A Network Reconfiguration Method of Power Distribution System Based on Security Domain
A technology for power distribution system and network reconfiguration, applied in AC network circuits, information technology support systems, genetic models, etc. The effect of improving calculation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
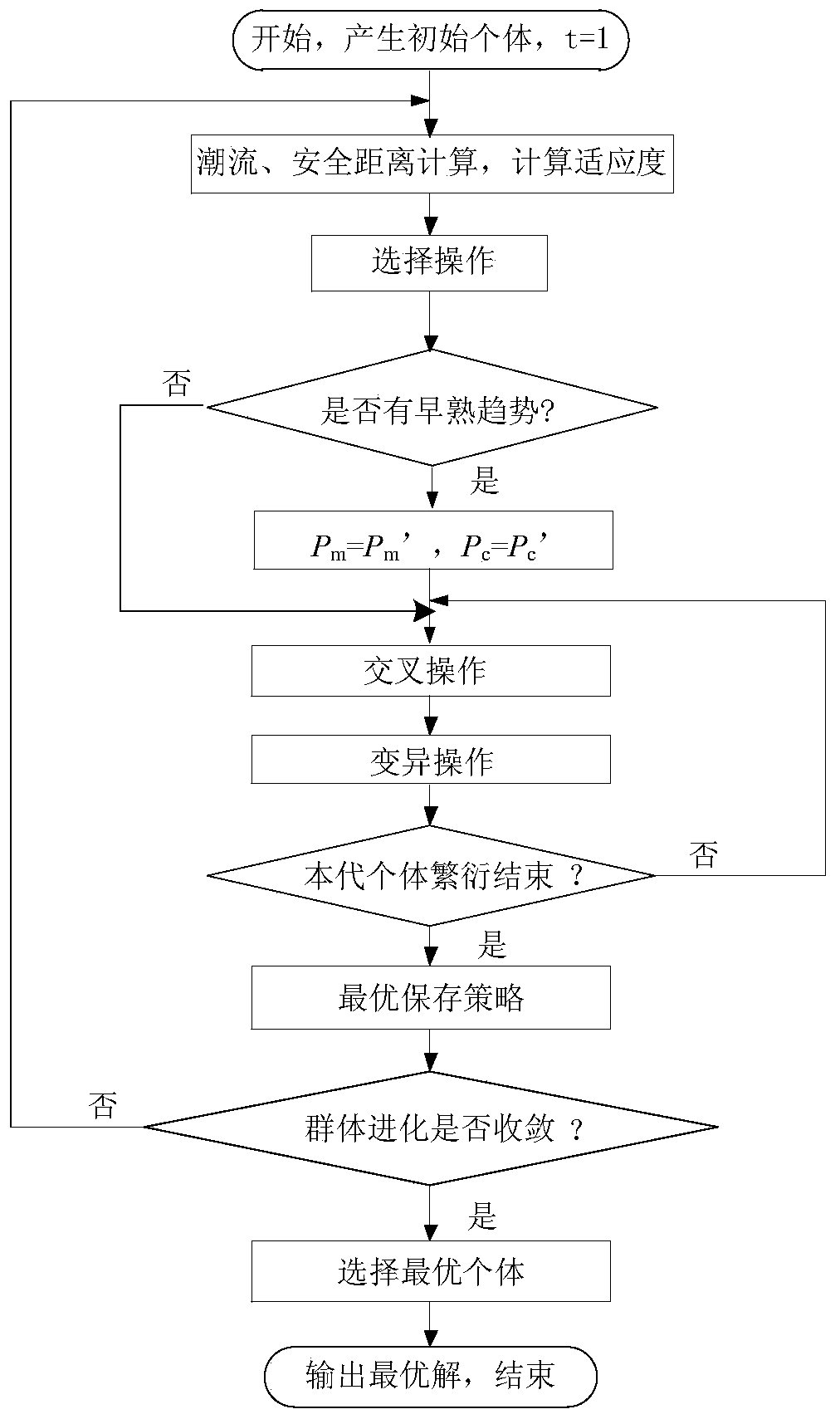
[0031] A security domain-based power distribution system network reconfiguration method, the power distribution system network reconfiguration method includes the following steps:
[0032] 101: Construct the security index of the distribution system security domain according to the distribution system security domain and the security boundary equation;
[0033] 102: Obtain a network reconfiguration model according to the security index of the security domain of the power distribution system, reconstruct the distribution system network through the network reconfiguration model, and obtain the final switching state of the entire network.
[0034] Among them, the steps to construct the security index of the distribution system security domain according to the distribution system security domain and the security boundary equation are as follows:
[0035] Obtain the safety distance of a single feeder;
[0036] The average feeder safety distance and the minimum feeder safety distan...
Embodiment 2
[0044] The following combines specific test data and calculation formulas to describe in detail the operation process of a distribution system network reconfiguration method based on security domains. See the following description for details:
[0045] 201: Construct the distribution system safety domain and its safety boundary equation;
[0046] The distribution system safety domain DSSR is defined as satisfying the N-1 safe operation criterion and various other operating constraints (for example: Kirchhoff’s law constraints, power flow equation constraints, node voltage amplitude constraints or radiation structure operation constraints, when specifically implemented, The embodiment of the present invention does not limit this) the set of all working points W. Among them, the working point W is an n-dimensional vector composed of all load nodes of the distribution system, that is, the security domain of the distribution system is:
[0047]
[0048] In formula (1), Ω DSSR...
