A security verification method and device based on NFC identification
A security verification and to-be-verified technology, applied in the direction of digital data authentication, etc., can solve the problem of easy copying or fraud, and achieve the effect of being suitable for large-scale promotion, shortening verification time, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
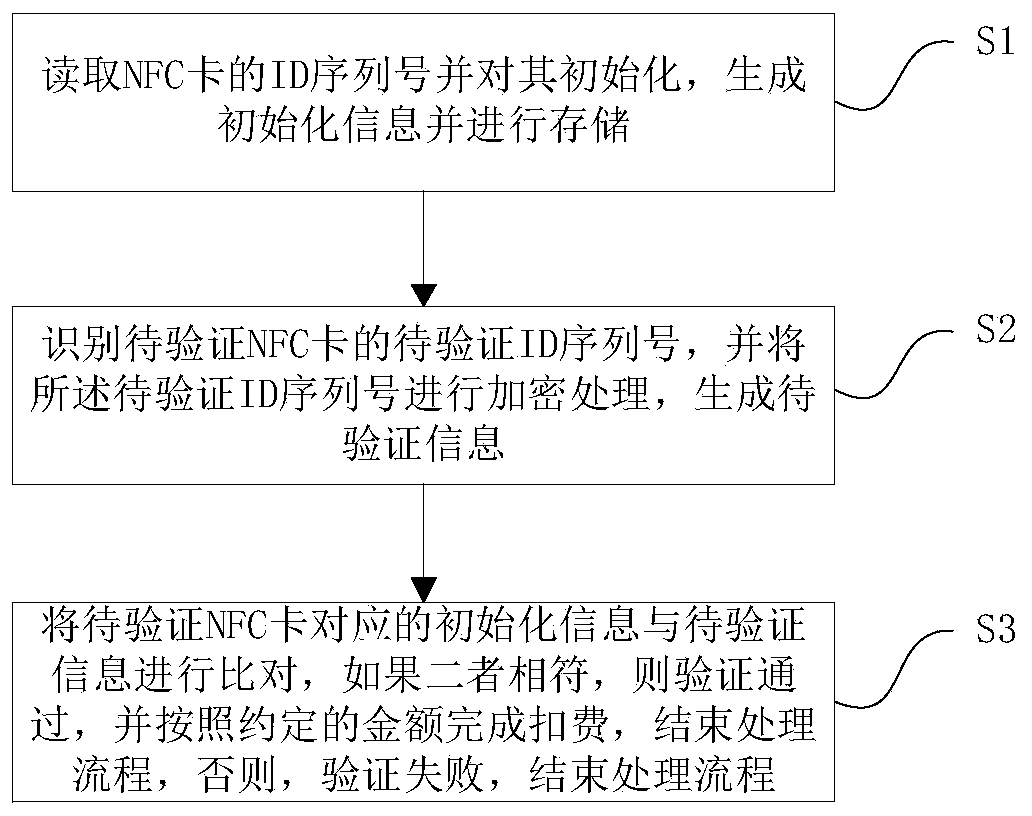
[0019] Embodiment 1, a schematic flow chart of a safety verification method based on NFC identification, which will be combined below figure 1 A schematic flow chart of a security verification method based on NFC identification in this embodiment is introduced in detail.
[0020] Such as figure 1 As shown, a schematic flow chart of a security verification method based on NFC identification, including the following steps:
[0021] Step 1: Read the ID serial number of the NFC card and initialize it, generate initialization information and store it;
[0022] Step 2: identifying the ID serial number to be verified of the NFC card to be verified, and encrypting the ID serial number to be verified to generate information to be verified;
[0023] Step 3: Compare the initialization information corresponding to the NFC card to be verified with the information to be verified. If the two match, the verification will pass, and the deduction will be completed according to the agreed amou...
