Wireless sensor network homomorphic encryption privacy protection method
A wireless sensor and homomorphic encryption technology, applied in wireless communication, network topology, electrical components, etc., can solve the problems of unguaranteed data integrity, high computing and communication overhead, and inability to guarantee data fragmentation, etc., to achieve high reliability , reduce the network bandwidth, the effect of fast speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
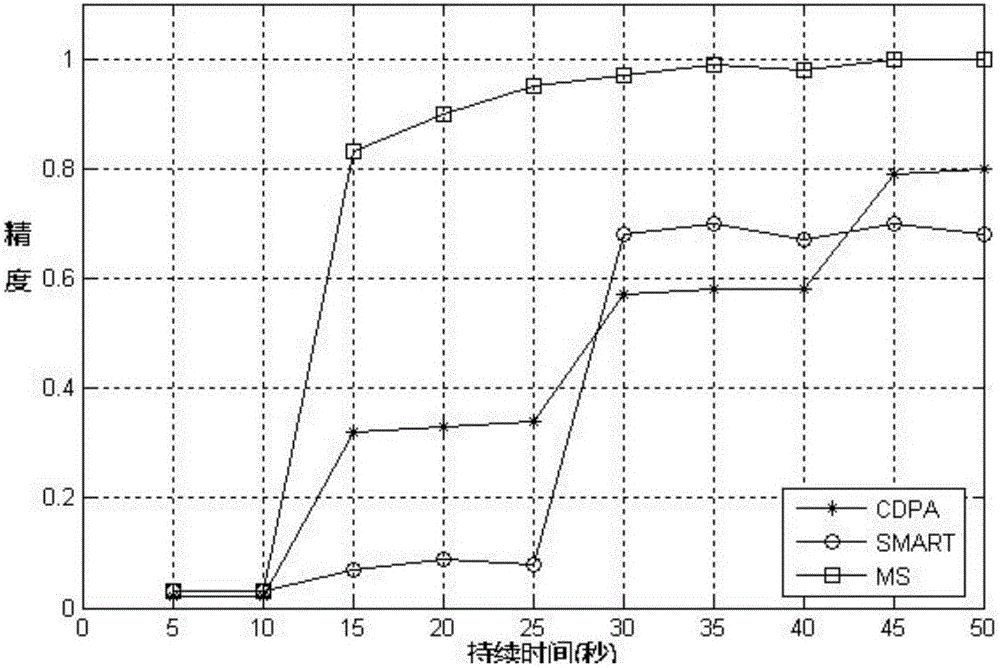
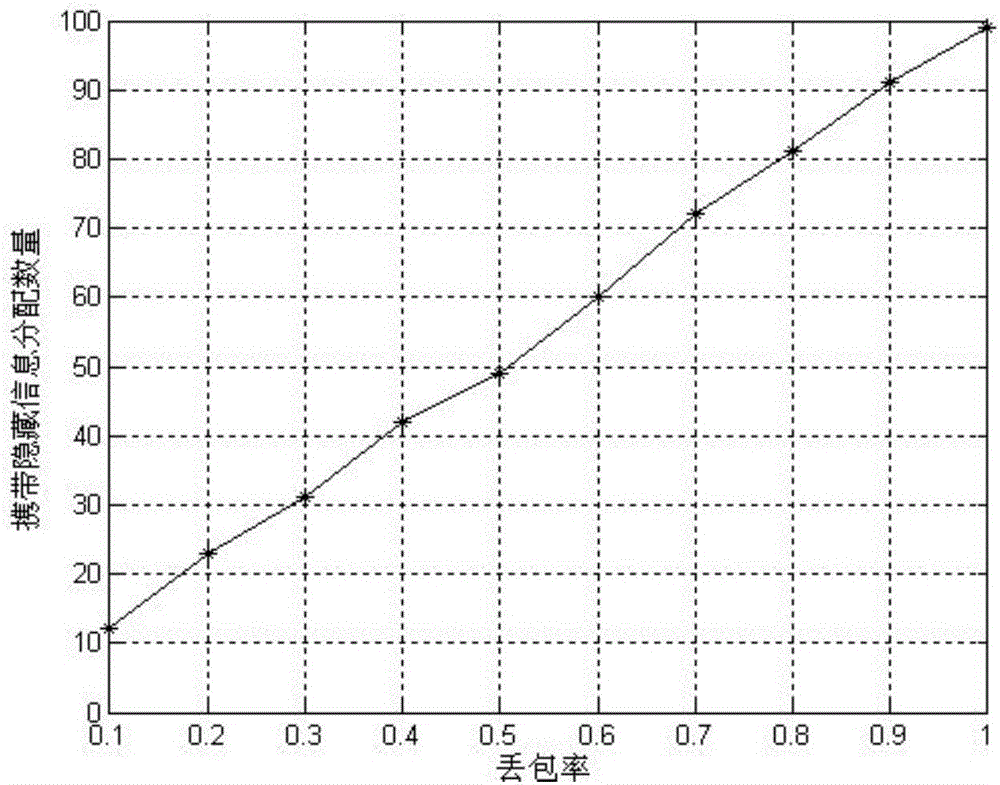
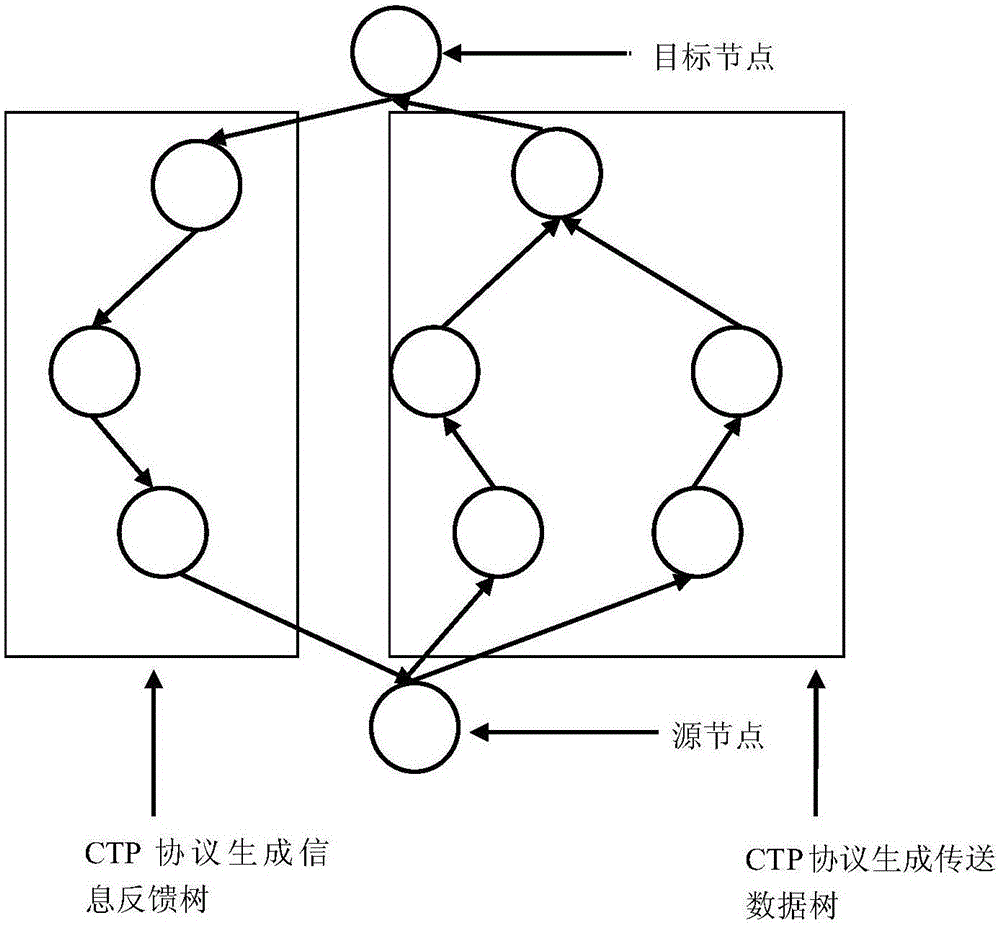
[0027] in such as image 3 In the network model shown, two routing trees are established from the source node to the target node, which respectively use the CTP protocol to generate an information feedback tree and a transmission data tree. Since the designed linear redundancy algorithm can dynamically adjust the redundancy, that is to say, the fragmentation strategy can be adjusted according to the packet loss rate, and the redundancy can be changed. Therefore, an information feedback tree with the source node as the root node is established, and the target node passes The situation of packet loss is fed back to the source node through the information feedback tree. The transmission data tree is a data transmission tree with the target node as the root node. The task is relatively simple, that is, to simply forward the fragmented data of the source node to the target node.
[0028] The source node first generates a test data packet to test the packet loss of the network and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com