A Hardware Trojan Horse Detection and Discrimination Method Based on Distance Measure Distribution
A hardware Trojan detection and distance measurement technology, applied in the protection of internal/peripheral computer components, etc., to achieve the effect of small calculation amount, fast detection speed and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
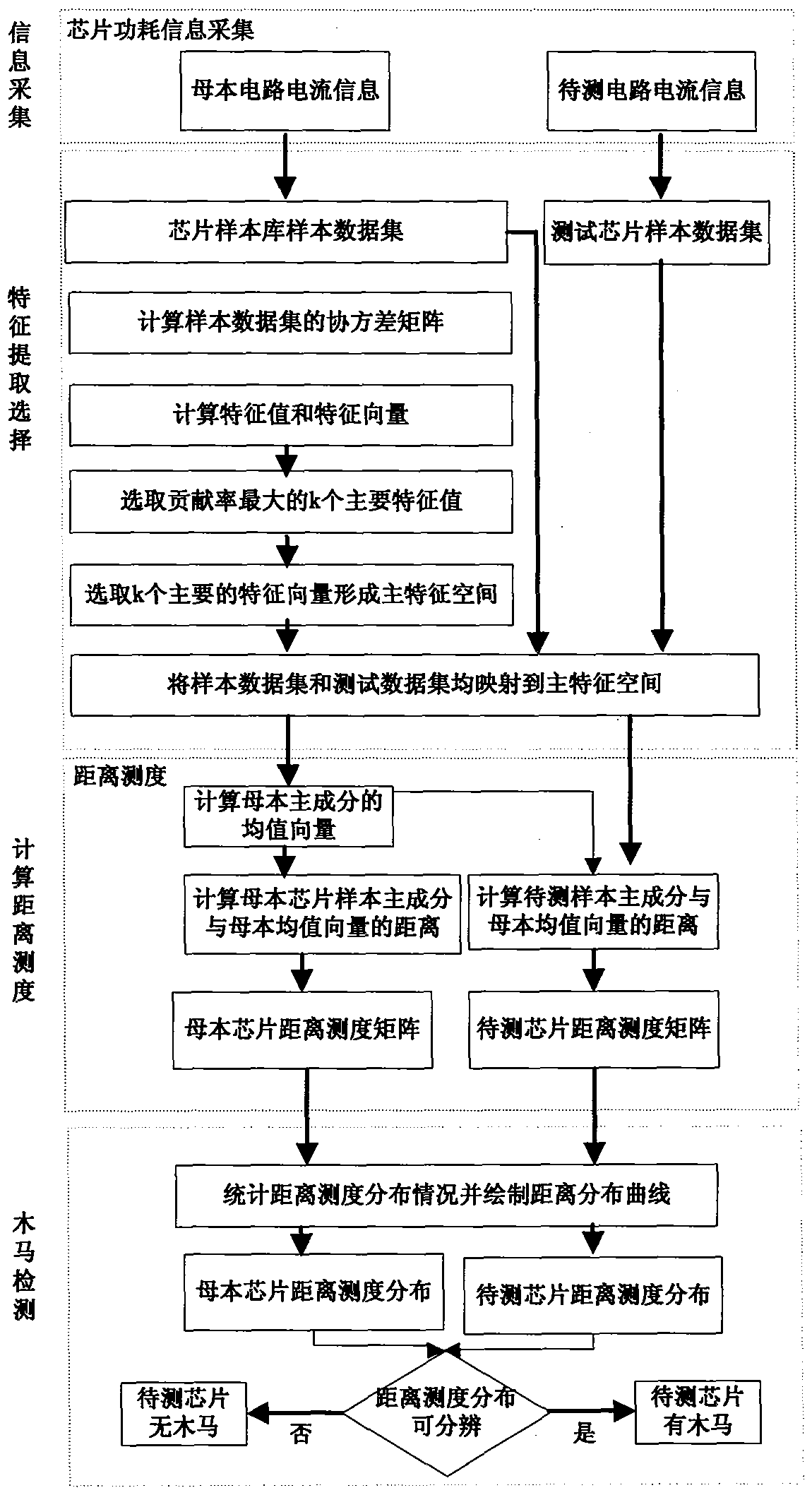
[0030] A hardware Trojan horse detection method based on distance measure distribution, the steps are as follows:
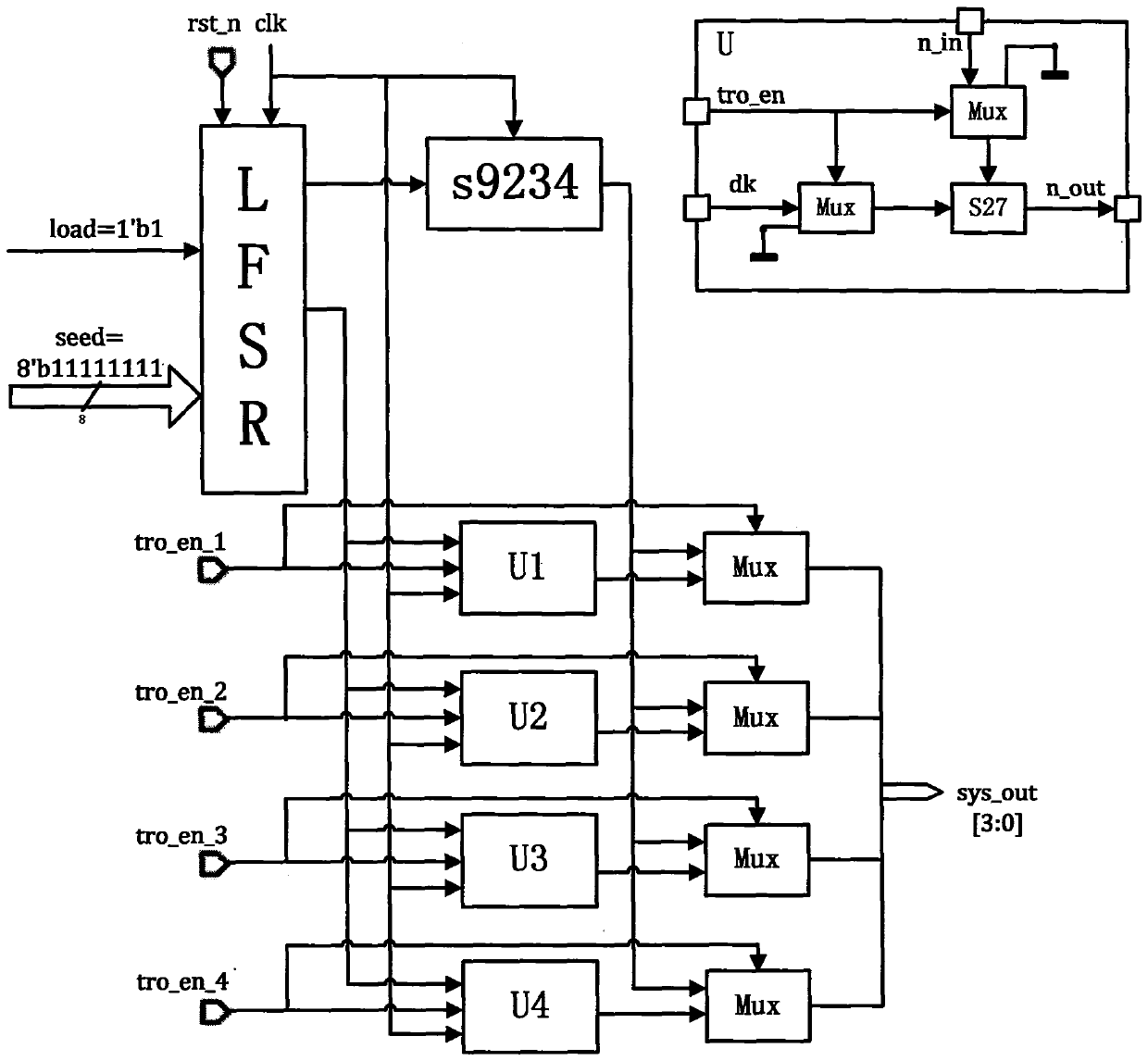
[0031] (1) According to FPGA hardware platform resource, the present invention has designed carrier circuit and Trojan horse circuit based on ISCAS'89 reference test circuit, selects the most suitable s9234 of platform as carrier circuit, and has selected the s27 that most meets this carrier circuit area ratio as Trojan horse circuit, the schematic diagram of the circuit structure is as follows figure 2 shown. The Clk clock is used as an external system clock, and rst_n provides a reset for the system. The module LFSR is used as a pseudo-random number generator to provide input for the carrier circuit, and at the same time provide input for the hardware Trojan circuit. The seed is provided for the pseudo-random number generator through seed, which is set to 8’b11111111. The Load signal determines whether to load the seed into the pseudo-random number generator...
