A wireless information security device system and method
A technology for information security, wireless transceiver equipment, applied in the field of wireless information security equipment system, can solve the problems of computer crash, data loss, inconvenience, etc., to achieve high practical value and improve the effect of convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
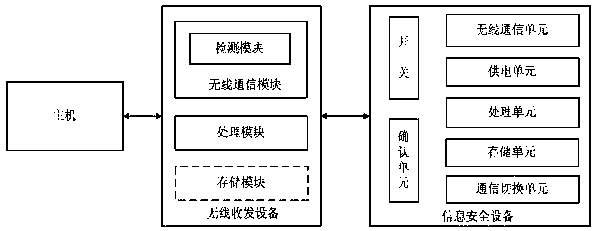
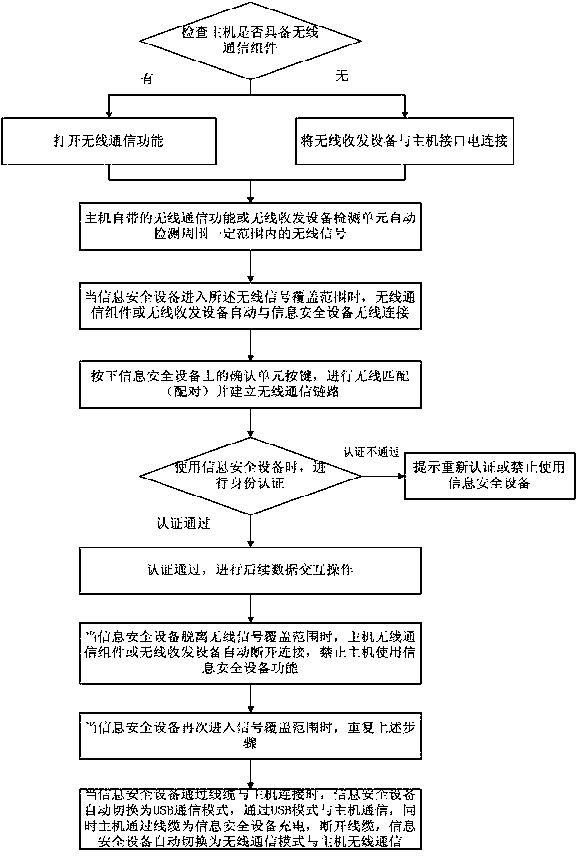
[0142] In this embodiment, the host is a Lenovo (ThinkPad) notebook computer with a wireless switch, the wireless communication is bluetooth, the information security device is a dongle, the wireless communication unit in the dongle is a bluetooth communication component, and the dongle switch is open by default. Both the lock confirmation unit and the switch are in the form of buttons. According to a specific embodiment of the present invention, the method for securely transmitting data through a wireless information security device includes specific steps:
[0143] 1. Turn on the wireless switch of the laptop and turn on the Bluetooth function;
[0144] 2. The Bluetooth component of the notebook automatically detects wireless signals within a certain range around;
[0145] 3. When the dongle enters the coverage area of the notebook Bluetooth signal, the notebook Bluetooth component automatically connects with the Bluetooth communication component inside the dongle;
[01...
specific Embodiment 2
[0152] This embodiment is similar to the operation steps of Embodiment 1, the difference is that the host in this embodiment is a computer without wireless communication components, the information security device is a dongle, the dongle has a built-in Bluetooth wireless communication unit, and the wireless transceiver device is similar in shape A USB receiver for a wireless mouse (hereinafter referred to as a USB transceiver), according to an embodiment of the present invention, the method steps of a wireless information security device include:
[0153] 1. Electrically connect the USB transceiver to the host interface;
[0154] 2. The detection module of the USB transceiver automatically detects wireless signals within a certain range around;
[0155] 3. When the dongle enters the wireless signal range, the USB transceiver is automatically connected to the Bluetooth wireless communication unit of the dongle;
[0156] 4. Perform wireless matching (pairing) through the confir...
specific Embodiment 3
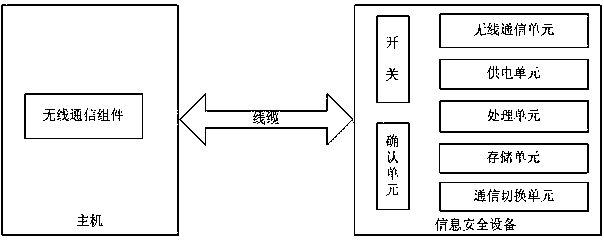
[0160] This embodiment is similar to Embodiments 1 and 2, the difference is that this embodiment uses a cable, and the steps of the wireless information security device method provided by this embodiment are:
[0161] 1. When the information security device performs data interaction with the host through wireless communication with the host's own wireless communication components or wireless transceiver equipment, the cable is electrically connected to the information security device and the host;
[0162] 2. The information security equipment communication switching unit automatically switches the wireless communication mode to the USB communication mode, and at the same time, the cable charges the information security equipment;
[0163] 3. When the cable is disconnected from the host, the information security device communication switching unit automatically switches the USB communication mode to the wireless communication mode, and the information security device and the ho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com