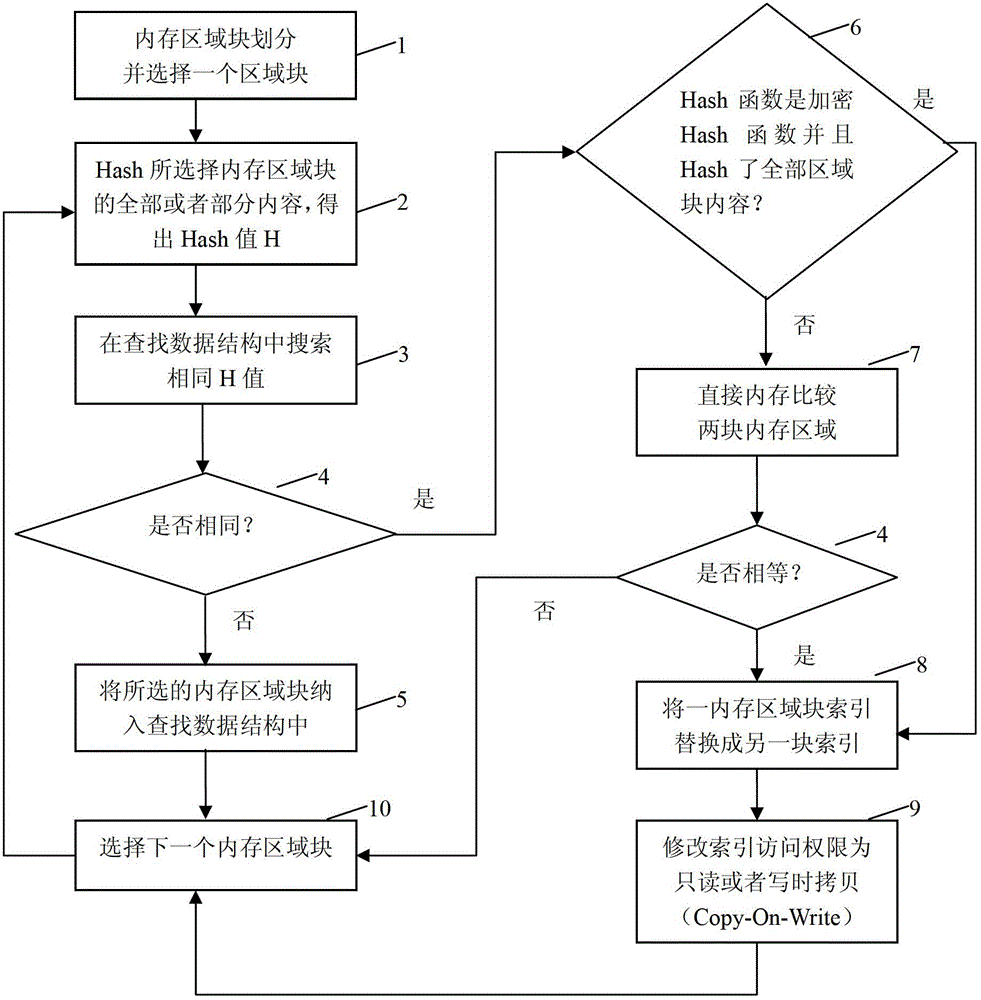
[0054] This embodiment discloses a method for eliminating memory redundancy in a cloud computing environment based on the division of physical page frames of memory area blocks, including the following steps:
[0055] Step 1, using virtualization technology to manage the memory block division method to divide the computer memory into different physical page frames, by scanning the page table managed by the computer virtual memory, selecting one of the physical page frames, and initializing the search data structure;
[0056] Step 2, using an encrypted hash function or a non-encrypted hash function to calculate the hash value of all or part of the content of the currently selected physical page frame as the hash value of the currently selected physical page frame;
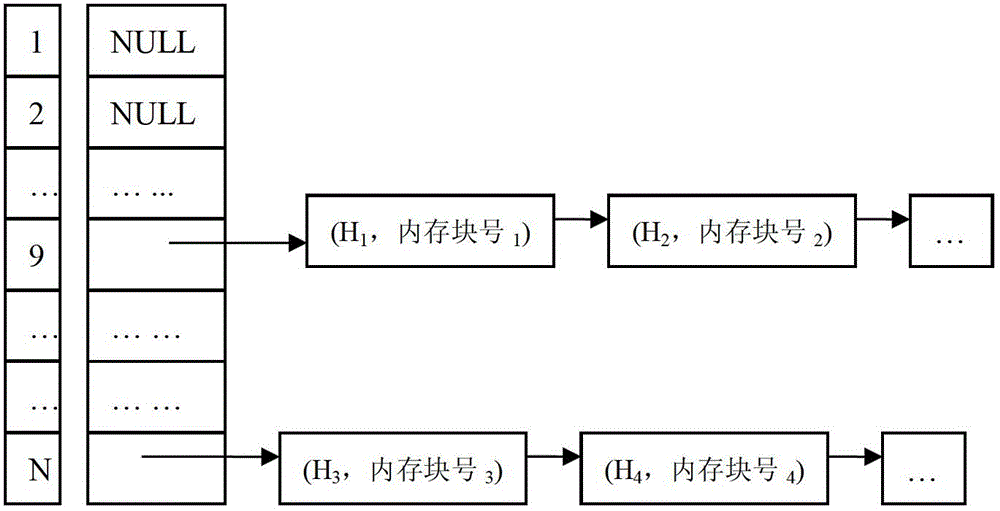
[0057] Step 3, from the search data structure, find whether there is any other physical page frame whose hash value is the same as the hash value of the physical page frame in step 2;
[0058] Step 4, if yes, determ...
Embodiment 2
[0066] This embodiment discloses a method for eliminating memory redundancy in a cloud computing environment based on an operating system mapping memory block division method. Based on the characteristics of the platform, it is assumed that the implementer determines that the redundancy granularity of the memory is large, and the hardware provides special optimization for the encryption Hash function SHA1 (such as VIA's C7 processor chip).
