A Single Event Soft Error Vulnerability Identification Method Applicable to Processor System
A processor system and identification method technology, applied in software testing/debugging and other directions, can solve problems such as high fault test coverage requirements, weak application scope and versatility, and difficult technical implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Specific embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
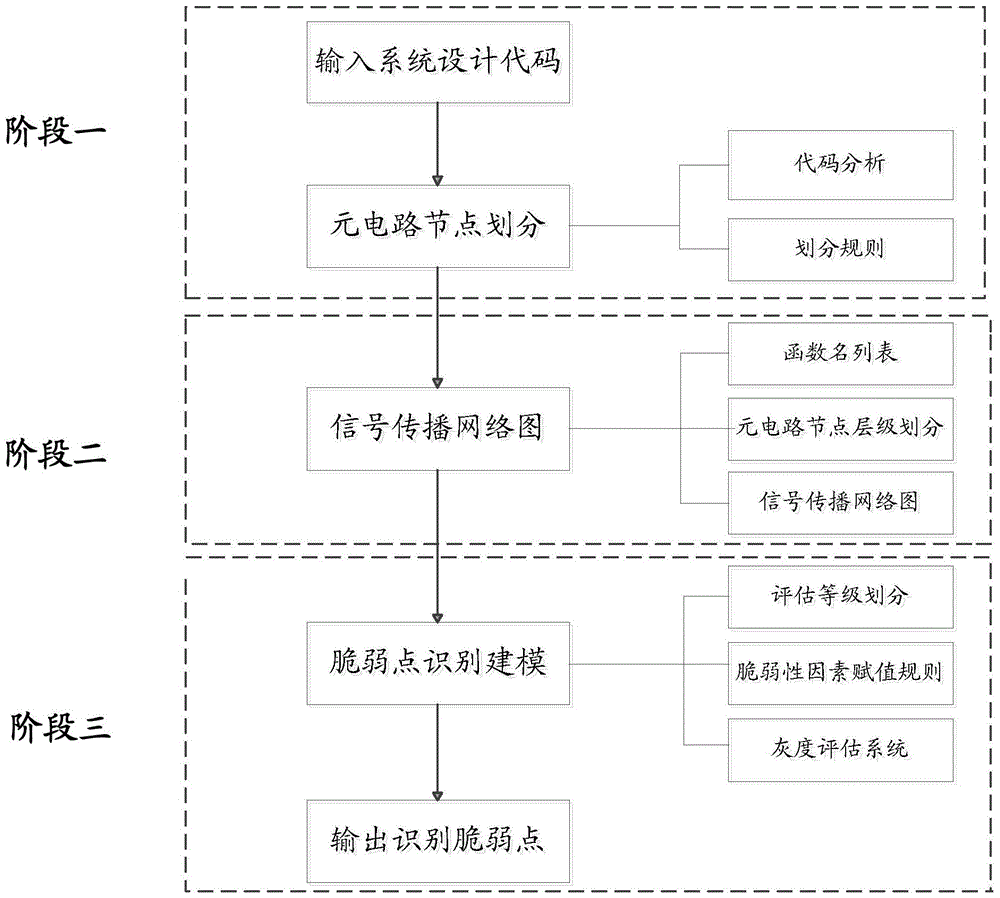
[0053] Such as figure 1 As shown, the present invention is applicable to a single event soft error vulnerability identification method of a processor system, including the following three stages:
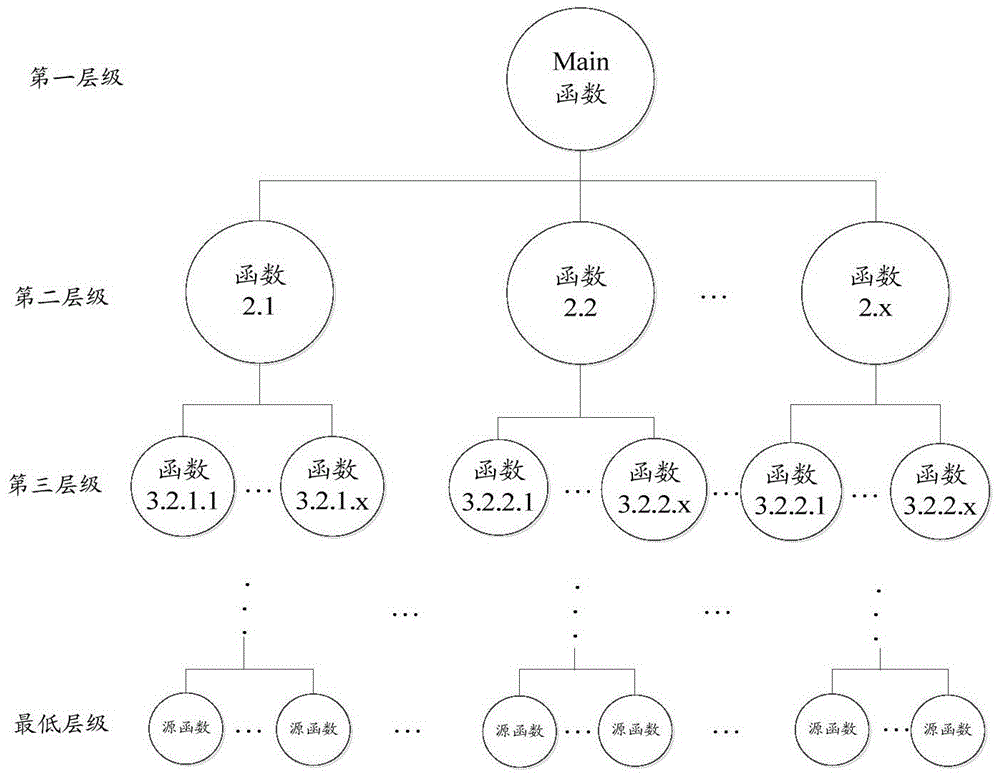
