Key generation method capable of ensuring security of wireless communication
A key generation and wireless communication technology, applied in key distribution, can solve problems such as solution failure, channel noise interference asymmetry, high bit mismatch rate, etc., to achieve the effect of ensuring communication security, reducing bit mismatch rate, and ensuring efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
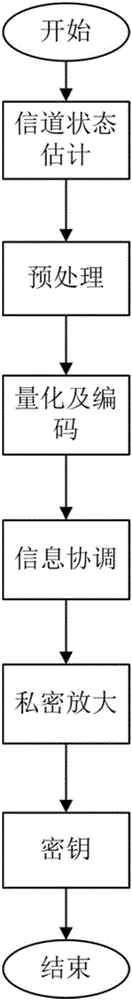
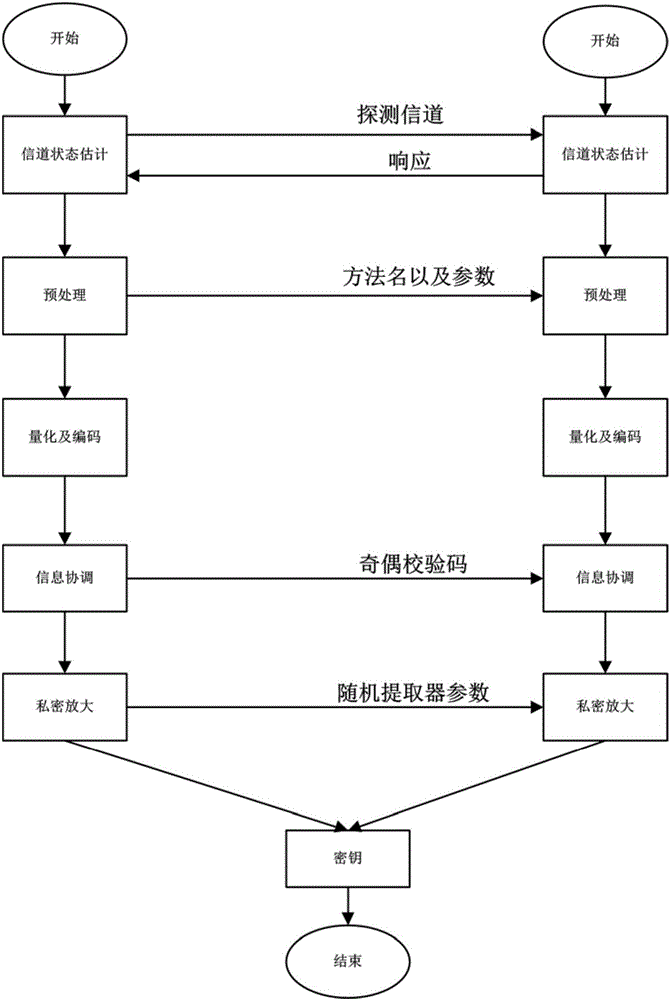
[0036] The preferred embodiments of the present invention will be specifically described below in conjunction with the accompanying drawings. The inventive concepts provided by the present invention can be implemented in a wide variety of specific contexts. The specific embodiments discussed are merely illustrative of implementations of the invention, and do not limit the scope of the invention.
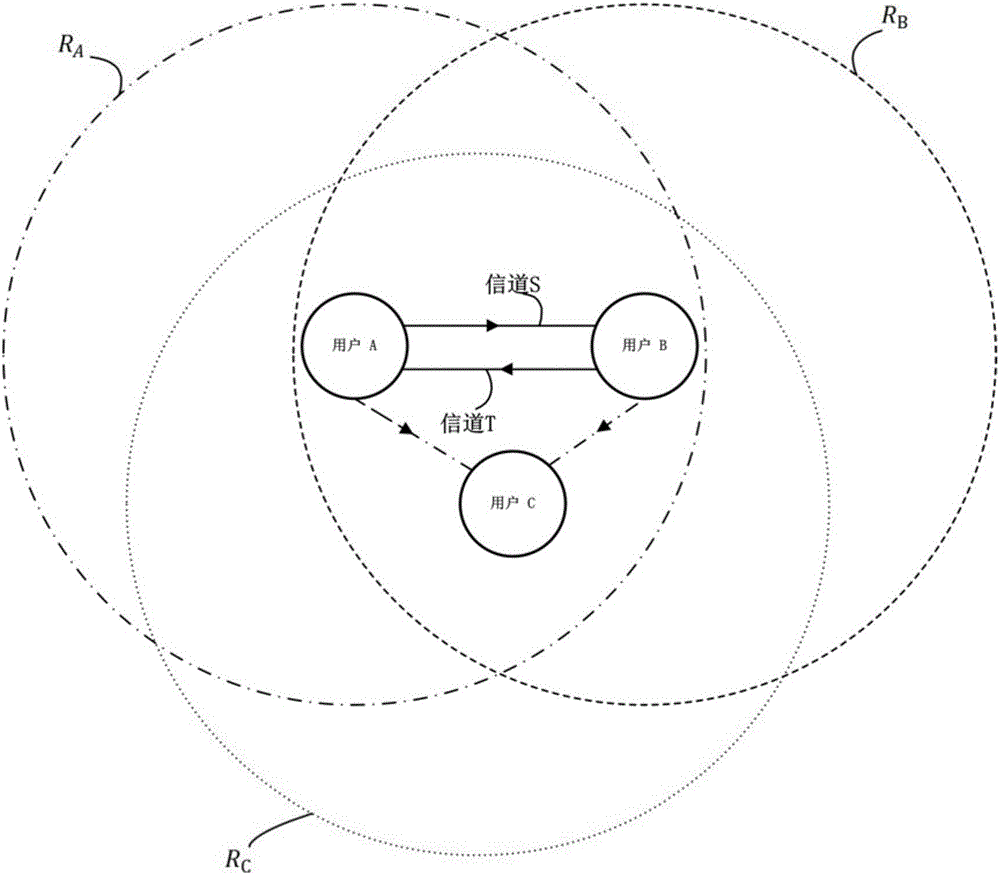
[0037] figure 1 A typical wireless communication system is shown. Consider the system as a time-division half-duplex system where there are two users A and B. Combined with the specific environment, consider the channel asymmetry between users. Therefore, channel S is between user A and user B, and channel T is between user B and user A. The communication radius of user A is R A , the communication radius of user B is R B . In addition, there is a communication radius R C User C. The communication radius of the three users can be different, but it must be ensured that all us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com