Method and device for verifying user identity
A technology for user identity and verification methods, applied in data processing applications, instruments, payment systems, etc., can solve problems such as improper user settings and uneven security awareness, achieve objective determination of risk levels, and improve reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
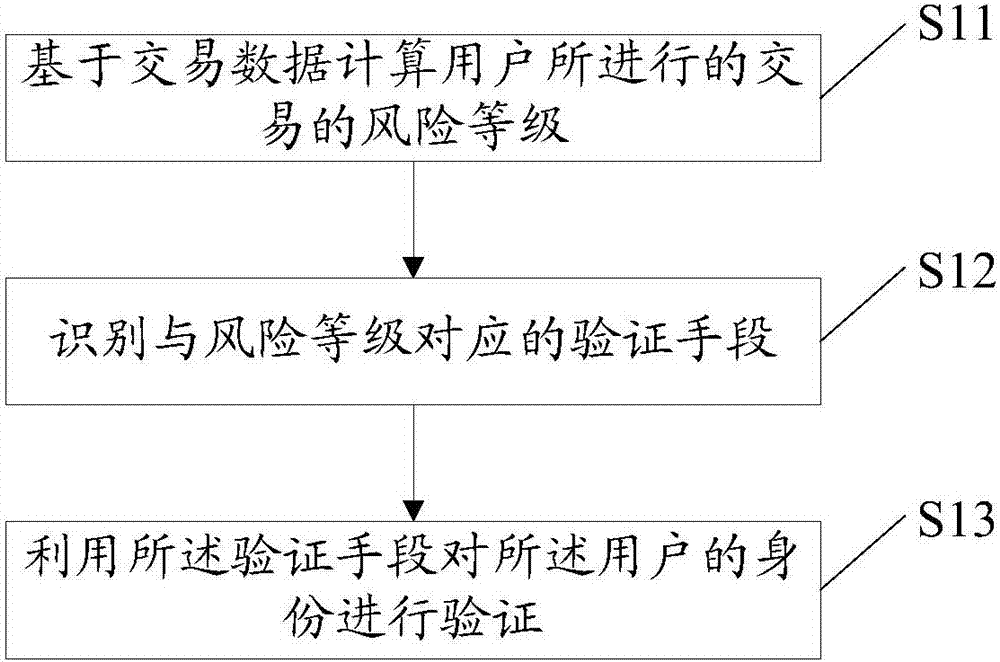
[0025] figure 1 It is a flow chart of the user identity verification method according to Embodiment 1 of the method of the present invention. see figure 1 , in this embodiment, the method includes:
[0026] S11: Calculate the risk level of the transaction performed by the user based on the transaction data.
[0027] S12: Identify a verification means corresponding to the risk level.
[0028] S13: Verify the identity of the user by using the verification means.
[0029] Among them, the data items (or attributes) in the transaction data include, but are not limited to: hardware information of the terminal device that executes the transaction, geographic location information of the terminal device, transaction time information, transaction type information, transaction object information, and transaction amount information etc.
[0030] In addition, verification means include, but are not limited to: static passwords, SMS verification codes, biometric identification, and dig...
Embodiment approach 2
[0033] The method provided in this embodiment includes all the content in the method embodiment 1, which will not be repeated here. Wherein, in this embodiment, processing S11 is realized by the following processing:
[0034] Transaction data for the transaction is input into a classification model to obtain the risk rating.
[0035] Among them, the classification model is also called a classifier, which can map data to one of the given categories, so that it can be applied to data prediction. The algorithms used include decision tree, logistic regression, naive Bayesian, neural network etc.
[0036] The process of constructing the classification model (classifier) will be described in detail below.
[0037] First, select sample data from the user's historical transaction data, classify the sample data, mark the type corresponding to each piece of sample data, that is, add classification marks, and divide the sample data after adding classification marks into a training se...
