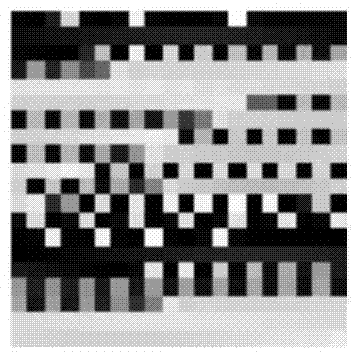
A Method for Constructing Image Password Based on Neuron Chaotic Response Coding
An image password and construction method technology, applied in electrical components, digital transmission systems, transmission systems, etc., can solve the problems of users being unable to verify the identity of the system, poor security, and easy to leak, so as to reduce the risk of interception and not easy to leak. , high-complexity effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
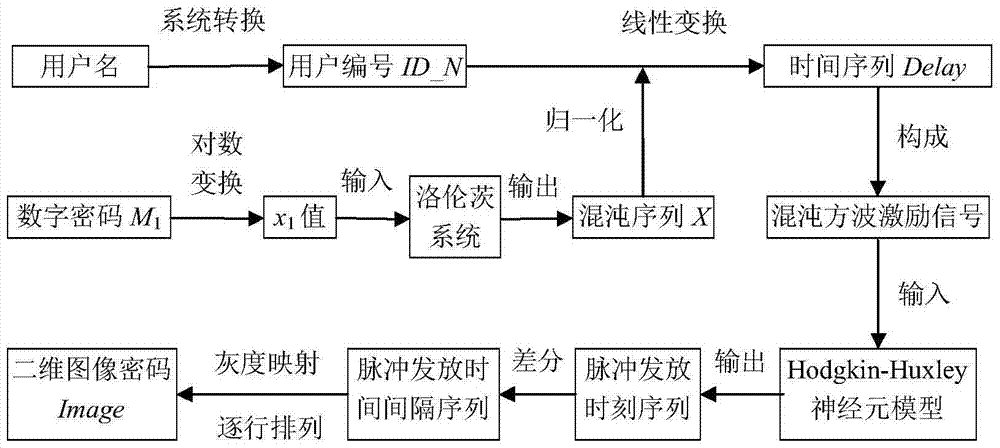
[0031] combined with figure 1 , the specific implementation steps of the present invention are:
[0032] Step (1) The user first enters the user name that has been authenticated and registered by the system, and the system will automatically convert the user name to the corresponding user number ID_N. digit password M 1 ; m is a positive integer;
[0033] Step (2) The system converts the digital password M entered by the user into 1 Perform logarithmic transformation, as shown in formula (1).
[0034]
[0035] will transform the result x 1 As the initial value of the position in the x direction of the three-dimensional space of the Lorenz system, other parameters of the Lorenz system and the initial values of the y and z directions are automatically generated by the identity authentication system, and the Lorenz system is shown in formula (2).
[0036]
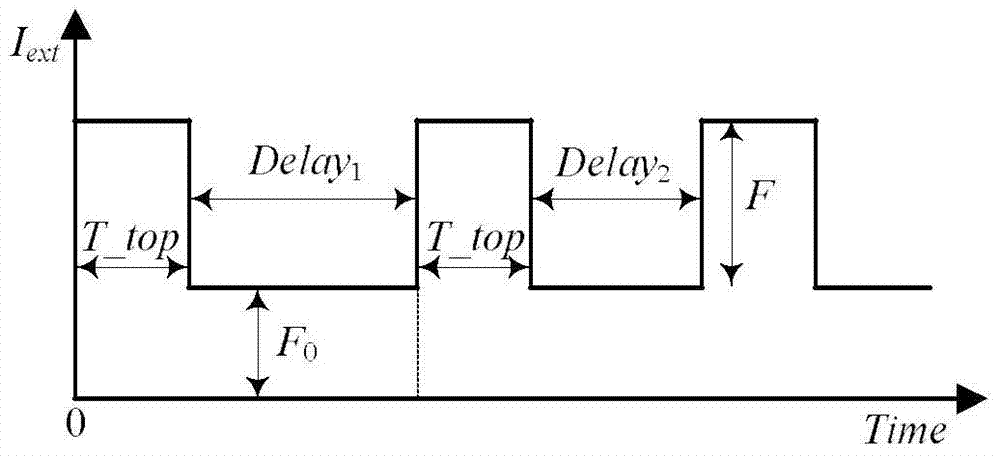
[0037] In this implementation example, a=10, b=28, c=8 / 3, the initial value of y is equal to 2, and the initial...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com