Embodiment 3
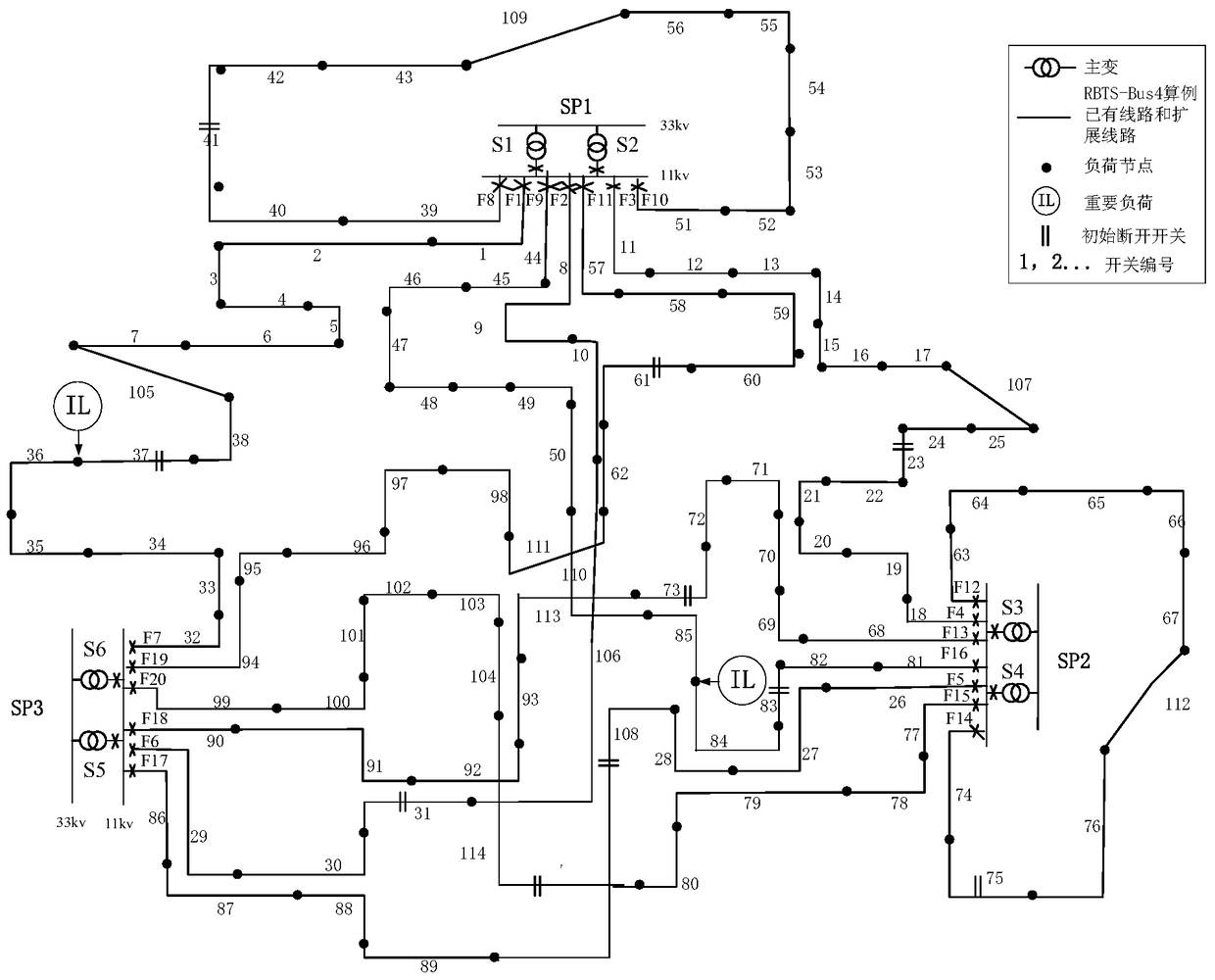
[0095] A distribution network calculation example is used below to illustrate the embodiment of the present invention. The modified IEEE RBTSBUS4 is used in the calculation example: 1) the number of feeders and the scale of feeder connections are increased; 2) the load is slightly increased, reflecting the situation that the power grid is approaching the N-1 safety boundary under high load operation; 3) the capacity of feeders and main transformers is adjusted , so that the safety of N-1 is the common constraint of the feeder and the main transformer; 4) The feeder F7 and F16 contain important loads and require a larger safety margin. The length of each line is 0.5km.
[0096] Table 1 Main Transformer Data
[0097]
[0098] Table 2 Feeder data
[0099]
[0100] 1) Safety boundary calculation;
[0101] The safety boundary equation of the example is calculated as follows.
[0102]
[0103] 2) Safe distance vector SD min set up
[0104] Due to SD min is a quantitati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com