A computer with data security function and its data encryption and hiding method
A data security and data encryption technology, which is applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve the problems of high cost, CPU resource occupation, unusability, etc., to achieve no CPU resource consumption, high data concealment, Maintain the effect of high-speed reading and writing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
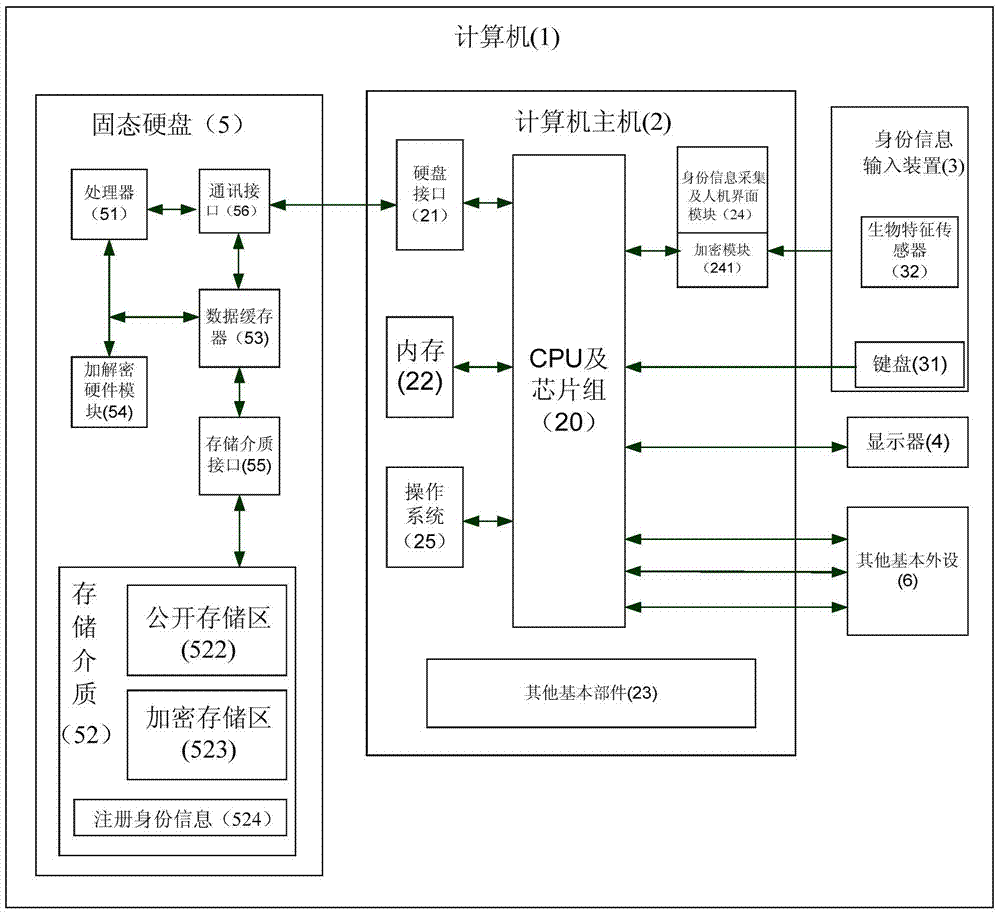
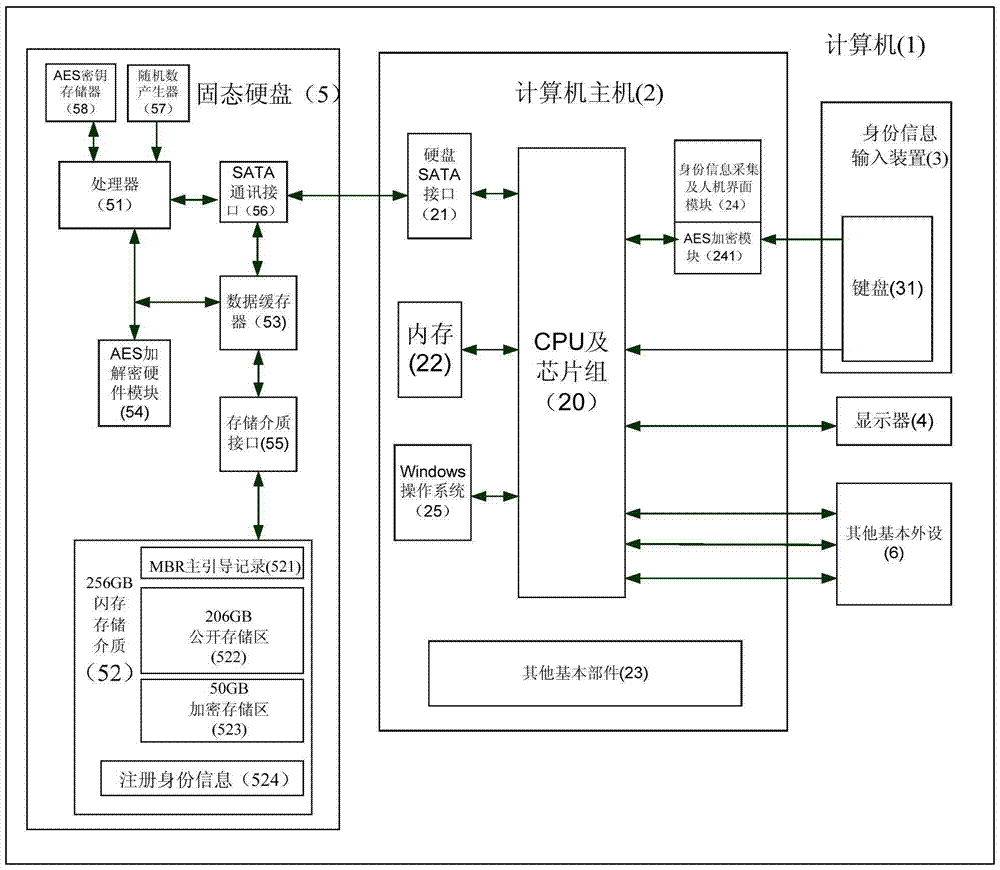
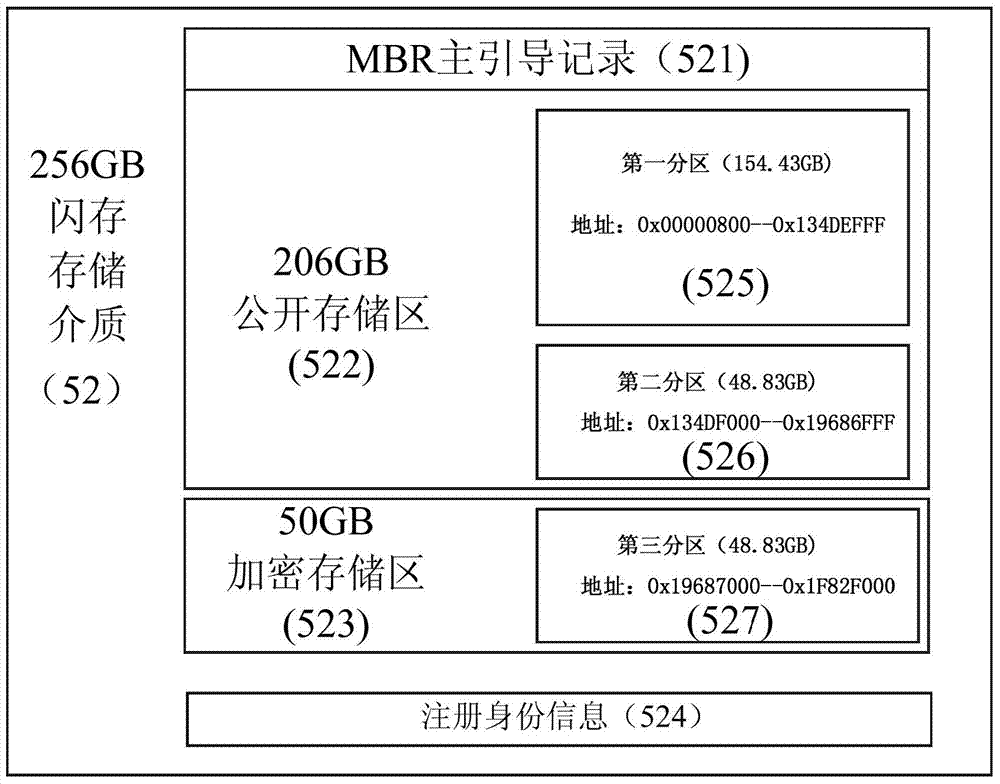
[0083] Figure 4 Shows a flow chart of a computer data encryption and hiding method of the present invention, now in conjunction with Figure 4 , figure 2 with image 3 , a preferred embodiment of the present invention is described as follows:
[0084] 1) Install and run the identity information collection and man-machine interface module (24) on the computer host (1), which comes with an AES encryption module (241);
[0085] 2) The user inputs the user's digital password through the keyboard (31) on the identity information collection and man-machine interface module (24), and uses the digital password as identity information;
[0086] 3) the identity information collection and man-machine interface module (24) converts the identity information input by the user into an ASCII code, and sends an identity verification information command to the processor (51) of the solid state disk (5);
[0087] 4) The processor (51) of the hard disk obtains a temporary random number by t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com