Dynamic protection method of implementation process of industrial configuration monitoring software
A technology for monitoring software and execution process, applied in the direction of platform integrity maintenance, etc., can solve problems such as poor security awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
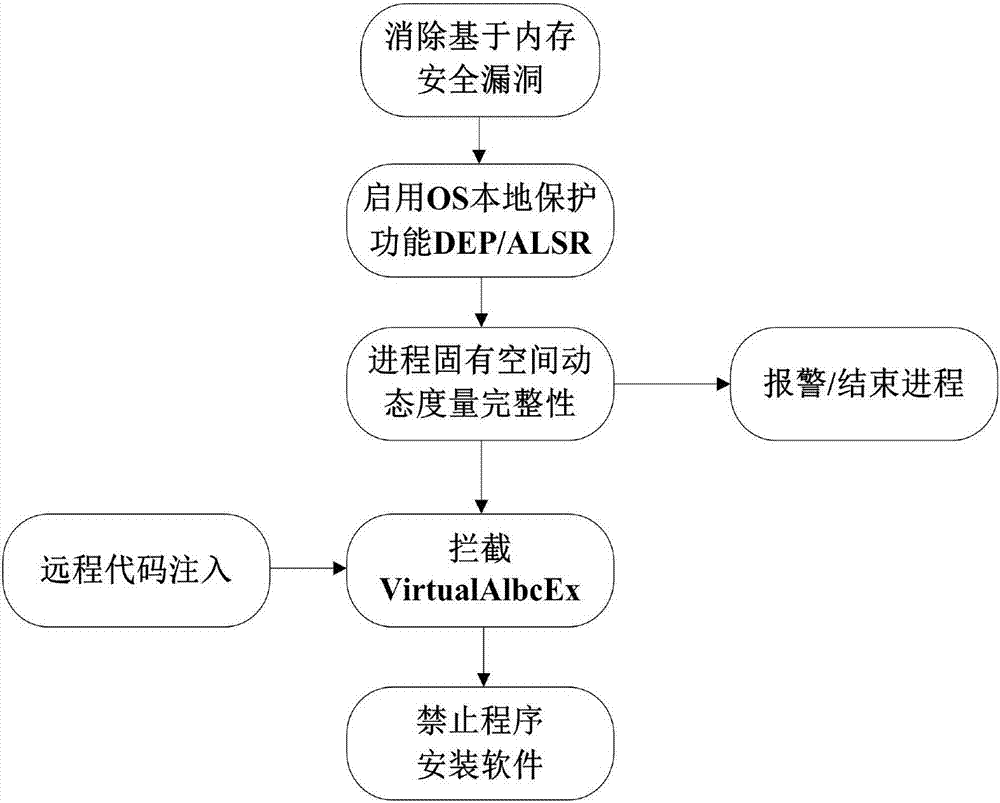
[0035] 1 Eliminate all known security vulnerabilities: such as compiling software with the GS compilation option to eliminate buffer overflow vulnerabilities as much as possible; such as implementing the SEH verification mechanism; applying OS patches in time, upgrading the software to a safe version, etc.;
[0036] 2 Make sure the local protection function of the operating system is enabled
[0037] 2.1 Enable DEP
[0038] In Computer Properties ---> System ---> Performance Properties ---> Data Execution Prevention, turn on the DEP settings; enable the operating system, services, and applications to enable the DEP function.
[0039] 2.2 Using an operating system with ALSR enabled
[0040]Now the mainstream operating systems basically implement ALSR: OpenBSD, Linux2.6.12 and later, windowserver 2008, windows 7, Vista, Windows Server 2008R2, MAC OS X, IOS 4.3.
