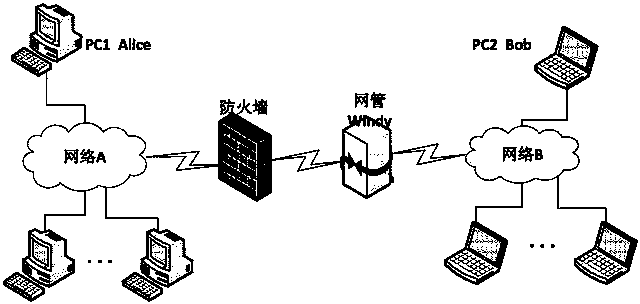
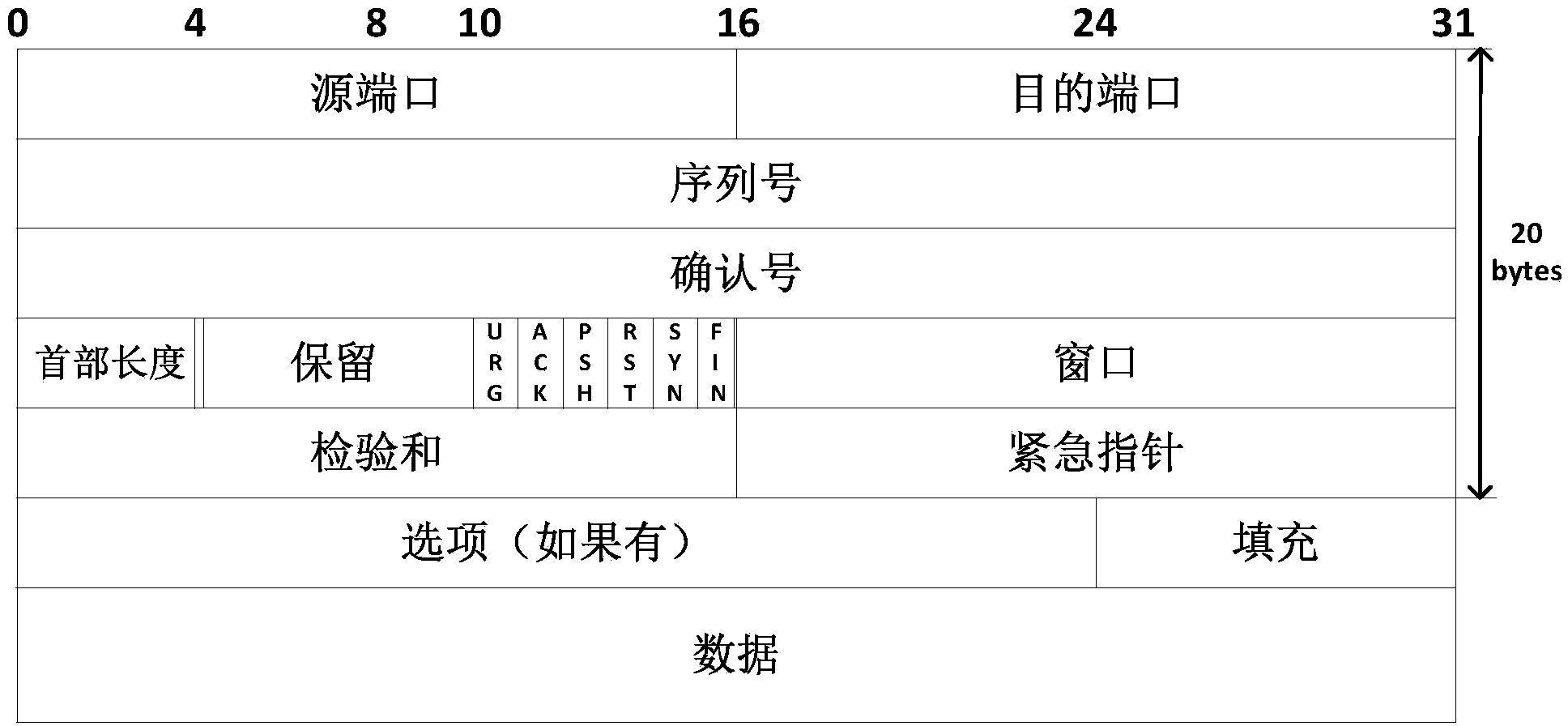
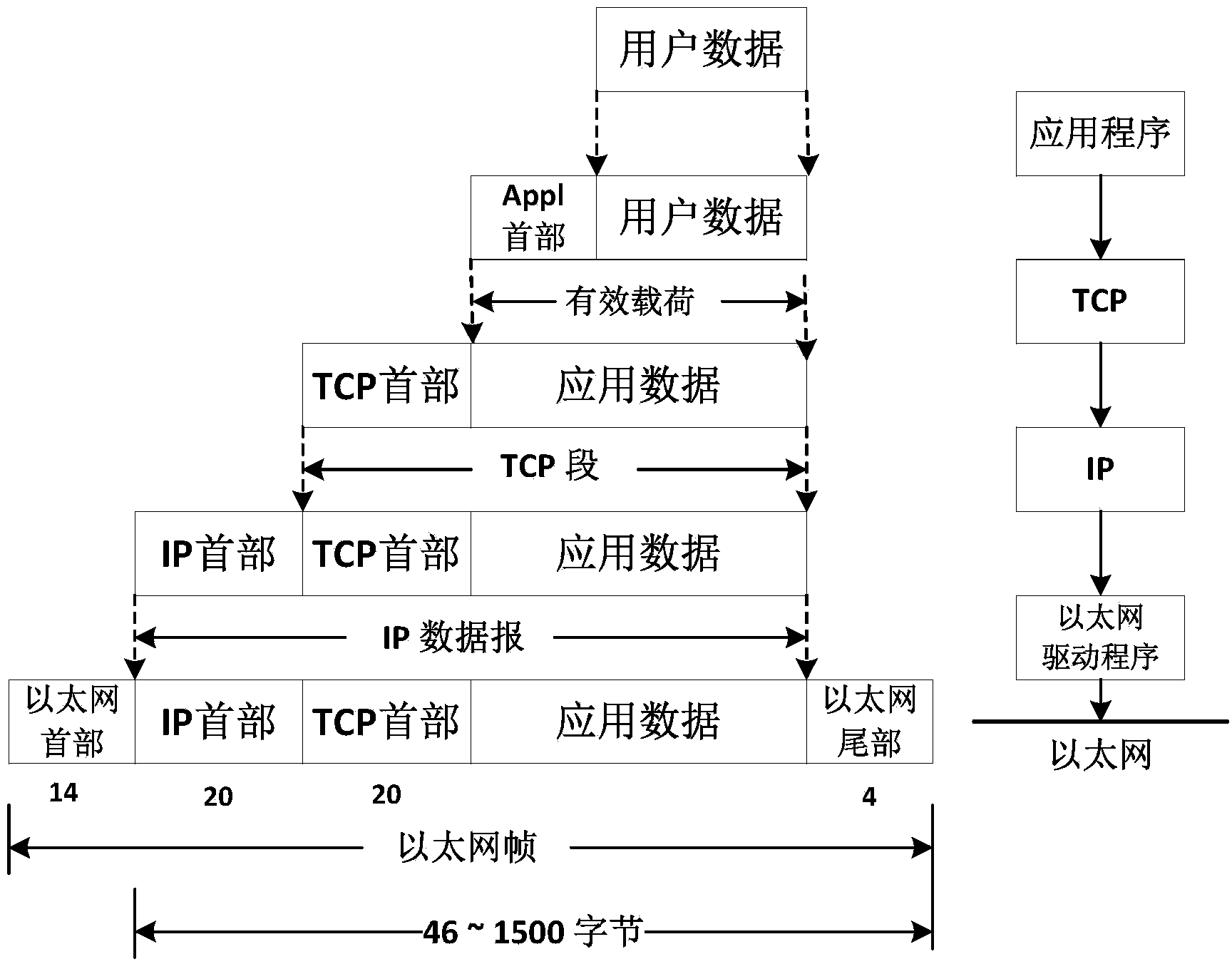
Two-way reliable covert channel based on TCP effective loads
A payload and hidden information technology, applied in the field of information security, can solve redundancy and other problems, achieve the effects of ensuring consistency, reducing embedding rate, and improving detection resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0043] attached image 3 It is a flow chart of the communication interaction between the sender and the receiver in the actual design. Specifically, it is implemented based on socket programming, and since the covert channel is designed based on TCP, a stream socket (SOCK_STREAM) is used to realize the software program of the sender and the receiver. The sender and the receiver adopt the active request method. First, the receiver creates a stream socket and binds the socket to a local address and port, and then sets the local socket to the listening mode. Accept the sender's connection request. The sender sends a connection request to the receiver after creating a local socket. The receiver receives the connection request and returns a new socket corresponding to this connection. The receiver and the sender communicate through this new socket. After the communication is over, the two parties disconnect according to the TCP four-wave process and close the socket.
[0044] a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com