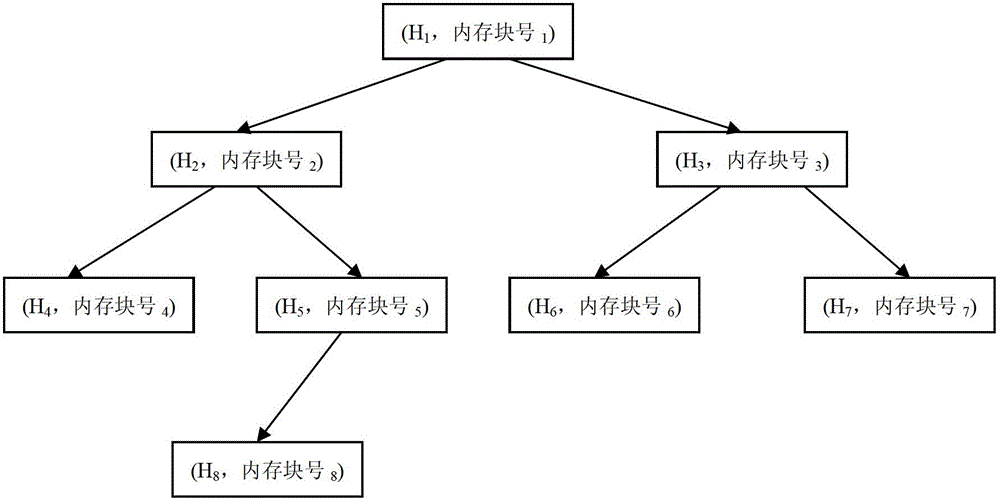
[0067] Such as Figure 4 As shown, assuming that the existing process P in the system 1 ,P 2 、…P i etc., each of which has a different number of mapped memory area blocks, which are linked in their respective process control blocks (PCBs) in order of addresses.
Embodiment example
[0068] This implementation case includes the following steps:
[0069] Step 1. Divide the system memory into different memory blocks based on the operating system mapped memory block (the memory mapped block generated by the mmap system call), according to the double order of the process number in the system from large to small, and the process address from large to small The standard selects the first memory block. Initialize the search data structure as an empty red-black tree (contains 0 tree nodes);
[0070] Step 2, initialize the encryption engine used by the CPU (C7) to calculate the SHA1 hash value, fill all the contents of the selected memory area into the engine and execute the SHA1 calculation to obtain a 160-bit hash value H;
[0071] Step 3, from the search data structure, red-black tree, find whether there are other memory areas with the same hash value as the selected memory area in step 2;
[0072] Step 4, if yes, consider that the contents of the two memory a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com