Embodiment 2
[0044] A hardware Trojan horse detection method based on distance measure distribution, the steps are as follows:
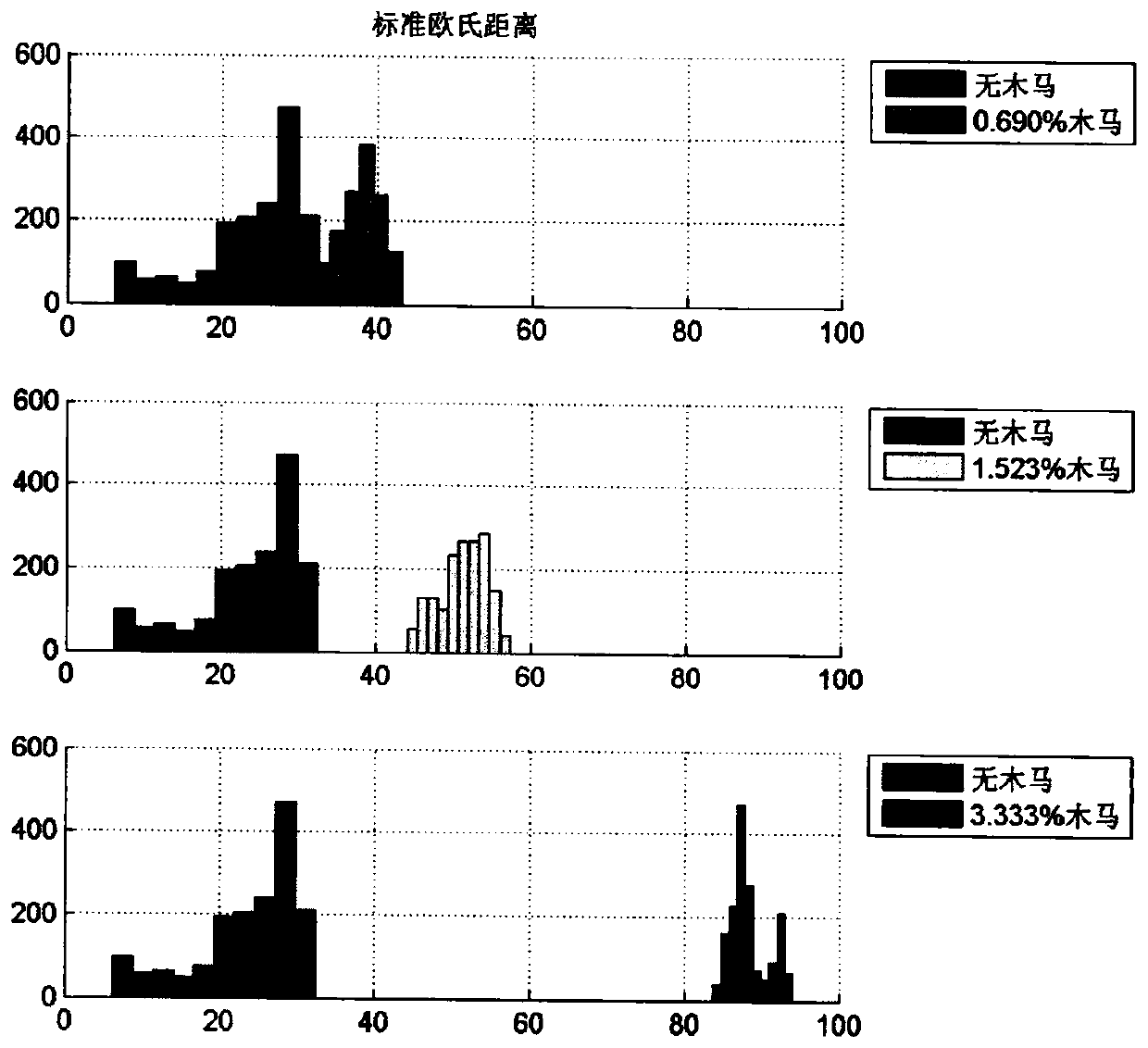
[0045] Using the same chip and detection platform as in Example 1, change the distance measurement algorithm in Example 1, and use the angle cosine distance measurement method to measure the distance between the parent chip and the three Trojan horse chips in Example 1, and finally obtain The statistical results of the histogram of the distance measure distribution are shown in Fig. 3(b). The distance distribution between the mother chip and the Trojan chip under test implanted with the largest area (3.333%) Trojan horse circuit is in a completely different interval, and the distance distribution pattern has obvious differences, which can be completely distinguished, that is, the hardware Trojan can be measured; while the mother chip The chip and the chip under test implanted with a medium-area (1.523%) Trojan horse circuit have a certain overlap in the cosine di...
Embodiment 3
[0047] A hardware Trojan horse detection method based on distance measure distribution, the steps are as follows:
[0048] Using the same chip and detection platform as in Example 1, change the distance measurement algorithm in Example 1, and use the Mahalanobis distance measurement method to measure the distance between the parent chip and the three Trojan horse chips in Example 1, and finally obtain the distance The statistical results of the measure distribution histogram are shown in Fig. 3(c). It can be clearly seen that there are differences in the distance distribution of the three groups, but with the increase of the Trojan horse area, the distance distribution span of the female parent and the Trojan horse chip will be relatively reduced, but the distance distribution is still in different intervals, and the distance distribution patterns are obvious. The differences can be completely distinguished, and hardware Trojan chips of different areas can be detected.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com