A method and device for data storage, data verification, and data traceability
A data storage and data verification technology, which is applied in database query, database indexing, digital data protection, etc., can solve the problems that data is easy to be tampered with and data authenticity cannot be determined
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
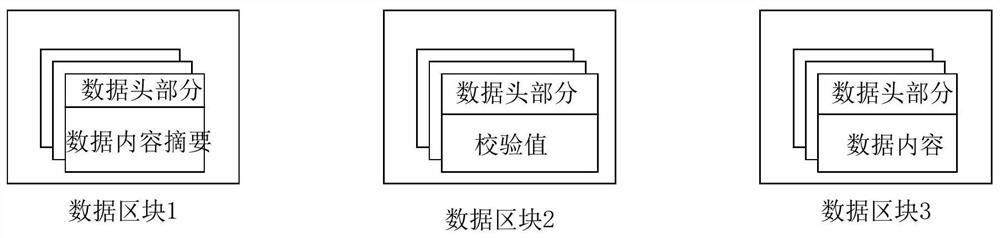
Image
Examples
Embodiment 1
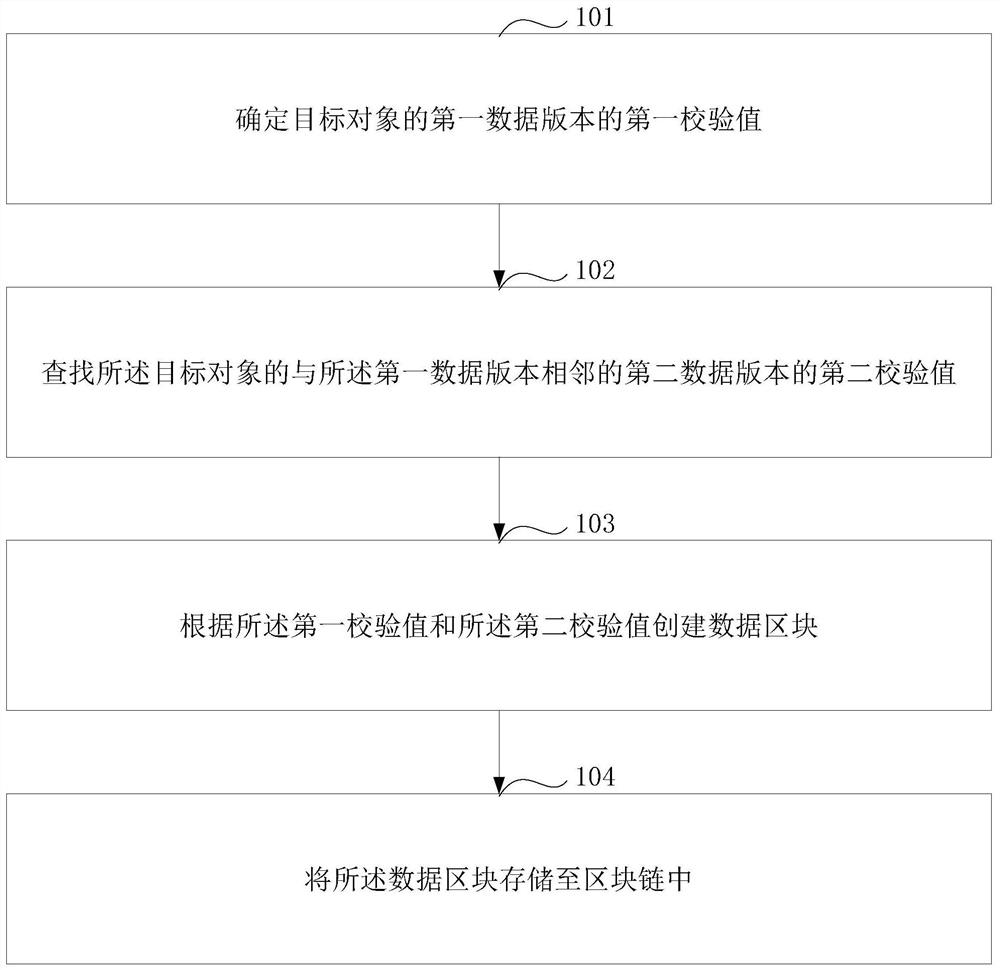
[0056] figure 1 It is a schematic flowchart of a data storage method provided by the embodiment of the present application. The method can be as follows.
