A method and system for configuring access control parameters
A technology of access control and configuration method, which is applied in the field of shared network, can solve the problems of system message bit increase, UE power consumption increase, frequency increase, etc., to reduce bit number and update frequency, reduce power consumption, and better load control Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
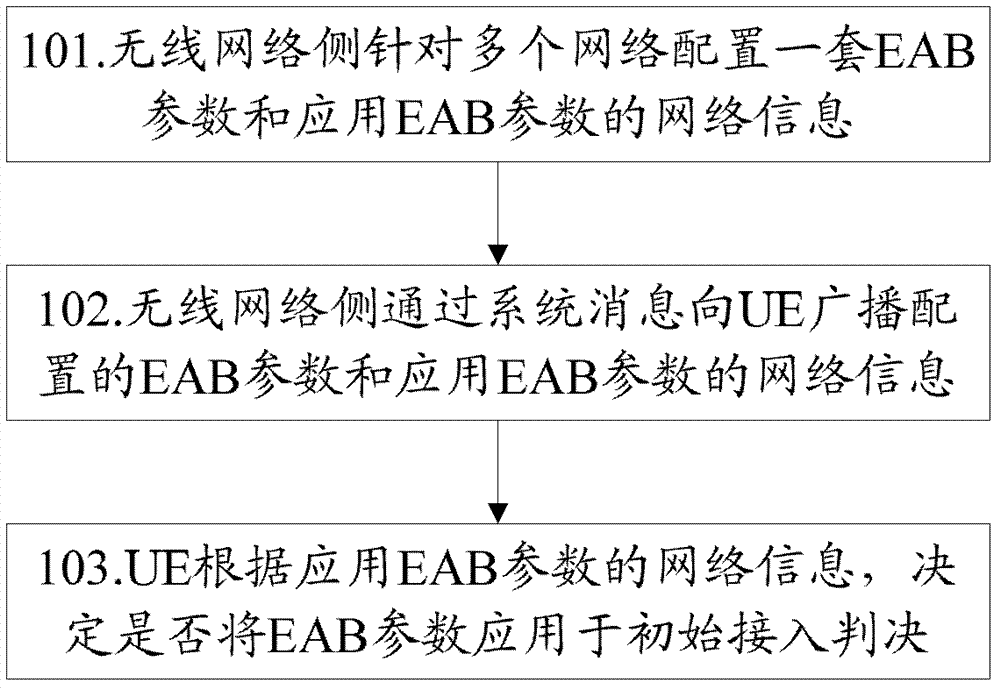
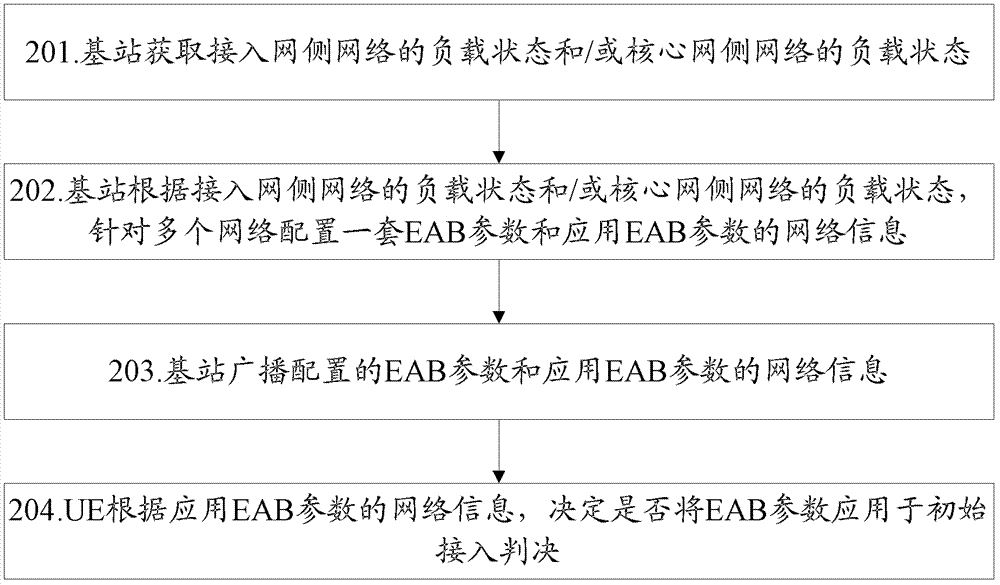
[0042] figure 2 It is a schematic flow chart of Embodiment 1 of the method for configuring access control parameters in the present invention. In an LTE system, a cell under the jurisdiction of a base station is a cell shared by multiple networks, and the network list (PLMNIdentity List) contained in its system message is as follows: Network PLMN 1, Network PLMN 2 and Network PLMN 3; in order to cope with the large-scale introduction of UEs or communication devices suitable for EAB, the base station needs to broadcast EAB parameters in the cell to control UEs accessing the network and control the load of the network, such as figure 2 As shown, the method includes the following steps:
[0043] Step 201, the base station obtains the load status of the access network side network and / or the load status of the core network side network;
[0044] Specifically, the base station can obtain the network (Selected PLMN) selected by the UE from the UE accessing the network, and then m...
