Method for detecting DDoS (Distributed Denial of Service) attack in big data environment
An attack detection and big data technology, applied in the network field, can solve the problems that cannot meet the actual needs of high bandwidth and consume a lot of time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be further elaborated below by describing a preferred specific embodiment in detail in conjunction with the accompanying drawings.
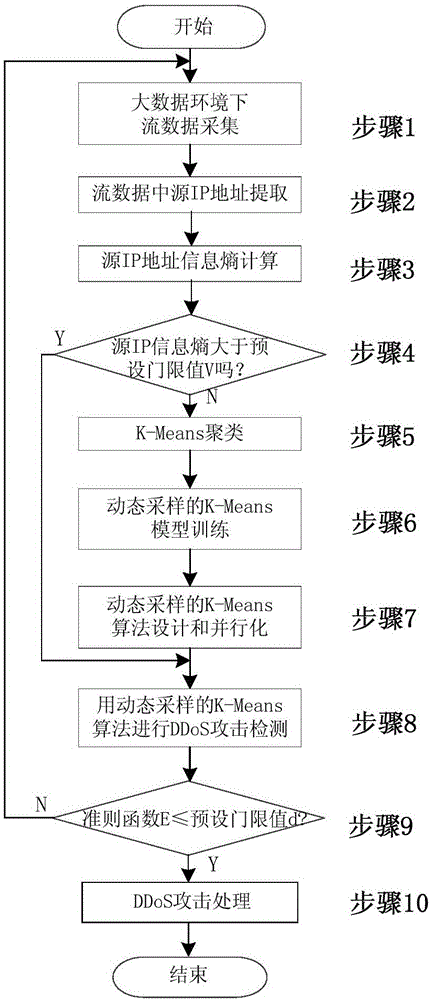
[0069] Such as figure 1 As shown, a DDoS attack detection method in a big data environment, the method includes the following steps:
[0070] S1, collecting various streaming data in a big data environment, that is, collecting various streaming data from a big data application system; An application system of several PBs; the users mentioned include registered users and non-registered users;
[0071] The various flow data include the data flow from the proxy server, the data flow arriving at the system through the firewall, and various POP data flows, etc.;
[0072] S2, extracting the source IP address from various flow data collected;
[0073] S3, calculating the information entropy of the source IP address;
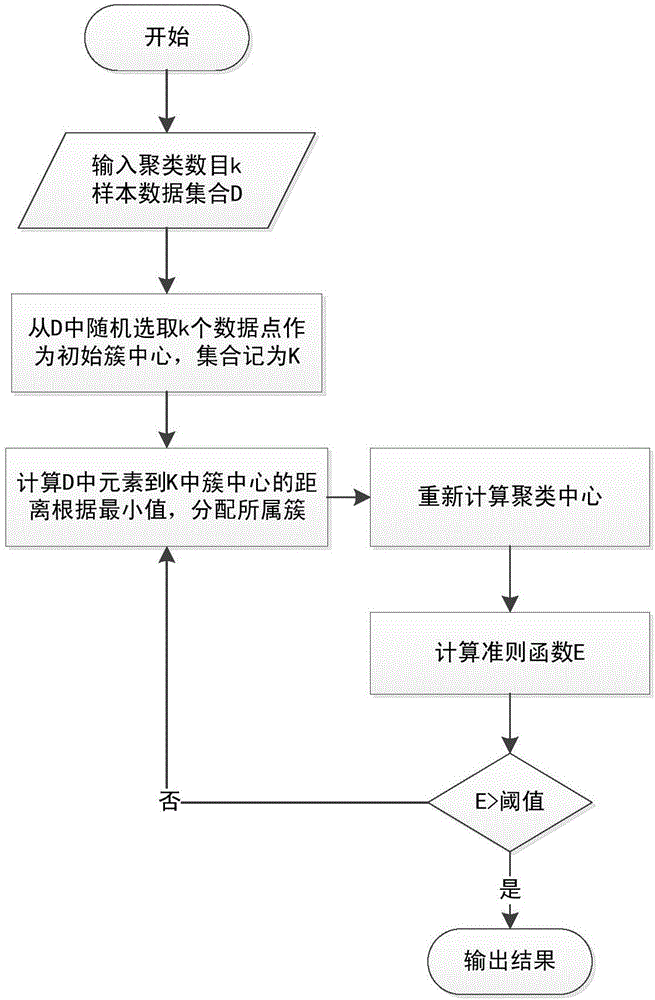
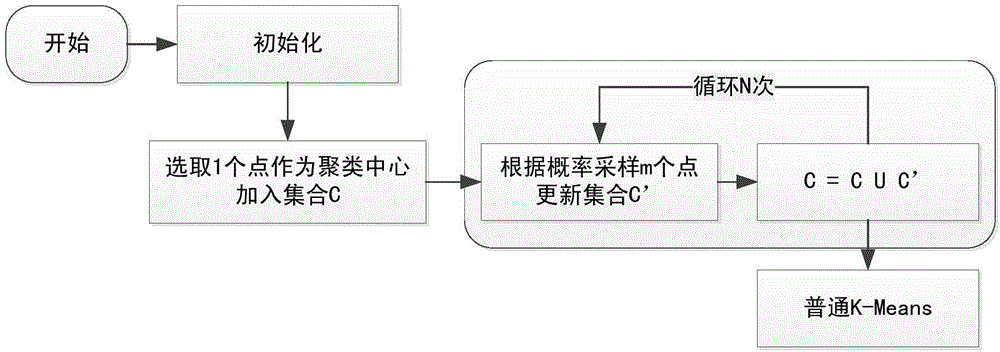
[0074] S4, determine whether the information entropy of the source IP address is greater than the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com