Circuit safety DFT (design for testability) method for accelerating hardware Trojan trigger and hardware Trojan detection method
A hardware Trojan and design method technology, applied in electronic circuit testing and other directions, can solve problems such as difficult detection, and achieve the effect of speeding up the triggering speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
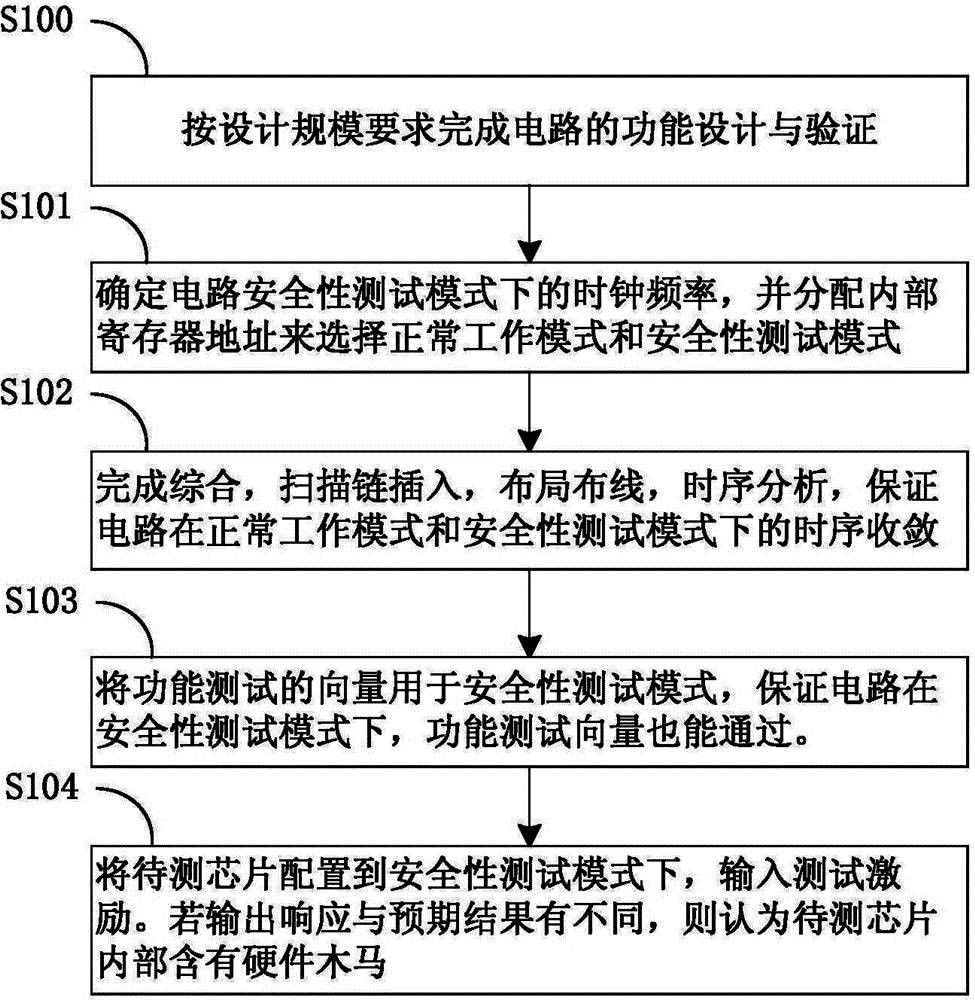
[0023] The present invention will be further described below in conjunction with specific drawings and embodiments.
[0024] Design for Testability (DFT, Design for Testability) is a very important part of integrated circuit design. It is mainly used to detect whether there are manufacturing defects in the chip during the manufacturing process, which affects the function of the circuit and the yield. And people have developed a variety of DFT techniques to more effectively detect defects in chip manufacturing.
[0025] However, for the security detection of whether there is a hardware Trojan in the integrated circuit, there is no general and standard process such as DFT at present.
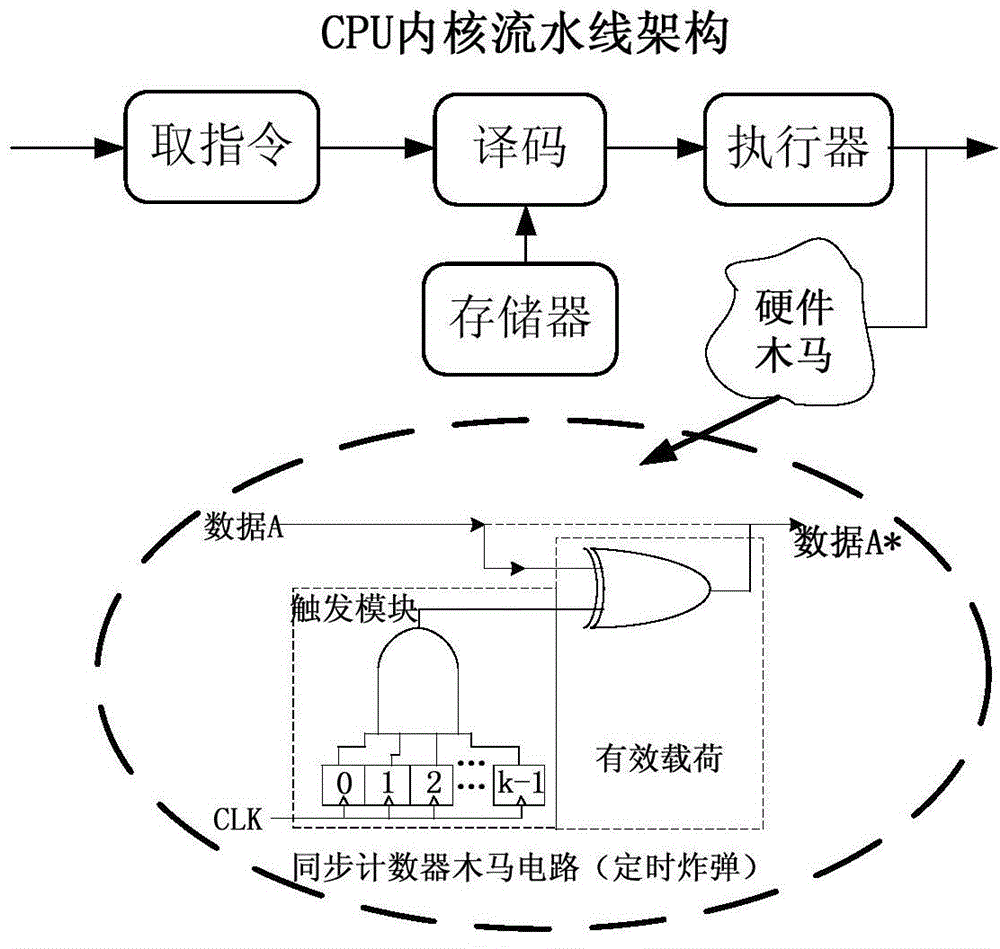
[0026] The current technology for hardware Trojan detection, such as logic testing, requires the hardware Trojan inside the circuit to trigger and change the logic value of the internal nodes of the circuit, so that it can be judged whether there is a hardware Trojan inside the circuit by observin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com