Embodiment approach 3
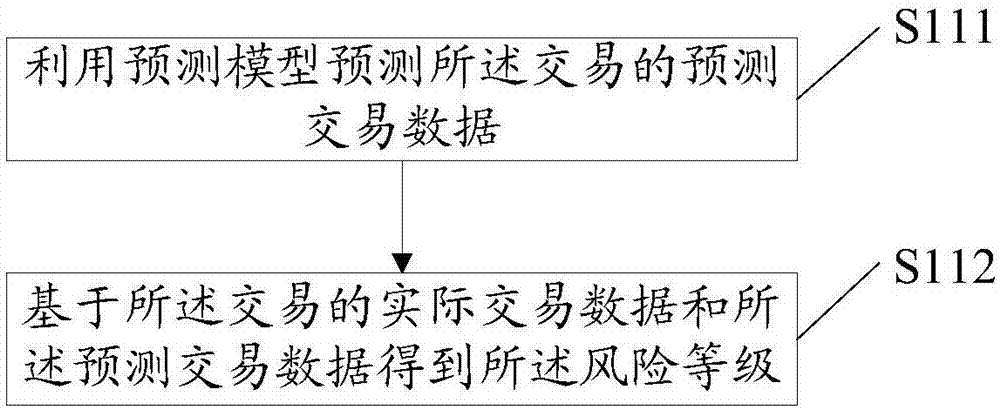
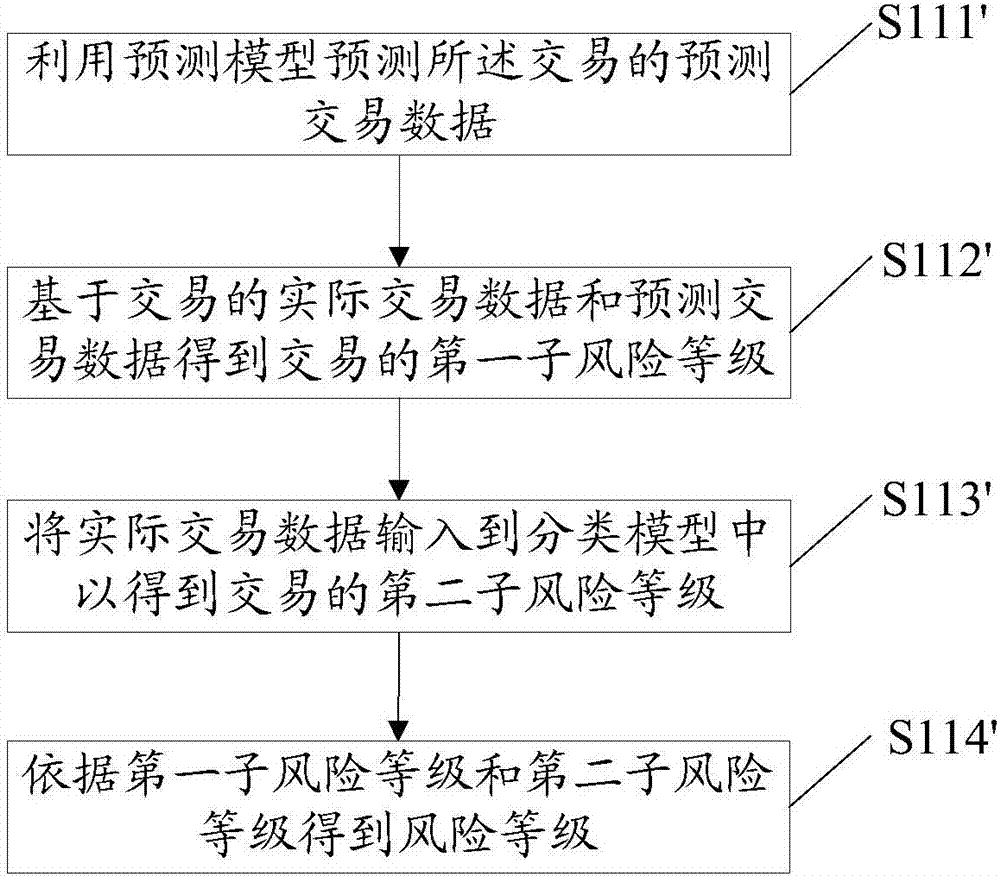
[0042] The method provided in this embodiment includes all the content in the method embodiment 1, which will not be repeated here. Among them, such as figure 2 As shown, in this embodiment, processing S11 includes the following processing:
[0043] S111: Use the prediction model to predict the predicted transaction data of the transaction.
[0044] S112: Obtain the risk level based on the actual transaction data of the transaction and the predicted transaction data.
[0045] Among them, similar to the construction process of the classification model, the training set is used to build the prediction model first, and the same evaluation index as the classification model is used, and then the verification set is used to verify the prediction model, but the training set and verification used to build the prediction model Sets do not need to introduce categorical tags.
[0046] Since the specific values of the sample data may have a large degree of dispersion, preferably, in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com