Secure mobile terminal electronic authentication method and system
An electronic authentication system and mobile terminal technology, which is applied in the field of secure mobile terminal electronic authentication and systems, can solve the problems of transaction data tampering by Trojan horses, high cost, and inconvenience for users to carry around, so as to improve transaction security, reduce production costs, The effect of guaranteeing uniqueness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
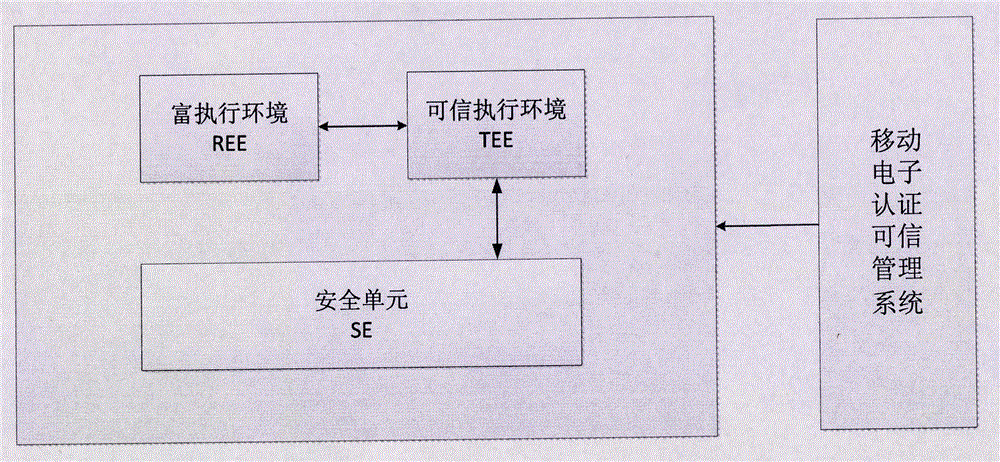
[0075] A secure electronic authentication method for a mobile terminal, comprising a built-in security element (SE) capable of storing keys in the mobile terminal and a built-in trusted execution environment (TEE) in the mobile terminal, the security element (SE) is provided with A safe application program applet that can run therein, the trusted execution environment (TEE) is provided with a safe echo trusted application program (TA), including the following steps:
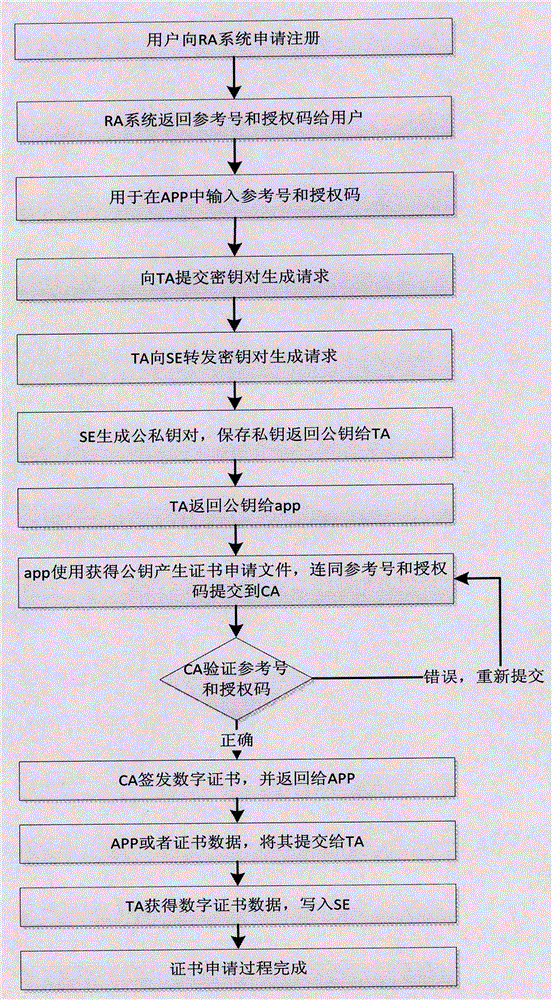
[0076] Step S1, the terminal uses the security application program applet to generate a public-private key pair inside the security element. The private key is stored in the security element (SE) and cannot be exported. The public key is submitted to the electronic certification service agency to apply for a digital certificate. After completing the digital certificate application After that, store the digital certificate inside the security unit;
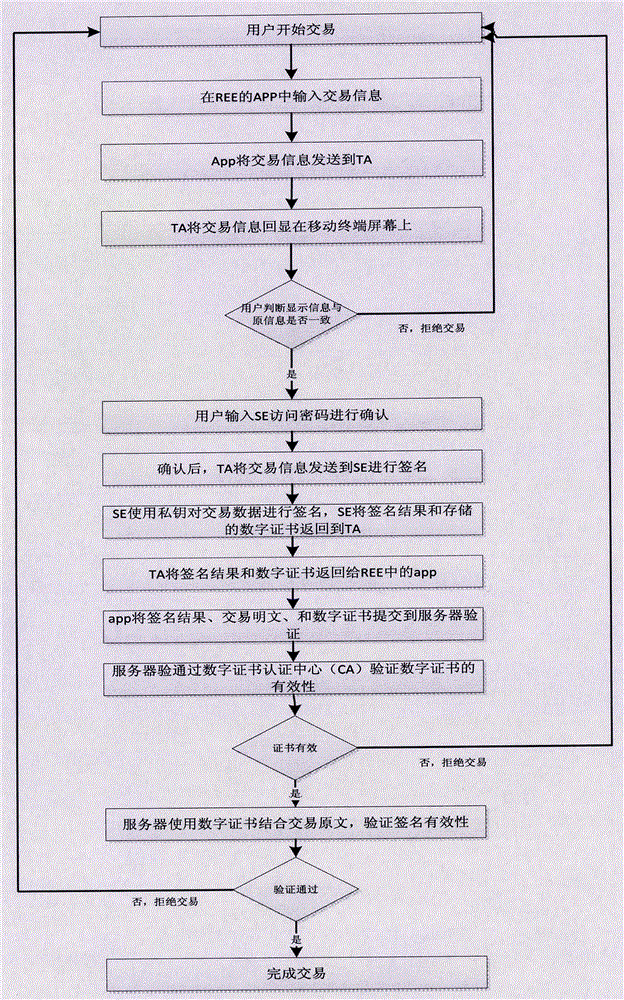
[0077] Step S2, before the user uses the mobile terminal APP to ...
Embodiment 2
