File redirection technology based virtualized security desktop
A secure desktop and redirection technology, applied in digital data protection, platform integrity maintenance, etc., can solve problems such as hidden dangers of computer data security, high architecture dependence, and complex operating system upgrade return on investment, etc., to ensure reliability, operation, etc. Safe, reliable and controllable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
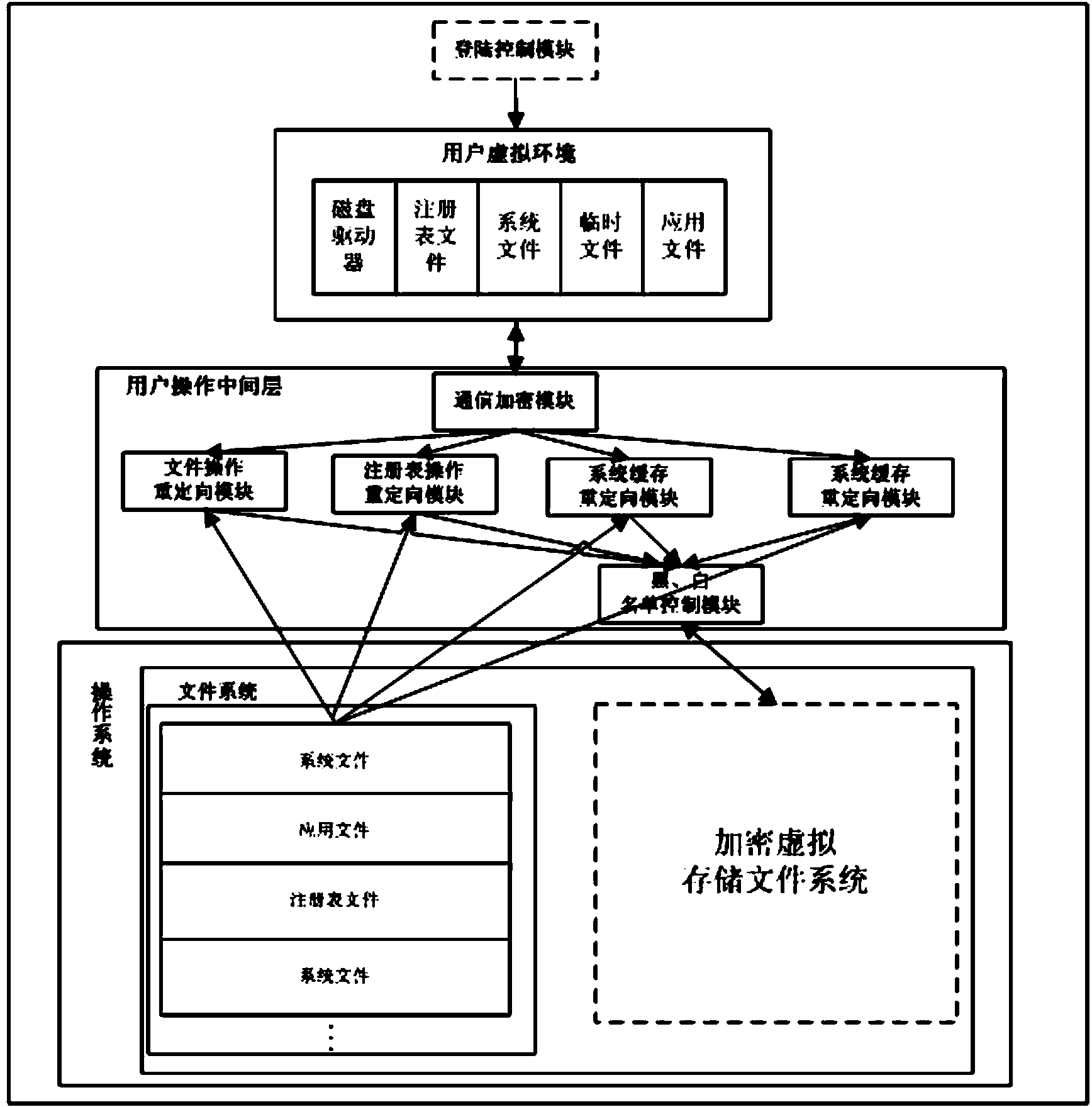
[0026] Virtualized secure desktop based on file redirection technology, such as figure 1 As shown, it includes three parts:
[0027] 1. Ensure the legitimacy of users using the secure desktop through the login control module:
[0028] The startup of the secure desktop system is tightly coupled with the host login control module, and the USBKEY+PIN dual authentication control mechanism is adopted to log in; only users registered and authorized by legal institutions can log in and start the virtual secure desktop, thereby ensuring that users who log in to the virtual desktop is a legitimate user. The basic implementation principle is as follows:
[0029] During the host login stage, the secure desktop system will extract the PIN code entered by the user when logging in, and then verify the validity of the authorization certificate in the USBKey device. Only users who have correctly entered the PIN code and are truly authorized are allowed to log in to the virtual security syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com