A Method of Image Encryption Based on Clustering and Chaos
An encryption method and technology of clustering algorithm, applied in the field of image encryption based on clustering and chaos, can solve the problems of insufficient anti-attack ability and low sensitivity, and achieve enhanced key sensitivity, enhanced chaos degree, and enhanced plaintext sensitivity. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
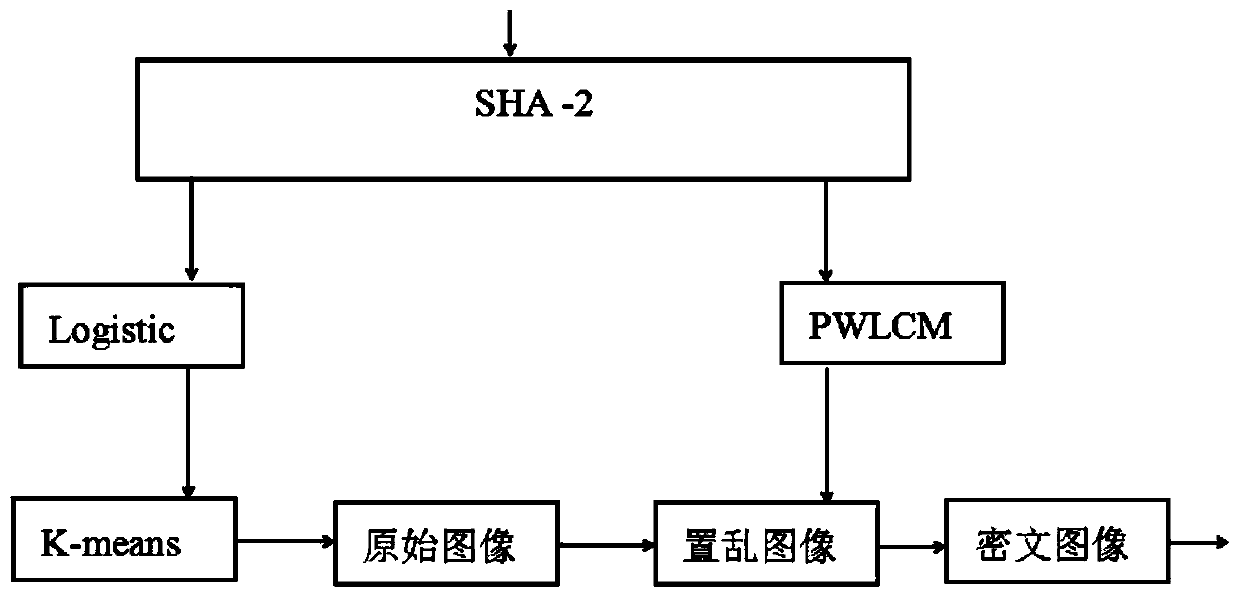
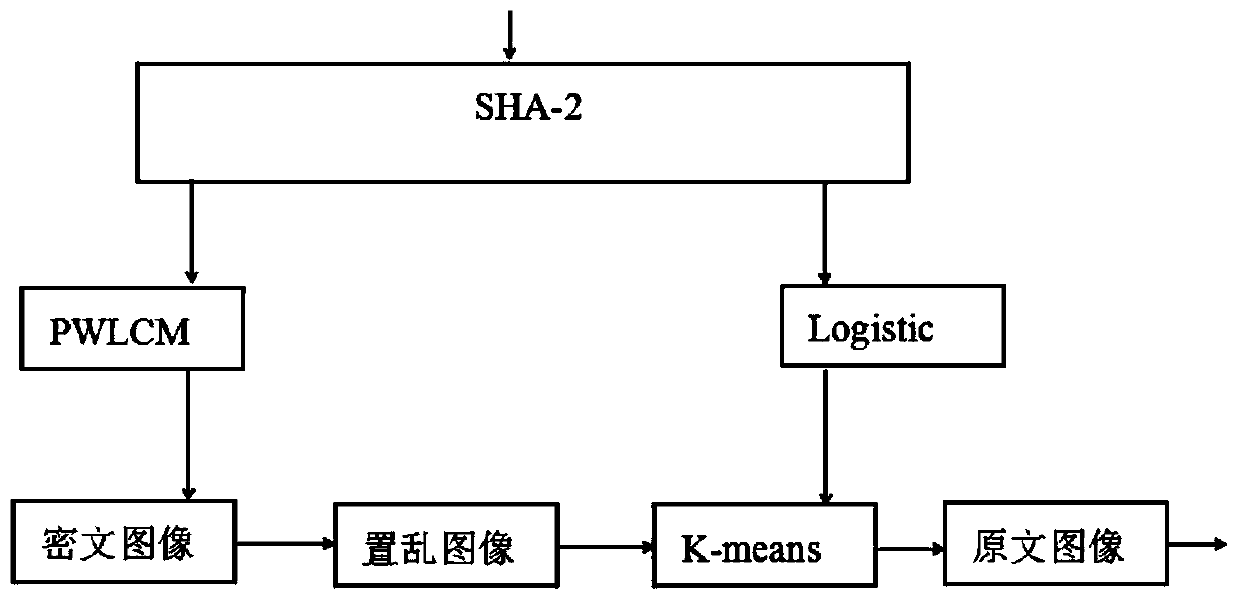
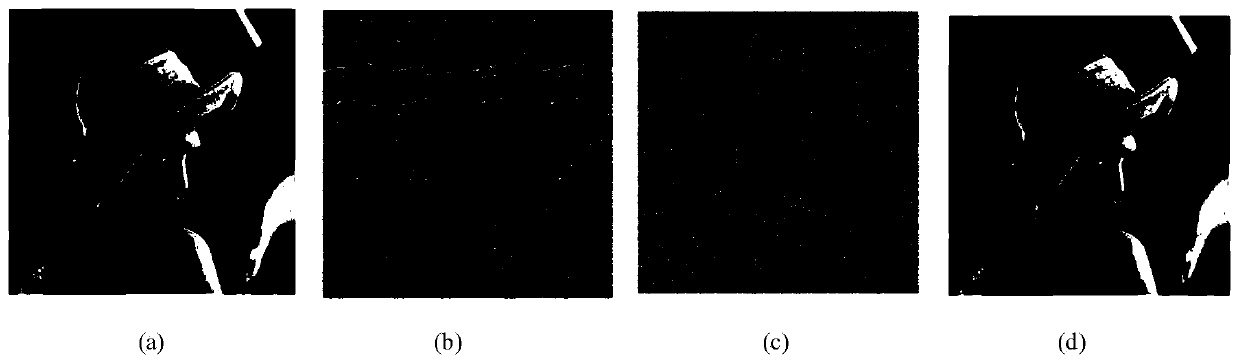
[0035] 1. The following combination figure 1 The encryption of the present invention is described in more detail
[0036] The flow of the encryption algorithm is as follows:
[0037] 1) First calculate the sum of all pixel values of the image P, and use formula (2) and formula (3) to generate the initial value x of the chaotic system 0 ,y 0 , xx 0 and yy 0 ;
[0038] 2) Use the initial value x 0 ,y 0 and formula (1) to generate the chaotic sequence (u i ,v i ), with xx 0 ,yy 0 and formula (2) to generate the cluster center sequence for k-means clustering operation.
[0039] 3) For any point l i =(ui ,v i ), use the k-means algorithm to cluster the chaotic sequence, and divide these points into k classes, which are cl 1 ,cl 2 ,Λ,cl k , and record the classification result l of each point i ∈cl j ,i∈[1,MN],j∈[1,k];
[0040] 4) Convert P to a one-dimensional sequence p 1 p 2Λ p MN , traverse the classification result k, and then start from the first pixe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com