Lorenz system optimal sequence and K-L transform-based image encryption method
An encryption method and K-L transformation technology, applied in the field of image encryption based on the optimal sequence of the Lorenz system and K-L transformation, can solve the problems of image encryption speed defects, etc., to avoid insufficient security, improve security, and improve algorithm speed Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
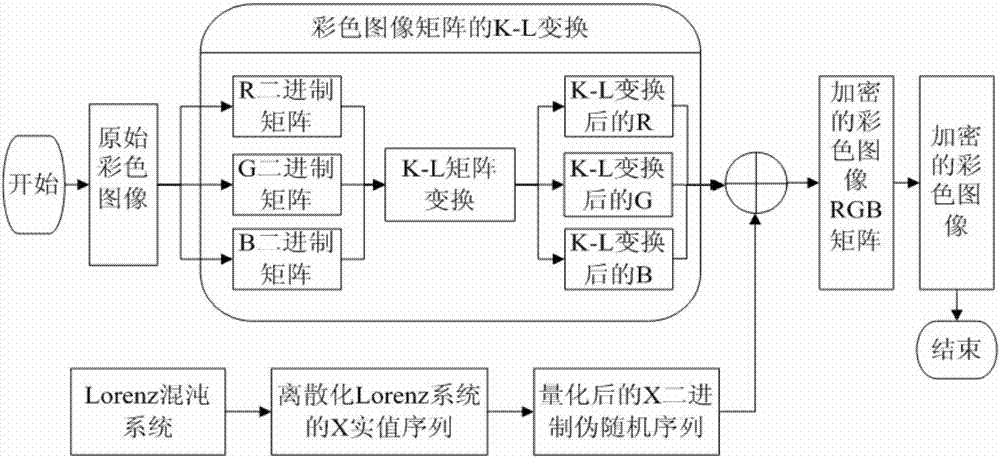
[0059] An image encryption method based on Lorenz system optimal sequence and K-L transformation, the steps are as follows:
[0060] 1. The steps of the image encryption algorithm:
[0061] (1) Generation of the optimal sequence of the Lorenz system
[0062] The system model of the three-dimensional Lorenz chaotic system equation is a ternary first-order nonlinear differential equation, and its system equation is:
[0063]
[0064] where a, b, c are real parameters limited within a certain range of variation, and x, y, z are variables of the equation.
[0065] The Lorenz chaotic system is a continuous chaotic system, so if we want to use the Lorenz chaotic system to obtain the chaotic sequence used in the encrypted image, we must first discretize the chaotic system, considering the hardware implementation, the complexity of the algorithm, and the speed of operation And resource occupation and other factors, choose Euler's method (Euler) to discretize the Lorenz chaotic sy...
Embodiment 2
[0103] The process implemented in the hardware of Embodiment 1
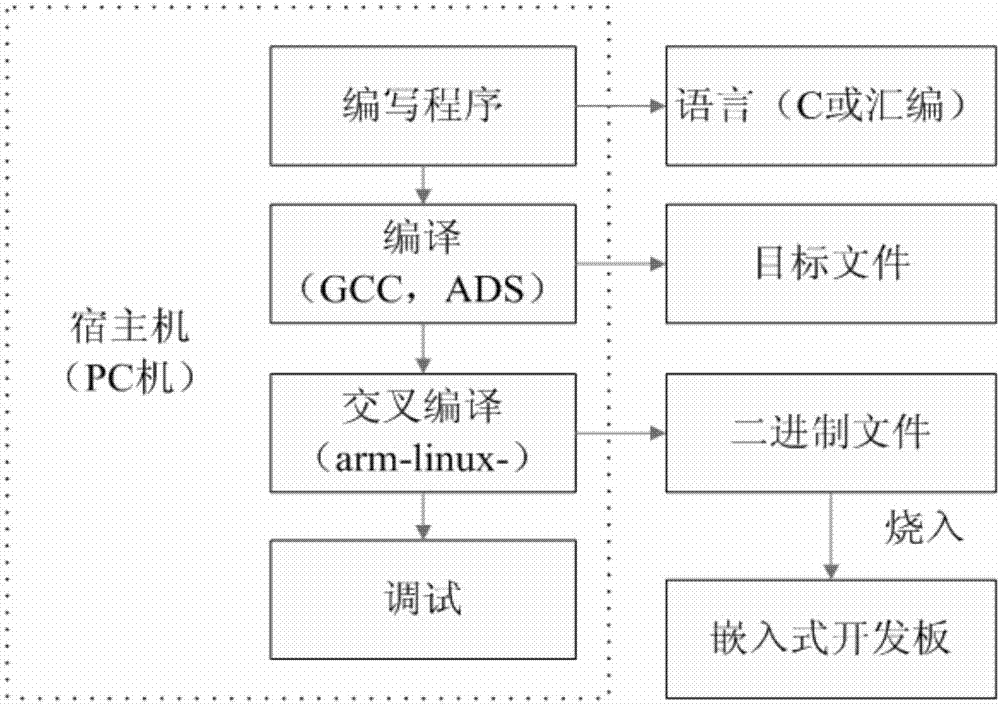
[0104] (1) Establish a cross-compilation environment in the Linux system on the PC side. The process is to write and compile the application program on the PC side, also known as the host computer, and then cross-compile the executable program and transplant it. Go to the target machine, that is, the binary file that can run in the embedded development board, and burn the binary file into the embedded development board. Therefore, the establishment of a cross-compilation environment is the basis for implementing embedded programs. Its specific development model is as follows: figure 2 shown.
