Network security defense system based on software-defined network and working method of network security defense system
A defense system and network security technology, applied in the field of network security, can solve the problems of SDN controller unable to respond, high hardware requirements, etc., to achieve the effect of improving high cohesion characteristics, improving detection efficiency, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
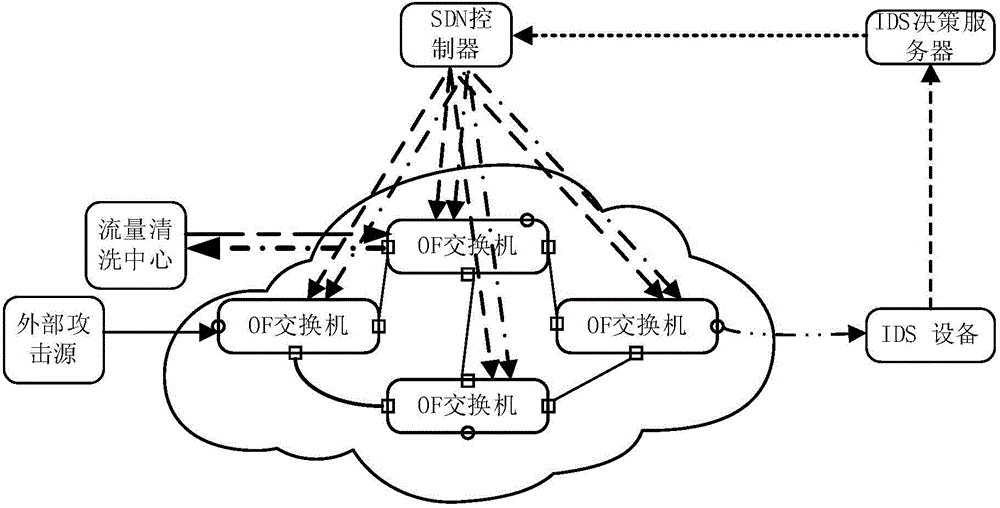
[0027] figure 1 A structural block diagram of the network security defense system of the present invention is shown.
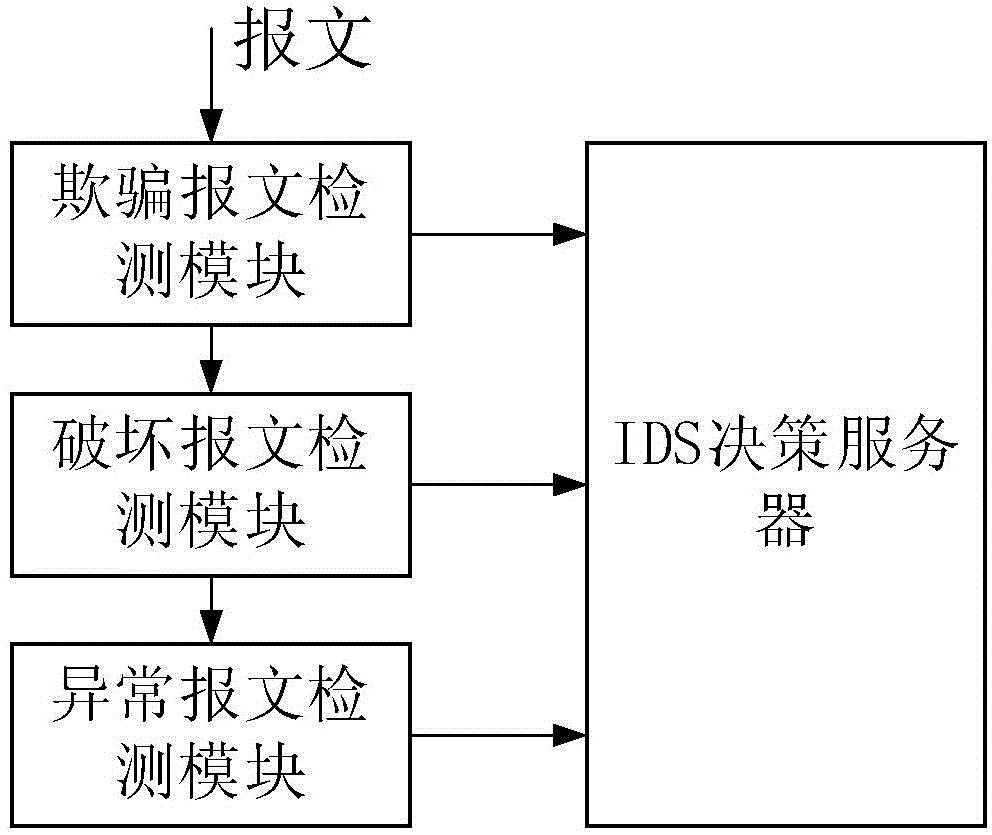
[0028] Such as figure 1As shown, a network security defense system includes: an SDN controller, an IDS decision server, and a distributed IDS device; When having the message of DDoS attack characteristic, report to IDS decision-making server (also can report to IDS decision-making server through SSL communication channel); Described IDS decision-making server formulates the processing corresponding to the message with DDoS attack characteristic according to reported information policy, and deliver the processing policy to the SDN controller for threat handling. The processing strategy will be described in the following examples.
