A malicious program intelligent defense system and defense method in cloud computing environment
An intelligent defense system, cloud computing environment technology, applied in computing, computer security devices, instruments, etc., can solve the problems of limitations, lag, limited number of samples, etc., achieve low computing resource consumption, high-performance computing power, reduce The effect of threat likelihood
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to describe the technical content of the present invention in detail, the following examples are given and described in detail with accompanying drawings.
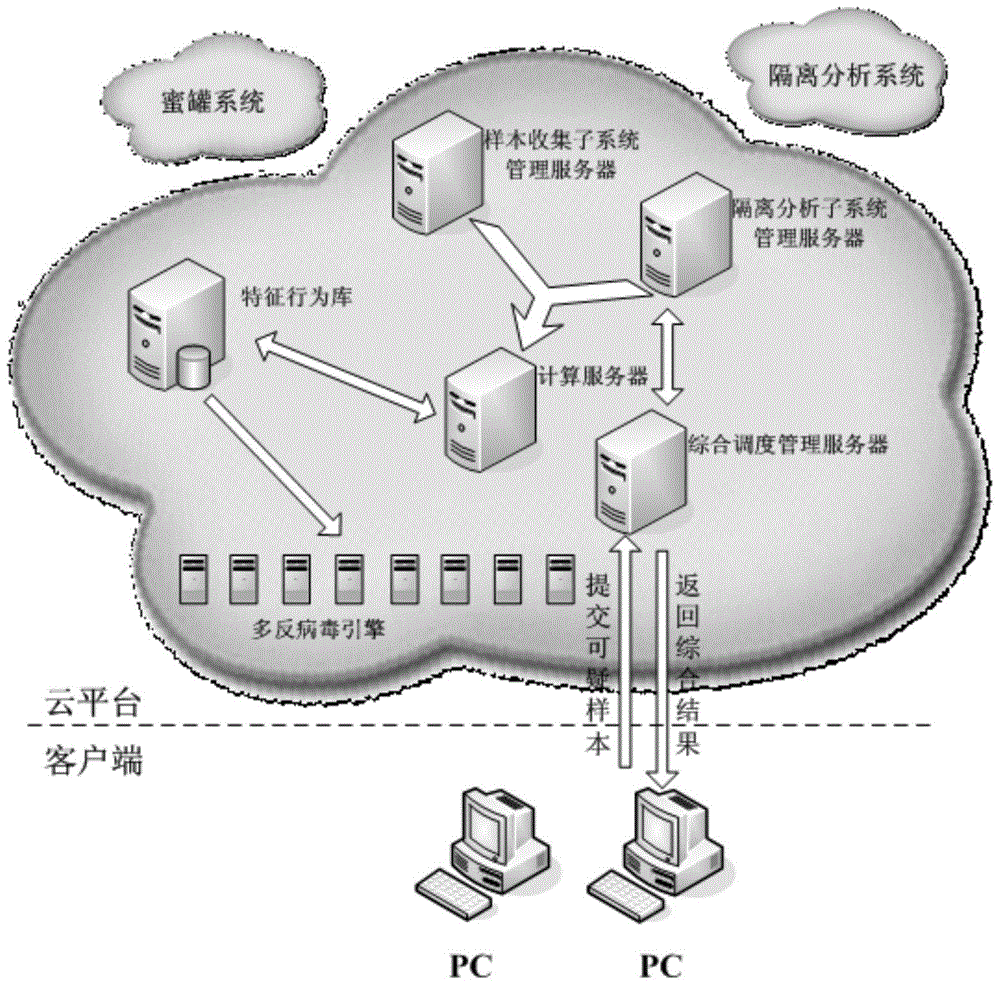
[0032] see figure 1 . A malicious program intelligent defense system in a cloud computing environment that fully guarantees the update of the anti-virus engine knowledge base and improves the ability to detect unknown viruses, including:
[0033] A cloud computing platform, the cloud computing platform is provided with a plurality of different anti-virus engines in parallel, and the different anti-virus engines scan for different types of viruses;
[0034] A sample collection subsystem, the sample collection subsystem collects data related to security vulnerability attacks;
[0035] An isolation analysis subsystem, the isolation analysis subsystem is a collection of multiple malicious program behavior analysis engines, and the isolation analysis subsystem analyzes and obtains behavior monitoring results w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com