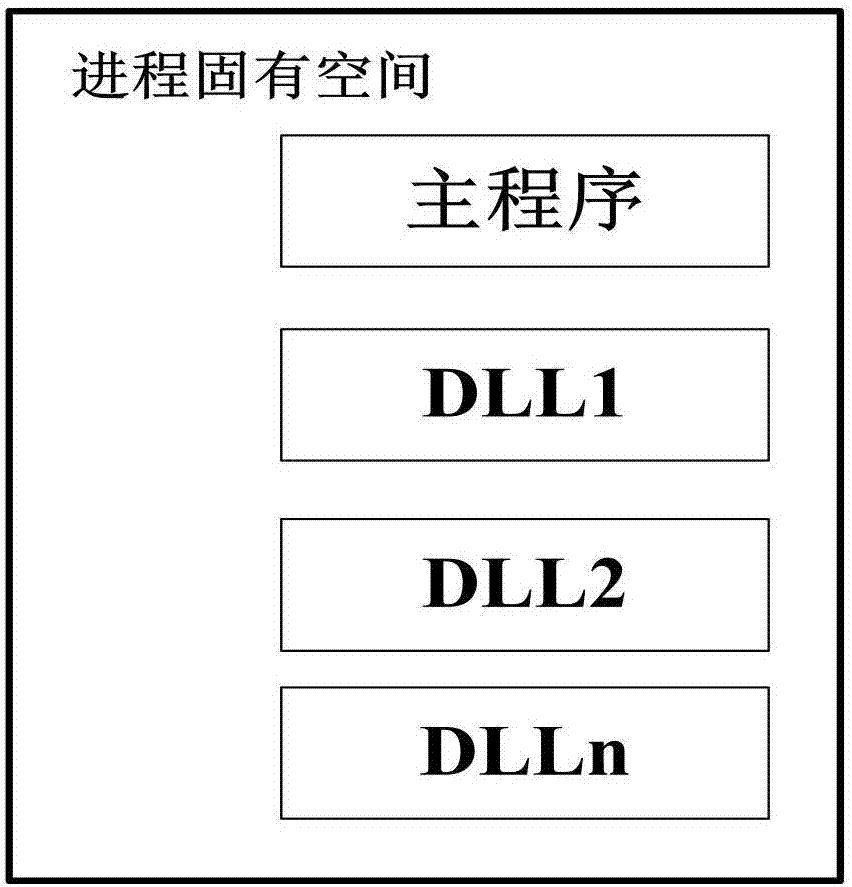
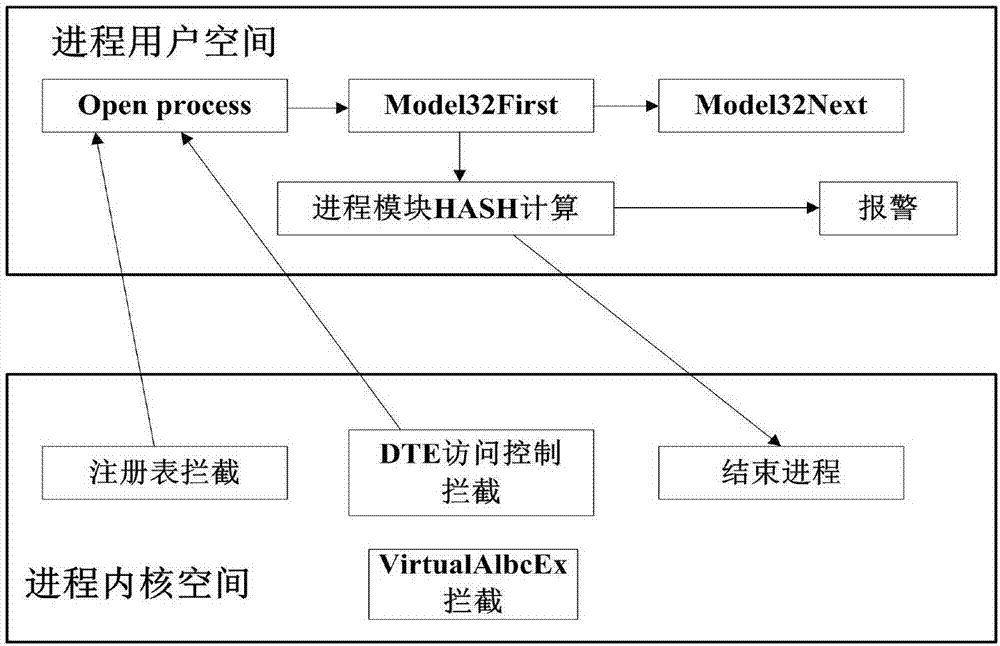
[0041] 3 Realize dynamic measurement of process memory space and execution memory allocation detection
[0042] 3....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com