[0029] Among them, the characteristics of DDoS attack are defined as: spoofing of link layer and Internet layer addresses, abnormal behavior of Internet layer and transport layer flag setting, and flood attack behavior of applicat...
Embodiment 2
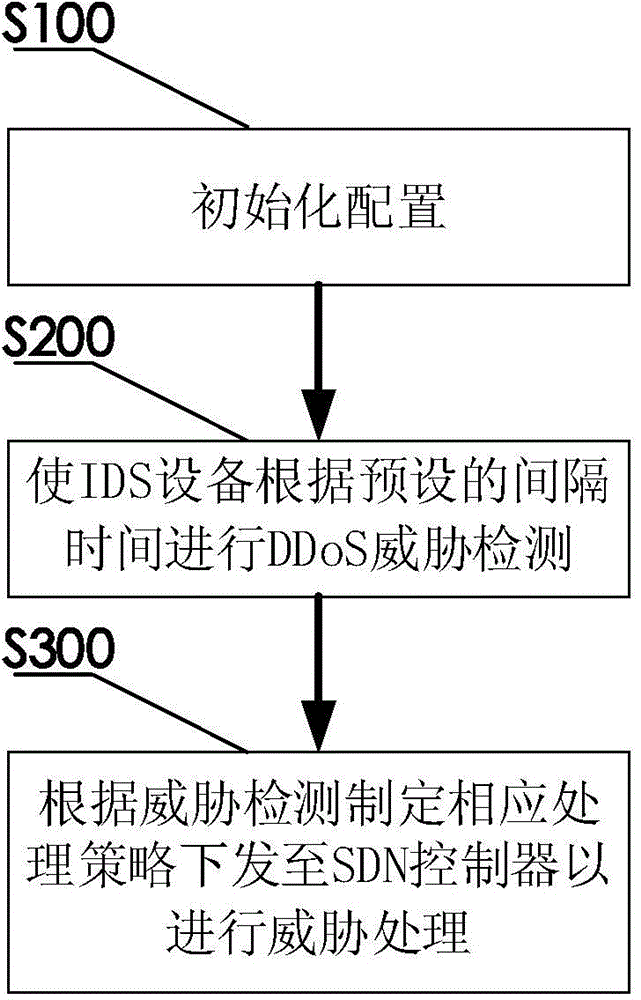
[0114] A working method of a network security defense system based on Embodiment 1, by separating random inspection from threat processing, effectively reduces the workload of the SDN controller and improves detection efficiency and data transmission rate.
[0115] image 3 A flow chart of the working method of the network security defense system of the present invention is shown.
[0116] Such as image 3 As shown, the working method of the network security defense system of the present invention comprises the following steps:
[0117] Step S100, initialize the configuration; Step S200, enable the IDS device to perform DDoS threat sampling according to the preset interval time; and Step S300, formulate corresponding processing policies according to the threat detection and send them to the SDN controller for threat processing.
[0118] The present invention realizes the random inspection of DDoS by means of random inspection, which greatly reduces the burden of the SDN cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com