Embodiment 2
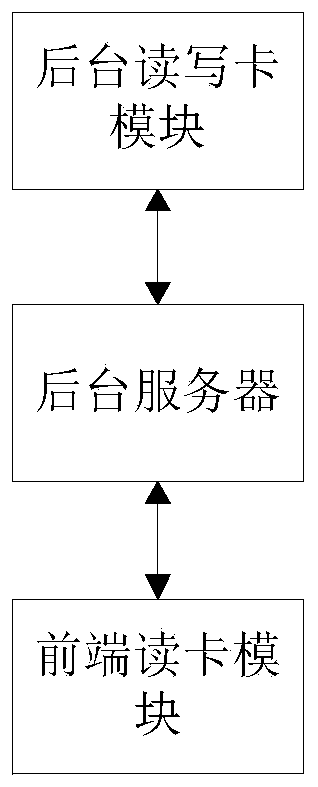
[0046] Embodiment 2, a schematic structural diagram of a safety verification device based on NFC identification, which will be combined below figure 2 A schematic structural diagram of an NFC identification-based security verification device in this embodiment is introduced in detail.
[0047] Such as figure 2 As shown, a structural diagram of a security verification device based on NFC identification, including a card reading and writing module, a front-end card reading module and a background server.
[0048] Wherein, the background card reading and writing module is used to read the ID serial number of the NFC card and initialize it, generate initialization information and send it to the background server for storage; the front-end card reading module is used to identify the ID of the NFC card to be verified The ID serial number to be verified, and the ID serial number to be verified is encrypted, and the information to be verified is generated and sent to the background...
Embodiment 3
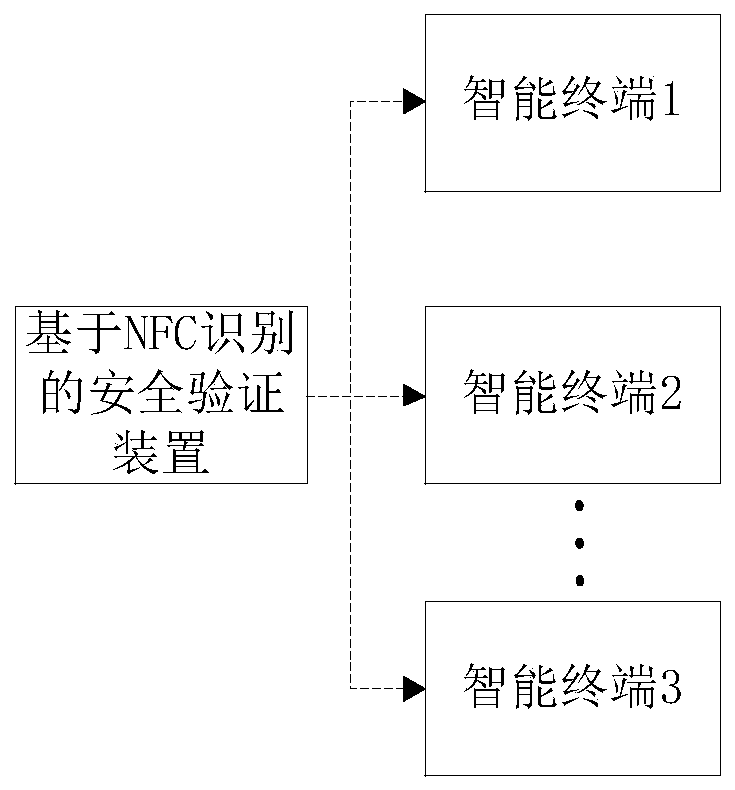
[0062] Embodiment three, a schematic structural diagram of a safety verification system based on NFC identification, which will be combined below image 3 A schematic structural diagram of an NFC identification-based security verification system in this embodiment is introduced in detail.
[0063] Such as image 3 As shown, a schematic structural diagram of an NFC-based security verification system includes at least one smart terminal and the NFC-based security verification device, and the smart terminal is wirelessly connected to the background server.
[0064] A security verification system based on NFC identification of the present invention can directly read the ID serial number of the NFC card through the intelligent terminal, and complete the communication of the NFC card through the communication between the intelligent terminal and the background server. NFC card payment can be completed anytime and anywhere, which is convenient, fast, safe and efficient, and is very ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com