System and method for malicious code analysis based on cloud computing
A malicious code and malicious code detection technology, applied in computing, transmission systems, computer security devices, etc., can solve the problems of large host resource consumption, weak rapid response ability, and lagging recognition ability, so as to reduce security risks, quickly analyze and Fast processing, the effect of fast discovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
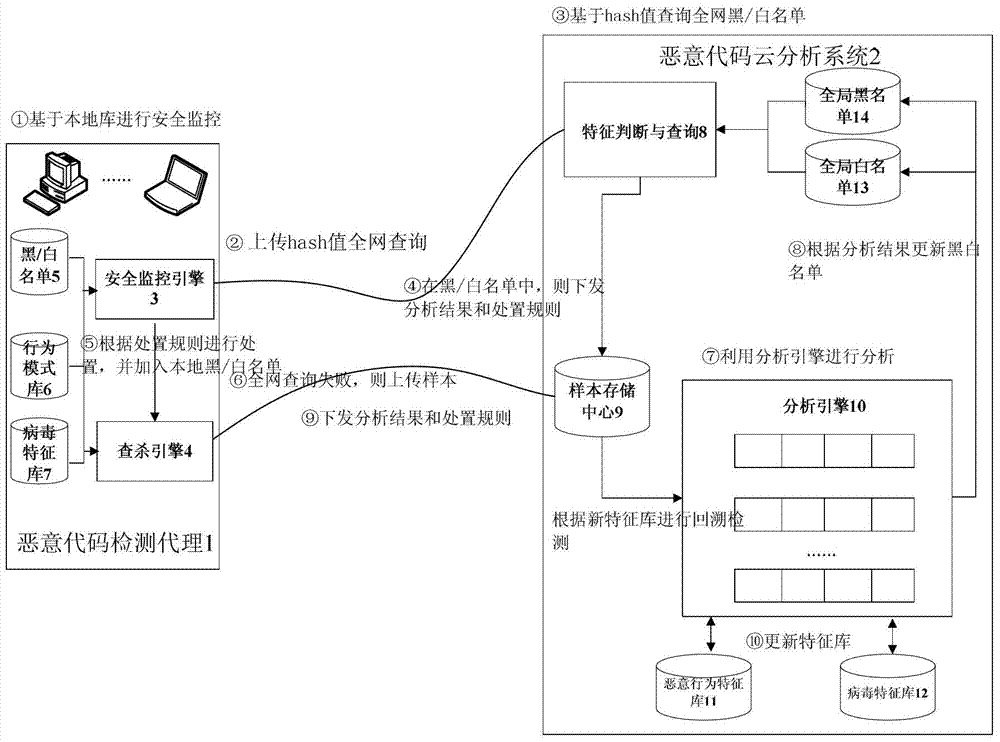
[0032] A malicious code analysis system based on cloud computing includes a malicious code detection agent 1 and a malicious code cloud analysis system 2 . In order to reduce the impact of new security threats and host performance due to its own complexity, and improve the rapid discovery, analysis and processing capabilities of intrusion threats, the host malicious code analysis system separates the core detection and analysis engine from the host. The host-side malicious code detection agent 1 only retains the functions of state detection, behavior monitoring, and killing, and the required complex detection and analysis functions are provided by the malicious code cloud analysis system in the form of network services on the server side. Among them, the malicious code detection agent 1 includes a security monitoring engine 3, an killing engine 4, a local black / white list 5, a behavior pattern library 6, and a virus signature library 7; the malicious code cloud analysis system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com