[0080] A secure electronic authentication method for a mobile terminal, comprising a built-in security element (SE) capable of storing keys in the mobile terminal and a built-in trusted execution environment (TEE) in the mobile terminal, the security element (SE) is provided with A safe application program applet that can run therein, the trusted execution environment (TEE) is provided with a safe echo trusted application program (TA), including the following steps:
[0081] Step S1, the terminal uses the security application program applet to generate a public-private key pair inside the security element. The private key is stored in the security element (SE) and cannot be exported. The public key is submitted to the electronic certification service agency to apply for a digital certificate. After completing the digital certificate application After that, store the digital certificate inside the security unit;
[0082] Step S2, before the user uses the mobile terminal APP to ...
Embodiment 3
[0085] A secure mobile terminal electronic authentication method based on mobile phone security element (SE) and trusted execution environment (TEE) technology to realize transaction security echo, including a user private key that can be stored and cannot be exported, and can complete the signature encryption function A TA program that is built into the security element (SE) of the mobile terminal and can run in the trusted execution environment (TEE) to realize the transaction security echo function. A set of applets in the security element (SE) can be managed, and TA can be safely displayed. A mobile electronic authentication trusted management system managed by the program.
[0086] The public-private key pair generated by the PKI technology is generated in the built-in security element (SE) of the mobile terminal. Once the key is generated, the private key cannot be exported. Contains application applets running in a secure element (SE);
[0087] The transaction informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com