An Internet of Things node with control and function separation and its security protection method
A technology of separation of functions and the Internet of Things, applied in transmission systems, electrical components, etc., can solve the problems of low CPU performance, complex manufacturers, privacy leakage, etc., to achieve low maintenance and upgrade costs, improve system security, and ensure functional safety. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below with reference to the accompanying drawings and examples.
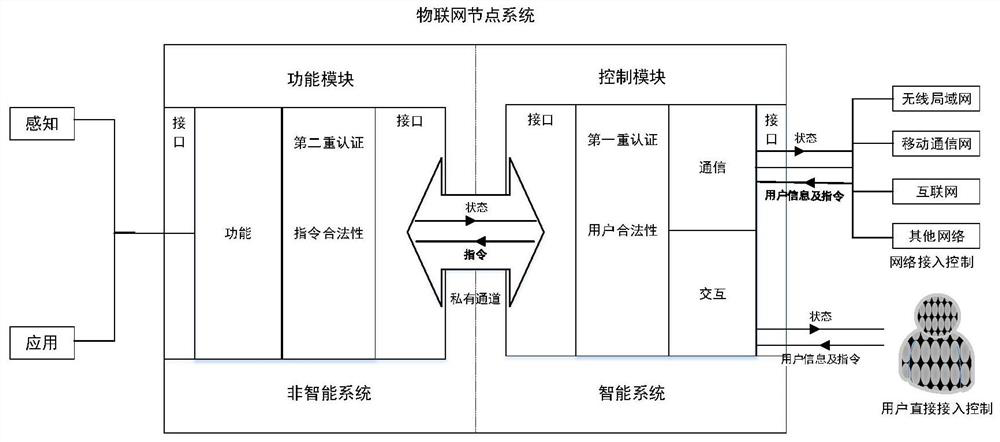
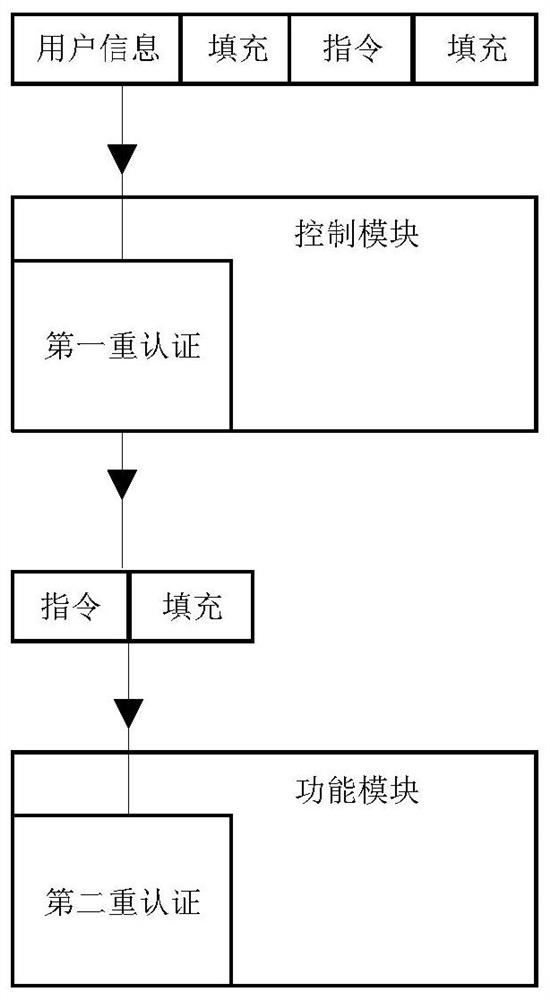
[0036] The IoT nodes in the prior art usually use a single operating system, but according to the functional characteristics of the IoT nodes, the present invention divides the IoT nodes into two parts, control and function, to form a dual system—a control system and a functional system. The nodes are independent of each other, and the double authentication method is adopted to ensure the security of the nodes. The system of the Internet of Things node of the present invention is as figure 1 shown.
[0037] The following describes the sensor chip from three aspects: structural characteristics, safety characteristics and interface characteristics:
[0038] (1) Structural characteristics
[0039] ●Separation of control and function
[0040] IoT nodes are separated into control modules and functional modules, and the two modules work independently of each...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com