Security pre-encoding method of multi-user opposite end-to-end relay system
A relay system and multi-user technology, which is applied in the field of precoding processing for multi-user to relay nodes in an end-to-end relay system, and can solve problems such as few studies and reports
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
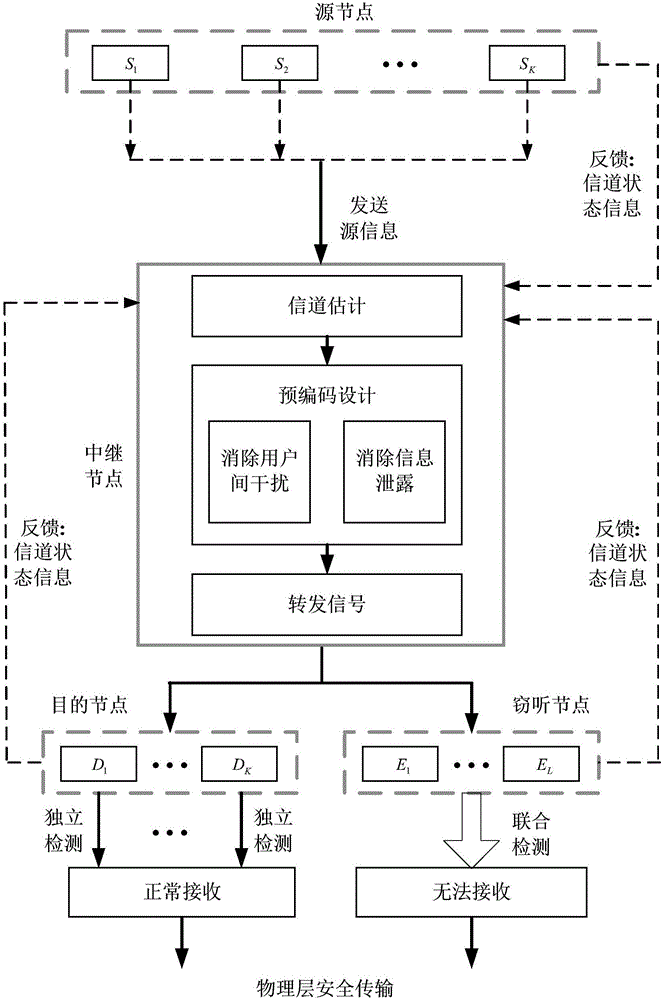
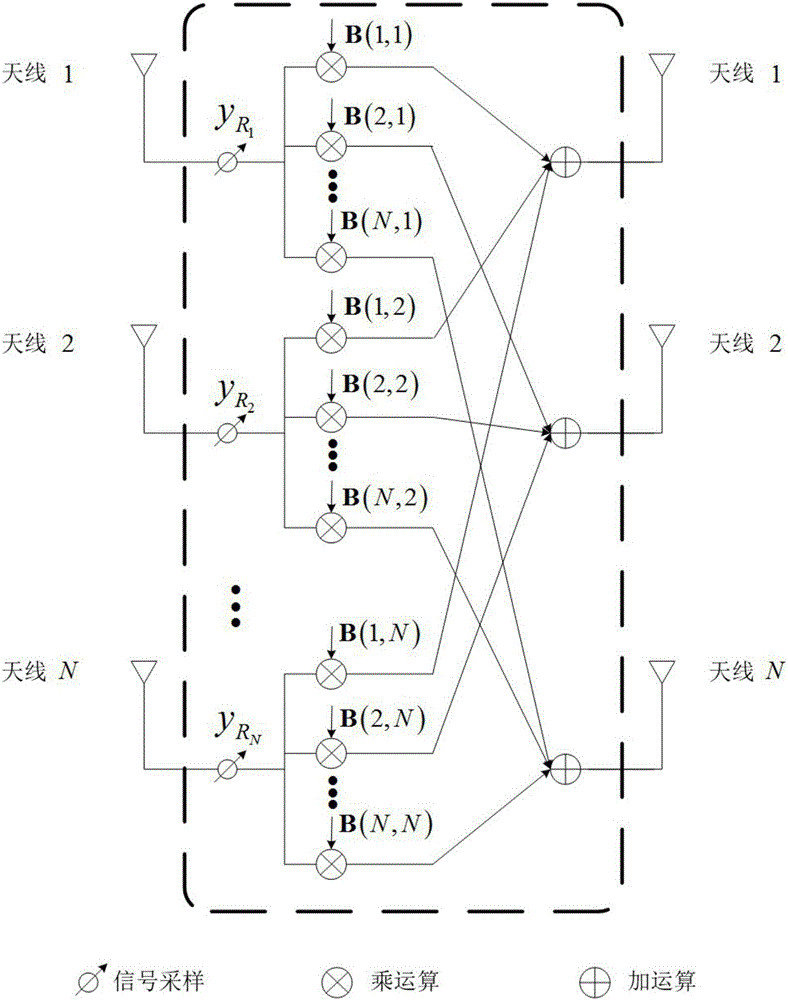
[0033] Technical scheme realization process of the present invention is as follows:
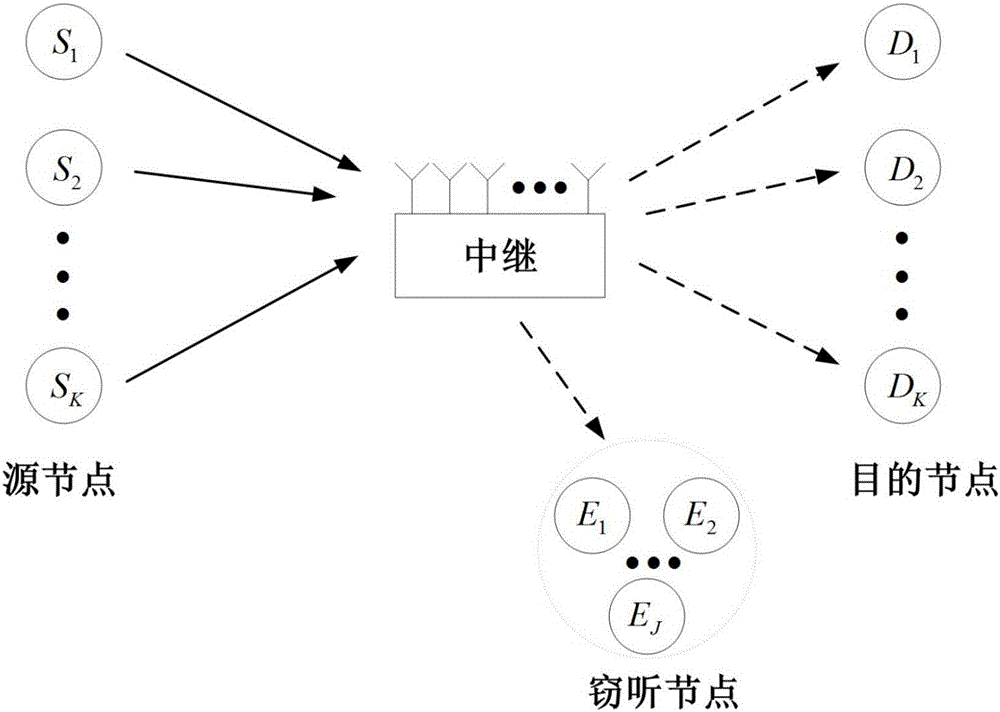
[0034] figure 1 The multi-user peer-to-peer relay communication system shown includes a relay node R and K source nodes S 1 ,S 2 ,...,S k ,...,S K , K destination nodes D 1 ,D 2 ,...,D k ,...,D K and J tapped section E 1 ,E 2 ,...,E j ,...,E J A multi-user peer-to-peer relay system is formed. In the system, K source nodes and K destination nodes realize long-distance communication with the assistance of relay R. Each source node S k respectively corresponding to the kth destination node D k Form a set of user pairs {S k ,D k}, forming a total of K groups of user pairs {S 1 ,D 1},{S 2 ,D 2},...,{S k ,D k},...,{S K ,D K}. Among the K groups of user pairs, each destination node D k Only want to get the source node S k The private information sent by other source nodes is regarded as interference. The K group of user pairs and the J eavesdropping nodes are all legal mobi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com