Method and device for detecting memory access overflow
A memory access and detection model technology, applied in the field of computer compilation, can solve the problems of high false negatives and false positives, inability to handle recursion, etc., to reduce false negatives and false positives, and reduce the cost of space and time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
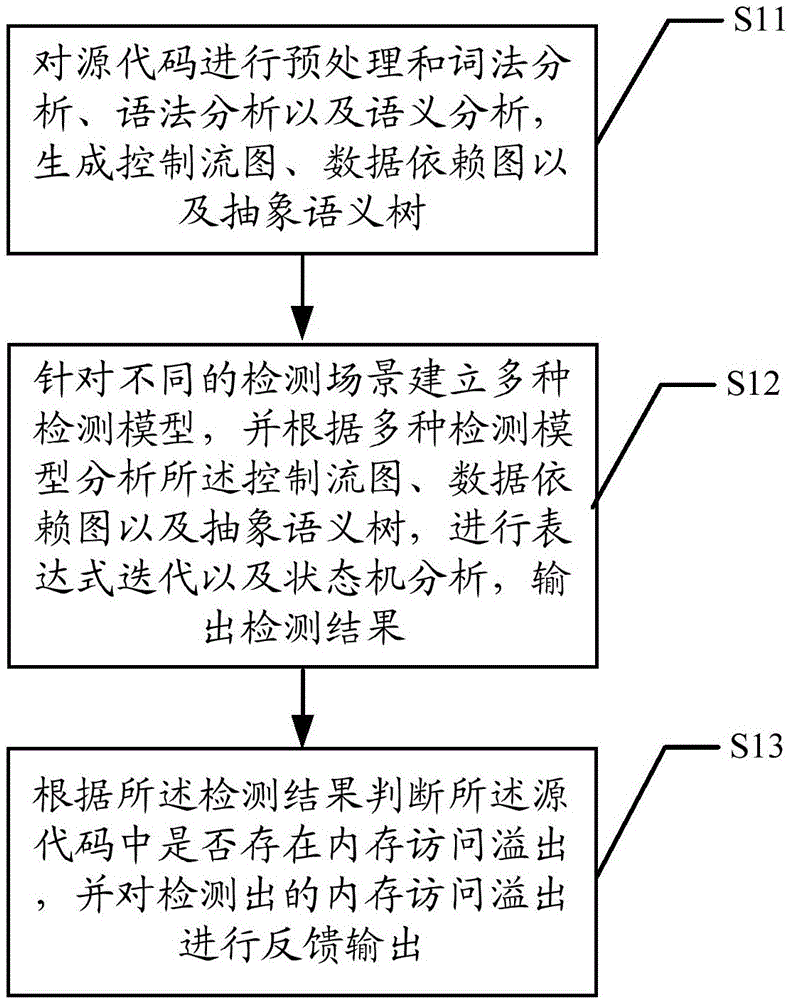
[0048] Explanation of related terms:
[0049] Memory access overflow (Buffer Overflow) means that due to the program's write operation on a memory object, the system mistakenly changes another memory object;
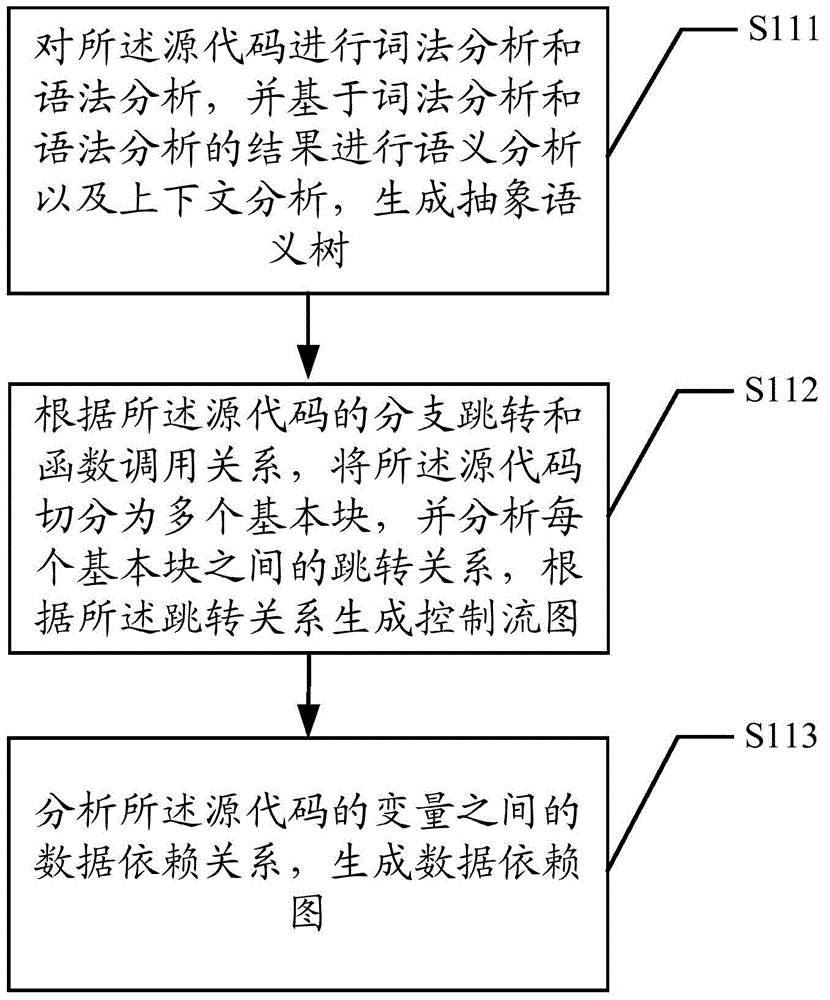
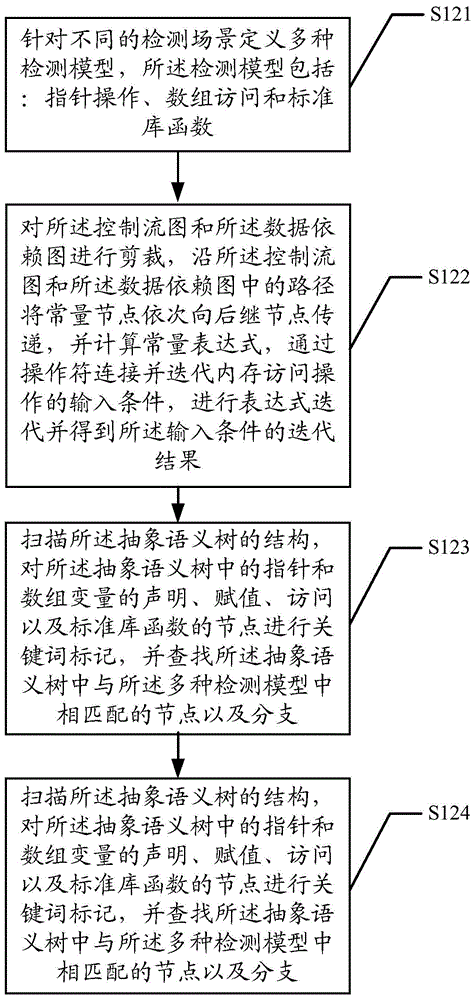
[0050] A control flow graph (CFG) is an abstract data structure used in compilers. It is an abstract representation of a procedure or program, maintained internally by the compiler. Each node in the control flow graph represents a basic block, ie, a basic block without any jumps or jump targets; jump targets start with a block, and end with a block. Each directed edge in the control flow graph is used to represent the jump direction in the control flow, or the jump relationship between basic blocks.
[0051] The data dependency graph (data dependency) refers to the data constraint relationship between the statements. If the two operations do not occupy the same variable, or they only read the same variable for continuous reading and writing, then the execution results an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com