Precaution method for Android malicious application program based on code behavior similarity matching
A malicious application and similarity matching technology, which is applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as false positives and false positives, low analysis code coverage, detection accuracy and practicability, etc. Achieve the effect of improving detection effect, reducing pressure and optimizing configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The specific implementation of the present invention will be described in detail below with reference to the accompanying drawings. It should be noted that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
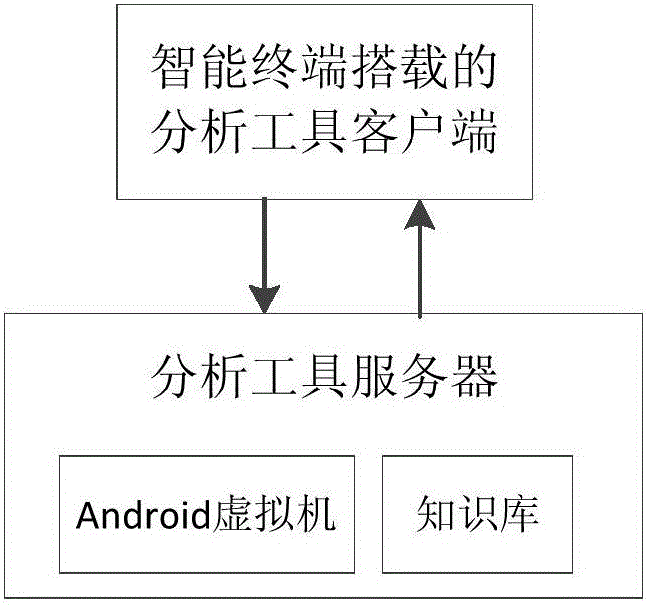
[0038] The structure diagram of the present invention is as follows figure 1 As shown, the architecture of the present invention is mainly divided into two parts: the analysis tool client and the analysis tool server carried by the smart terminal. Here, a light client and heavy server system design is adopted. The client is essentially an Android application, which is responsible for lightweight information extraction, and the server is responsible for heavy data analysis. The server side is composed of knowledge database, Android virtual machine and analysis software. This architecture is suitable for the reality of resource constraints such as power, computing, and storage of smart termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com