Malicious-software characteristic clustering analysis method and system based on behavior segment sharing
A malicious software and clustering analysis technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as inability to support intelligent automatic analysis, alleviate centralized system computing bottlenecks, computing and communication bottlenecks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
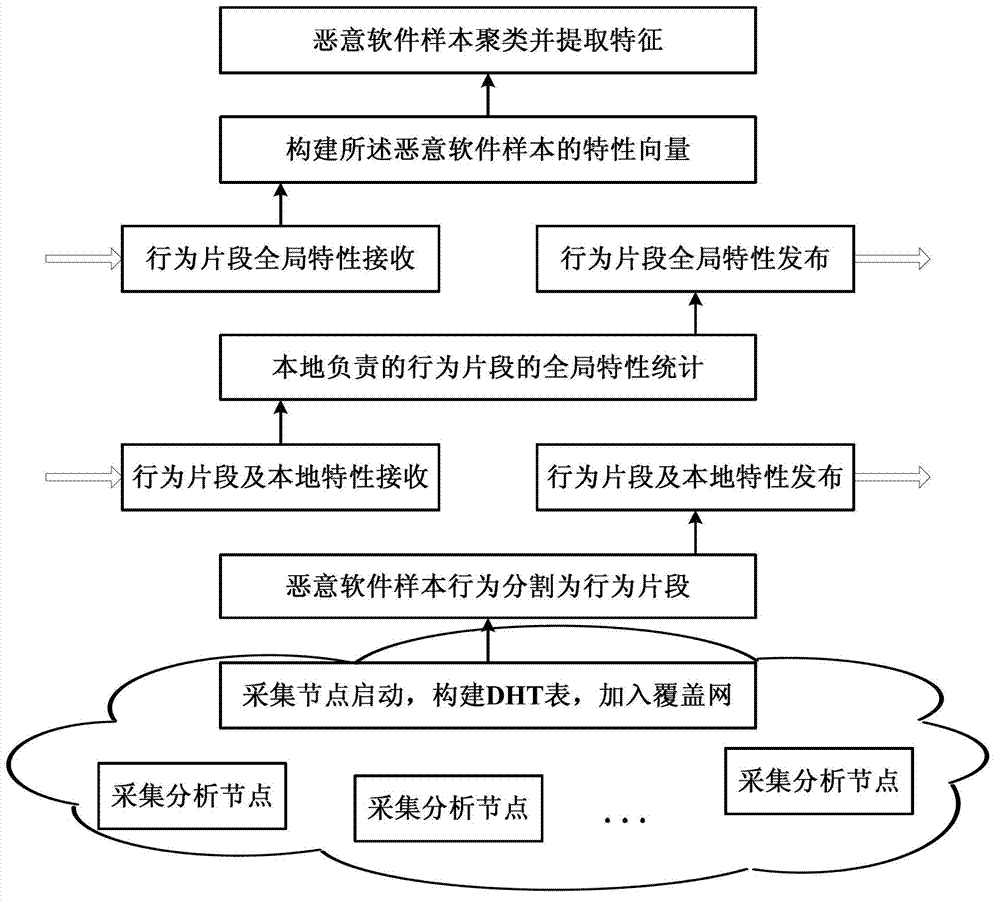
[0089] Such as figure 1 As shown, the implementation steps of the malware feature cluster analysis method based on behavior segment sharing in this embodiment are as follows:
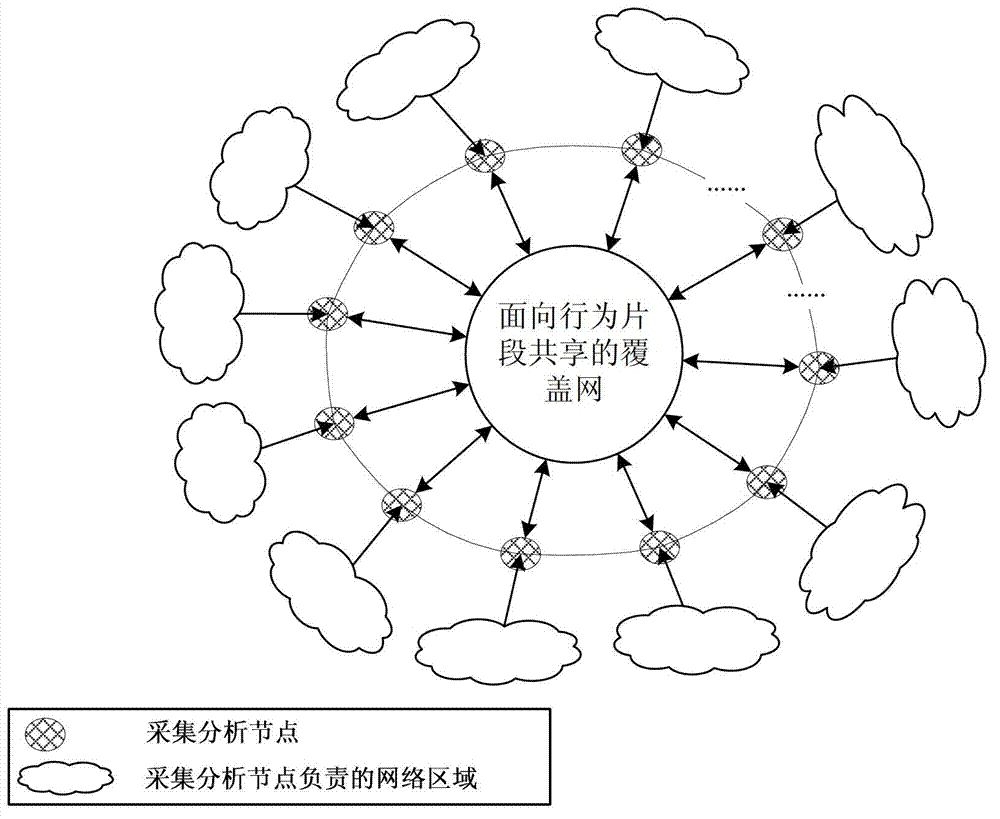
[0090] 1) Arrange geographically dispersed collection and analysis nodes in the network. Each collection and analysis