[0054] Stage 1: Meta-circuit node division: According to the functional design architecture of the system, analyze the code structure, and complete the mapping of the function segment of the pre-compiled code (such as C language code) and the instruction sequence set completed by the compiler to complete the meta-circuit node Division; the meta-circuit is a specific function or sub-function module that completes the precompiled code or instruction sequence; stage 1 includes specific implementation steps (1)-(3).
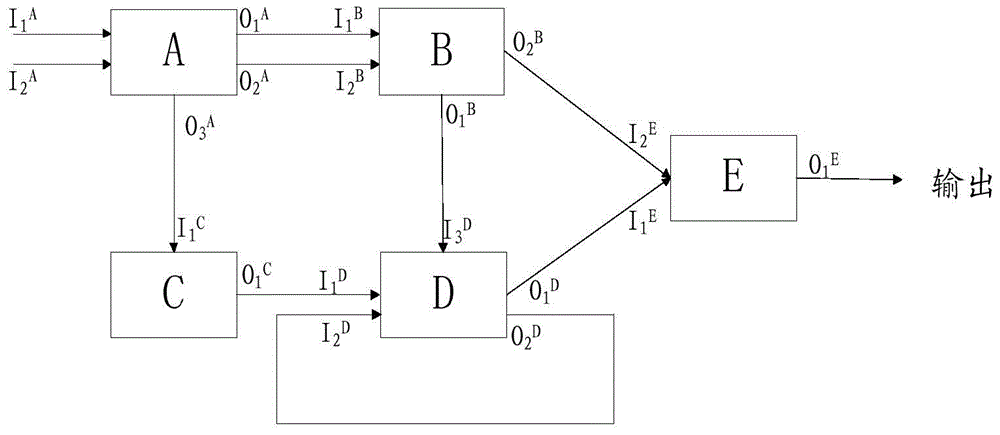
[0055] Stage 2: Construction of the signal propagation network diagram; use the meta-circuit nodes divided in stage 1 to constru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com