Commercial cipher algorithm based security access control system and implementation method thereof
A technology of commercial encryption algorithm and implementation method, which is applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems that the access control system is easy to be cracked and copied, and achieve high commercial security level, Conducive to safety, the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
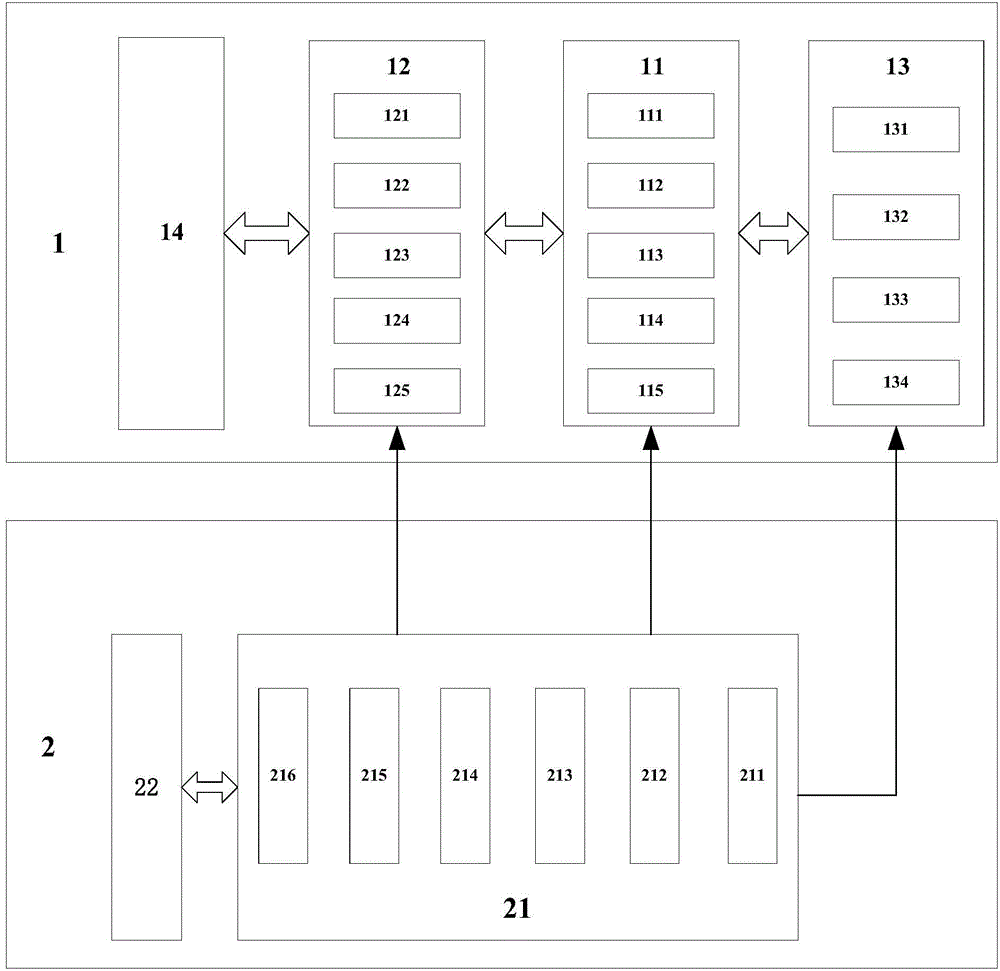
[0045] In order to ensure the safety and reliability of the access control system, the embodiment of the present invention provides a security access control system based on commercial cryptographic algorithms, see figure 1 , the secure access control system includes: an access control application system 1 and a key management and card issuing system 2 .
[0046] The access control application system 1 includes: a business secret security access control card reader 11 , a business secret security access control controller 12 , a business secret CPU card 13 and a business secret access control management software 14 .
[0047] The key management and card issuing system 2 includes: a business secret card issuer 21 and an access control key management system 22 .
[0048] The commercial security access control card reader 11 includes: a first antenna module 111 , a first radio frequency interface module 112 , a first main control chip 113 , a first SAM (secure access) module 114 ...