[0057] Step 101: Determine the first check value of the first data version of the target object.
[0058] In the embodiment of this application, the target object here can be any form of data, it can be a business form, a book manuscript, a software source code; it can also be a set of pictures, a piece of music, a video, No specific limitation is made here.
[0059] The data version of the target object here may refer to the different data content evolved during the entire life cycle of the target object, and an identification can be set for each data content, which can be called the version identification of the data version.
[0060] For example: for a video, each part (or each season) of the video can be called a data version, assuming that the first part of video A corresponds to data version 1.0, then the second pa...
Embodiment 2
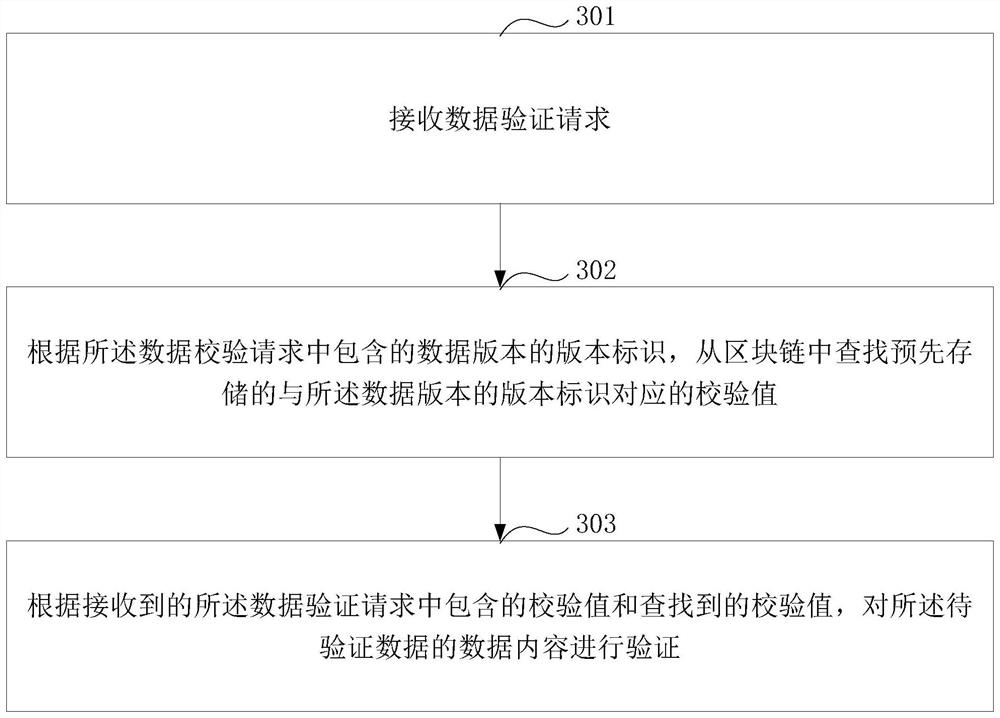
[0105] Based on the same inventive idea, image 3 It is a schematic flowchart of a data verification method provided in the embodiment of the present application. The method can be as follows.
[0106] Step 301: Receive a data verification request.
[0107] The data verification request includes the version identifier of the data version of the data to be verified and the verification value obtained based on the data content of the data to be verified.
[0108] In step 301, the execution subject of the embodiment of the present application may be a blockchain or other devices, which are not specifically limited here.
[0109] Specifically, when the data demander receives the data provided by the data provider, it can regard the provided data as the data to be verified, and determine the version identification of the data version of the data to be verified, and based on the obtained data to be verified The data content of the data is calculated to obtain the verification val...
Embodiment 3
[0124] Figure 5 It is a schematic flowchart of a data traceability method provided in the embodiment of this application. The method can be as follows.
[0125] Step 501: Receive a data backtracking request.
[0126] The data traceback request includes a version identifier of the first data version of the data to be traced back.
[0127] In step 501, when it is necessary to find the evolution process or evolution history of the target object, the operation of the embodiment of the present application can be started, that is, a data traceback request is sent, and the data traceback request includes the version of the first data version of the data to be traced back logo.
[0128] The version identifier of the first data version here may be the version identifier of the current data version, or the version identifier of any data version, which is not limited here.
[0129] Here, the version identifier of the first data version is used to determine the starting point of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com