Image encryption method based on adversarial nerve cryptography and SHA control chaos
An encryption method and cryptography technology, applied in the field of image encryption based on anti-neural cryptography and SHA control chaos, to achieve the effect of meeting encryption security, high sensitivity, and resisting plaintext and chosen plaintext attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to better explain the present invention and facilitate understanding, the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
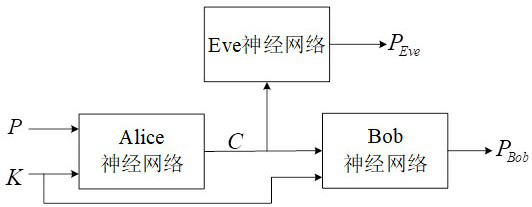
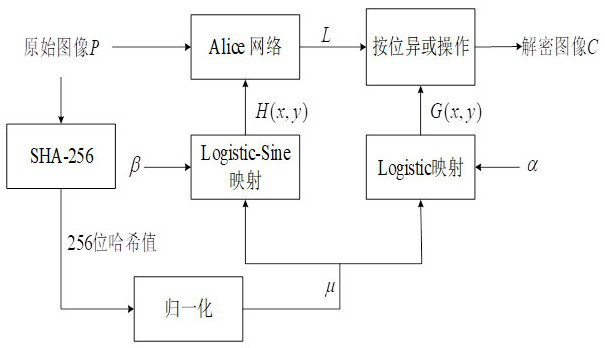
[0050] Such as figure 1 As shown, in terms of security, the ANC system designed by the present invention using the classical method involves three parts: Alice, Bob and Eve. Usually, Alice and Bob share a secret key K and confidentially transmit the plaintext P, Eve, as an attacker, wants to eavesdrop on the communication between Alice and Bob, and tries to obtain information about P through the ciphertext C, P Bob and P Eve The output of is computed by Bob and Eve respectively.
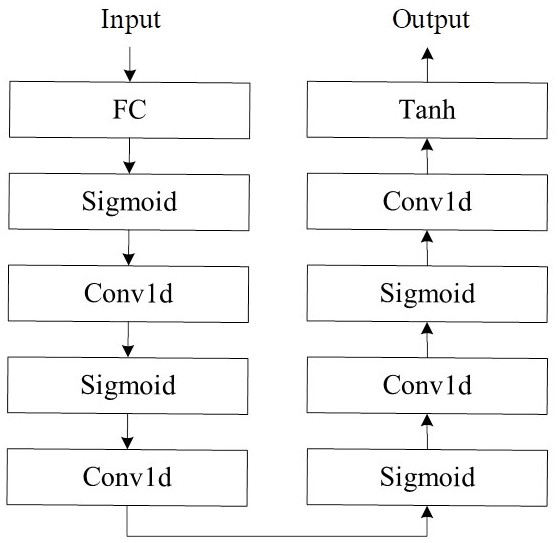
[0051] In the system framework of ANC, the network composed of Alice and Bob neural network is regarded as the generator in GAN, and the Eve neural network is regarded as the discriminator in GAN; the encryption process is mainly performed by Alice network, while the Bob network uses In the dec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com