Embodiment 2
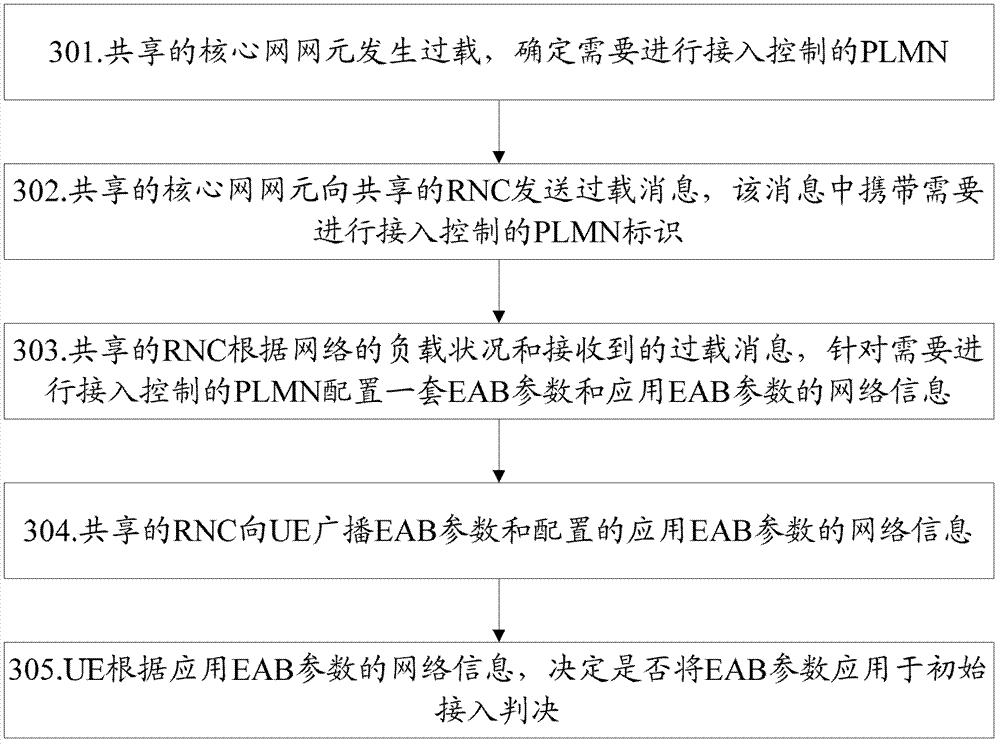
[0058] image 3 It is a schematic flow diagram of Embodiment 2 of the method for configuring access control parameters in the present invention. In the LTE system, in the UMTS shared network, the shared radio network controller (RNC, Radio Network Controller) uses EAB parameters to configure the access control parameters of the access network. UE performs access control, such as image 3 As shown, the method includes the following steps:
[0059] In step 301, a shared core network element is overloaded, and a PLMN that needs access control is determined.
[0060] In step 302, the shared core network element sends an overload message to the shared RNC, and the message carries the identification of the PLMN that needs to perform access control.
[0061] In this embodiment, the networks broadcast in the cell (one or more cells) under the jurisdiction of the RNC include PLMN1, PLMN 2, PLMN 3, and PLMN 4, and the PLMN identification contained in the overload message sent by the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com