Authorization authentication method, device and system based on device fingerprint
A technology of device fingerprinting and authority authentication, applied in the computer field, can solve problems such as insecurity, and achieve the effects of ensuring performance security and information security, avoiding duplication, and ensuring uniqueness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
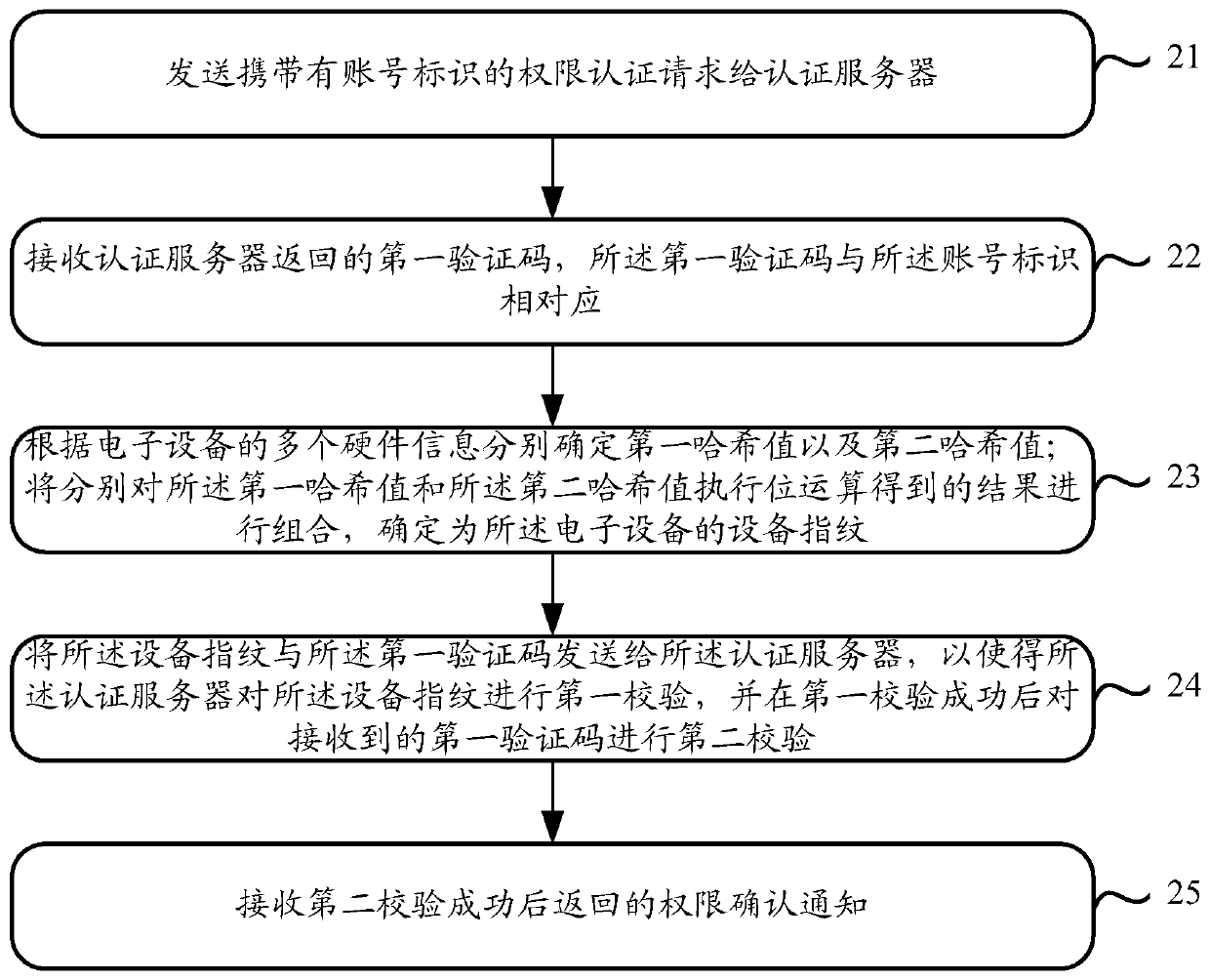
[0078] like figure 2 Shown is a schematic diagram of the steps of the authority authentication method provided by the embodiment of the present application. The authority authentication is mainly performed based on the device fingerprint. pad or other computer equipment, the method mainly includes the following steps:
[0079] Step 21: Send an authorization authentication request carrying the account ID to the authentication server.
[0080] Wherein, the account identifier involved in this step 21 can be understood as an identifier that can distinguish users, such as mobile phone number, ID number, etc., or a serial number, QR code, etc. that can distinguish users generated according to user information.
[0081] In addition, the authorization authentication request in this step may be initiated by the user when requesting services such as login or payment, and the authorization authentication request may be specifically generated according to the user's click on a control o...
Embodiment 2
[0163] The above authorization authentication method belongs to the same inventive concept, and the present application also provides a device for executing the above method.
