Detection method of power grid false data injection attack based on nonlinear measurement equation
A technique for measuring equations and injecting attacks, which is applied in the direction of digital data protection, etc., can solve problems such as false data injection attack detection, and achieve the effect of saving calculation time and improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
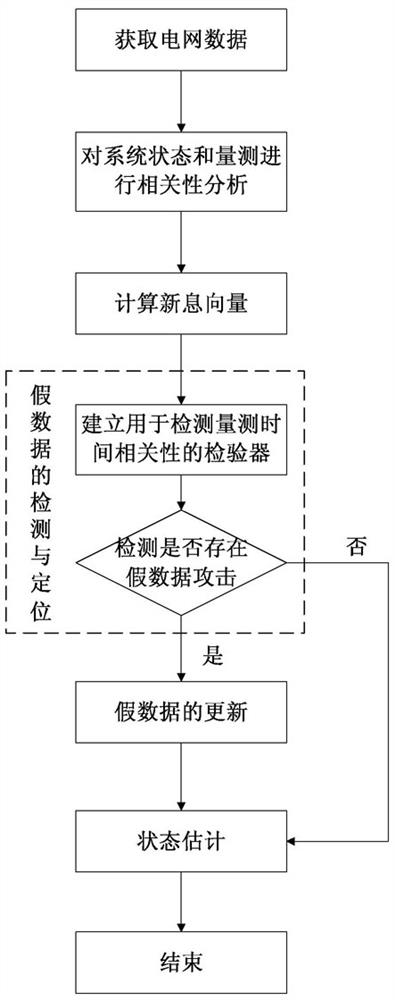
[0052] Embodiment 1: as attached figure 1 As shown, the power grid false data injection attack detection method based on the nonlinear measurement equation includes the following steps:
[0053] Step 1: Obtain grid data, the grid data includes grid topology, line parameters and historical state estimation data, wherein the grid topology includes the connection status between lines, switch opening and closing conditions; line parameters include line conductance and ground Susceptance, then enter the second step;
[0054] Step 2: Perform power grid system state correlation analysis and power grid system measurement correlation analysis; the power grid system state correlation analysis includes time correlation modeling of n-node systems and state prediction of n-node systems; the The power grid system measurement correlation analysis includes the time correlation between the current measurement value and the measurement prediction value, as follows:
[0055] (1) Carry out the ...
Embodiment 2
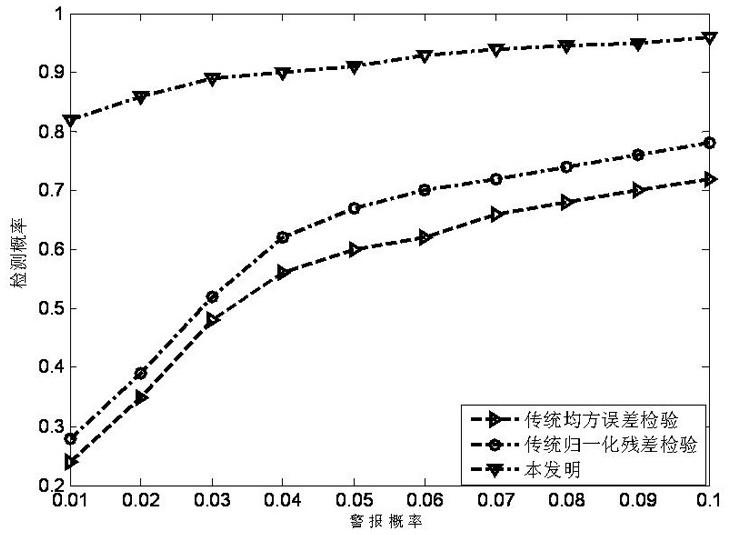
[0097] Embodiment 2: as attached figure 2 As shown, in the IEEE30 system, there are 86 SCADA measurements in the system. When the IEEE30 system is in stable operation (no sudden load change, generator failure, short circuit, etc.), the mean value of the SCADA measurement data is 0, and the standard deviation is 0.01 random Gaussian white noise; attack the phase angle of nodes 4 and 16, the attack range is 20% of the original value; detection threshold λ 1 =3; This emulation is under the Matlab environment and is configured as 2.5GHz, 8GB memory, and the processor is carried out on the computer of Core i5, and with the method of the present invention, traditional error mean square detection method, traditional normalization The residual error test method is used for detection at the same time.
[0098] The test results are attached figure 2 As shown, from attached figure 2 It can be seen that the detection effect of the method of the present invention is better than that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com