Embodiment 2
[0065] In order to solve the realization of the security access control system, the embodiment of the present invention provides a method for implementing a security access control system based on commercial cryptographic algorithms, see the following description for details:
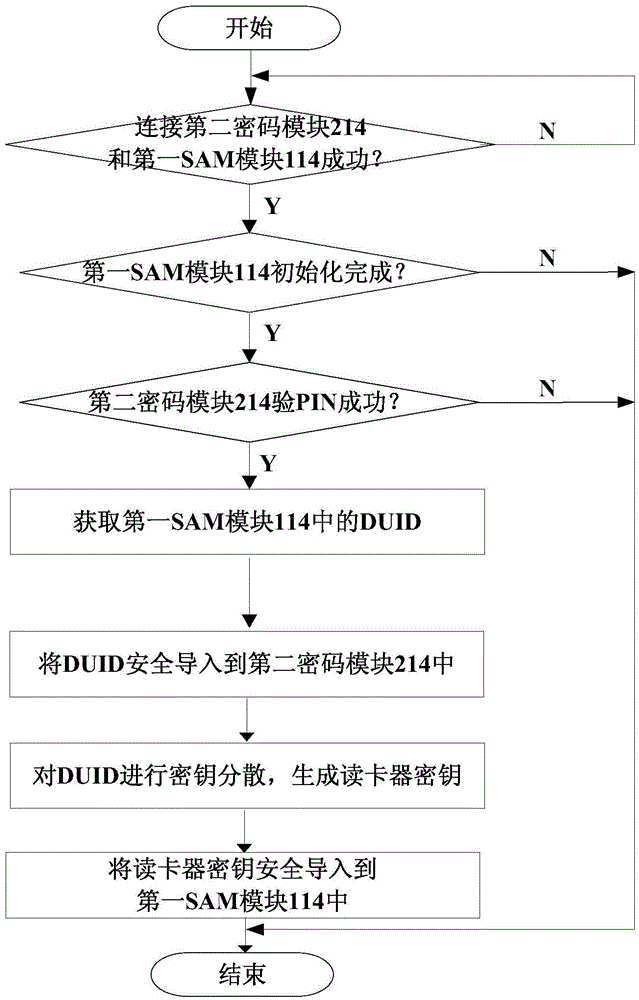
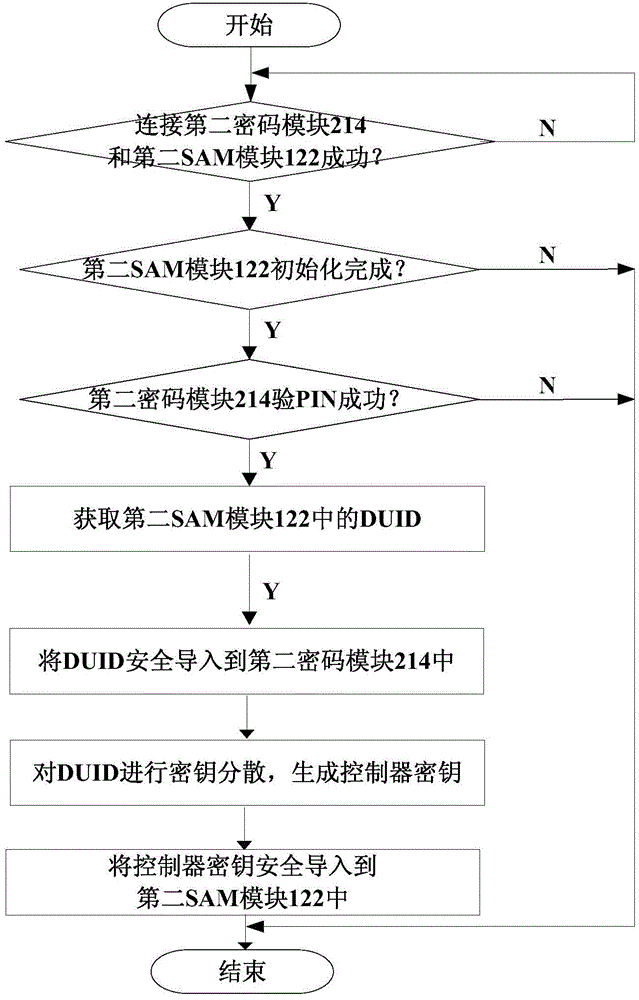
[0066] see figure 1 with figure 2 , the first SAM module 114 card issuing process in the commercial secret security access control card reader 11 is: the access control key management system 22 uses the commercial secret card issuer 21 to issue a card to the first SAM module 114 in the commercial secret security access control card reader 11 . When issuing a card, it is first necessary to verify the PIN code of the second password module 214 in the commercial secret card issuer 21. After the verification of the PIN code is successful, the commercial secret card issuer 21 obtains the PIN code from the first SAM module 114 in the commercial secret security access control card reader 11. Module identific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com