[0164] refer to Figure 8 As shown, a permission authentication device includes:
[0165] The first sending unit 81 is configured to send the authority authentication request carrying the account identifier to the authentication server;
[0166] The first receiving unit 82 is configured to receive a first verification code returned by the authentication server, the first verification code corresponding to the account identifier;
[0167] The determining unit 83 is configured to determine a first hash value and a second hash value respectively according to a plurality of hardware information of the electronic device; respectively perform bit operations on the first hash value and the second hash value to obtain The results are combined to determine the device fingerprint of the electronic device;
[0...
Embodiment 3
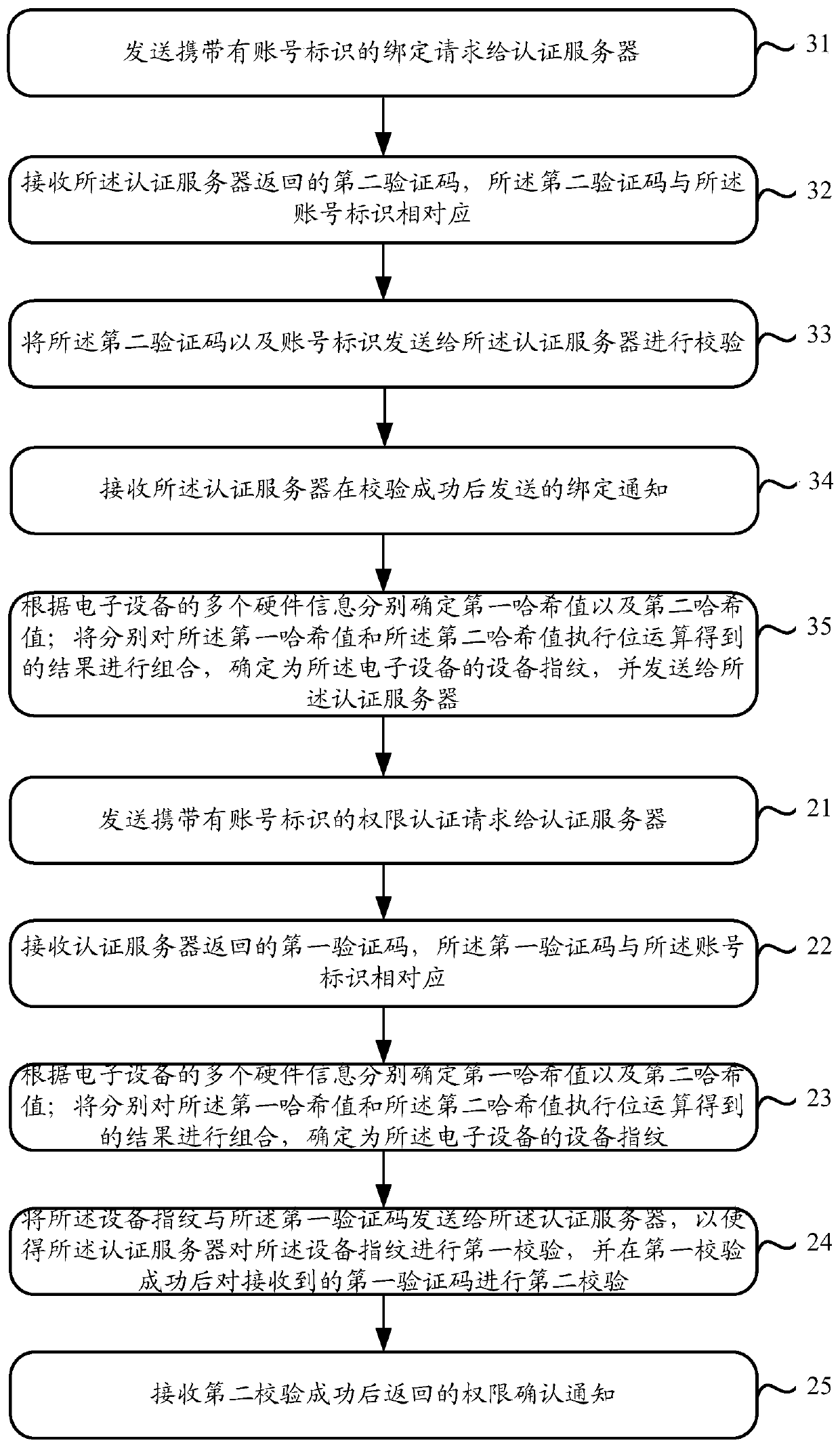
[0184] The embodiment of the present application also provides an authority authentication system, refer to Figure 10As shown, it includes: authority authentication device 1001 and authentication server 1002; wherein,
[0185] The authority authentication device 1001 is configured to send an authority authentication request carrying an account identifier to an authentication server; receive a first verification code returned by the authentication server, and the first verification code corresponds to the account identifier; according to the electronic A plurality of pieces of hardware information of the device respectively determine a first hash value and a second hash value; combining the results obtained by performing bit operations on the first hash value and the second hash value respectively, and determining as the The device fingerprint of the electronic device; sending the device fingerprint and the first verification code to the authentication server, so that the auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com