node is responsible for the collection and analysis of malware samples in a network area. A distributed hash table for building a distributed hash table is established in the collection and analysis nodes. Hashtable module;
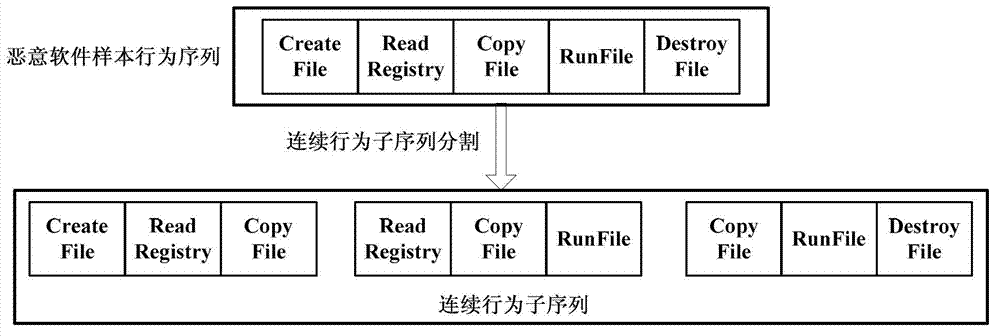
[0091] 2) The collection and analysis node divides the behavior of the collected malware samples into multiple behavior fragments;
[0092] 3) The collection and analysis nodes obtain the local statistical characteristics of the behavior fragments, share the behavior fragments and their local statistical characteristics with the distributed hash table module, and store the behavior fragments and their local statistical characteristics in the distributed hash table ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com