USB (Universal Serial Bus) flash disk secure storage method based on virtual file system
A virtual file system and secure storage technology, which is applied in the field of U disk security storage with multi-level confidentiality mechanism, can solve the problems of lack of mobility, key leakage, encrypted file cracking, etc., and reduce the possibility of key leakage or cracking performance, improve safety, and protect safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
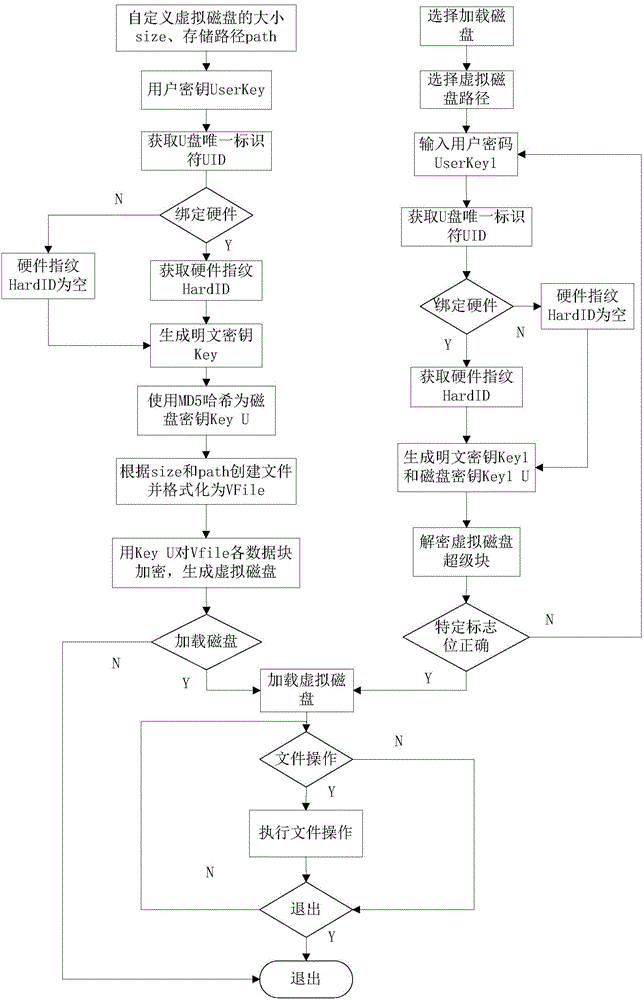
[0055] After the user obtains the encrypted USB flash drive, the process of using the client to open the virtual disk is as follows:
[0056] 1) Insert the U disk and open the disk management software;
[0057] 2) Select the loaded virtual disk;
[0058] 3) Enter the user key UserKey;
[0059] 4) Obtain the hardware fingerprint HardID bound to the virtual disk and the unique identifier UID of the U disk;
[0060] 5) Get the Key from "Key=UserKey+UID+HardID";
[0061] 6) Perform MD5 hash on the plaintext key Key to obtain the disk key Key_U;
[0062] 7) Traverse all the decryption algorithms in the encryption module, and use the generated disk key Key1_U to decrypt the super block of the virtual disk until the super block can be recognized by the virtual file system;
[0063] 8) If the super block cannot be recognized after all the decryption algorithms are tried, the user key is wrong and the key needs to be re-entered; otherwise, the user key is correct and the virtual di...
Embodiment 2
[0065] After the virtual disk is bound to the computer hardware, if you want to use it on other computers, the process of unbinding the computer hardware information is as follows:
[0066] 1) Insert the U disk and open the disk management software;
[0067] 2) Follow the steps in Example 1 to open the virtual disk;
[0068] 3) Choose to unbind the computer hardware;
[0069] 4) Obtain the unique identifier UID and user key UserKey of the U disk;
[0070] 5) Calculate the plaintext key Key1, Key1=UserKey+UID+HardID (HardID is empty);
[0071] 6) Perform MD5 hash on the plaintext key Key1 to obtain the disk key Key1_U;
[0072] 7) Decrypt the virtual disk data block with the old disk key Key_U, and re-encrypt the data block with the newly generated disk key Key1_U.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com