[0105] (2) Cut out the kernel and root file system in the Linux system, and transplant them to the embedded development board after cross-compilation to realize the most basic embedded development environment.
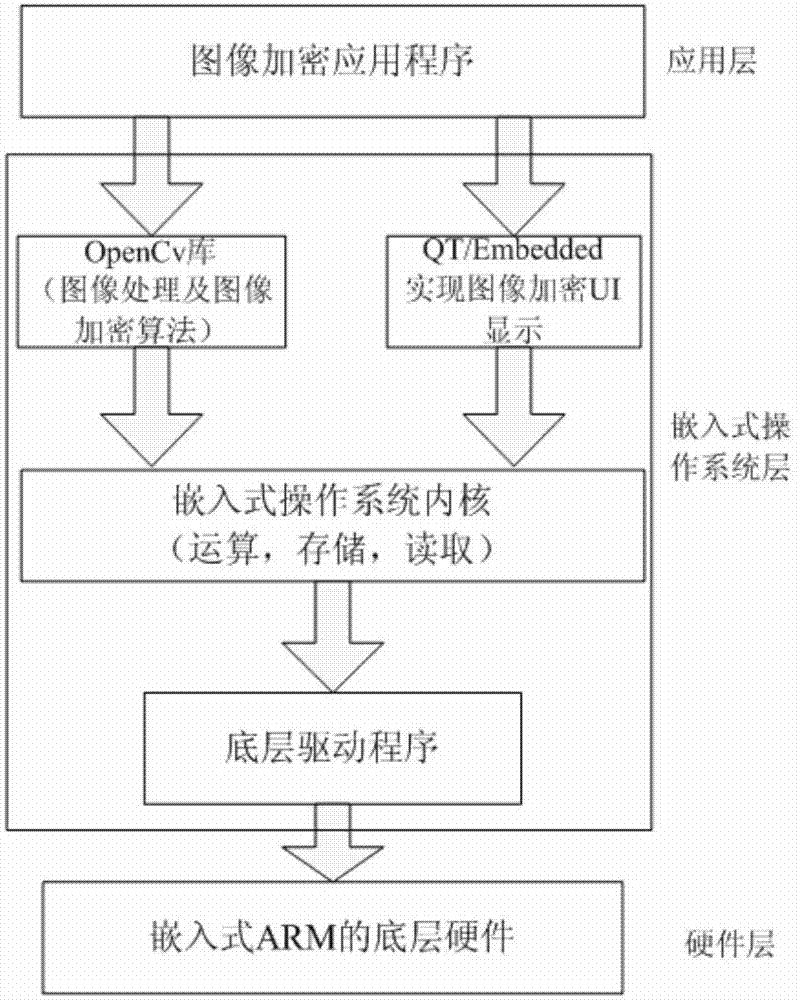
[0106] (3) Before realizing the image encryption of the embedded ARM platform, all programming should be impl...
Embodiment 3
[0116] Select a color image with a size of 256×256 and encrypt it. After encryption, use the same method to obtain the decryption result. The encryption and decryption results are as follows: Figure 5 Shown:
[0117] According to the encryption results, it can be seen intuitively that the encrypted image is unrecognizable from the original image, and the distribution is relatively uniform. The decrypted image is exactly the same as the original image. For the pixel correlation we want to improve, an intuitive data analysis and The analysis of the simulation image also analyzes the horizontal, vertical and diagonal components of the R, G, and B color components of the image respectively. The data analysis results are shown in the following table:
[0118] Table 1 Correlation coefficient values of adjacent pixels
[0119]
[0120] According to the calculation result table, the encryption algorithm improved by K-L transformation has a great improvement in pixel correlation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com