Malicious sample homology detection method based on image feature descriptor
A feature descriptor and image feature technology, applied in the field of network security, can solve problems such as weak scalability, weak expansion ability, and insufficient texture features, so as to improve computing efficiency and accuracy, reduce the number of groups and layers, The effect of improving anti-aliasing ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be described in detail below with reference to the accompanying drawings and examples.
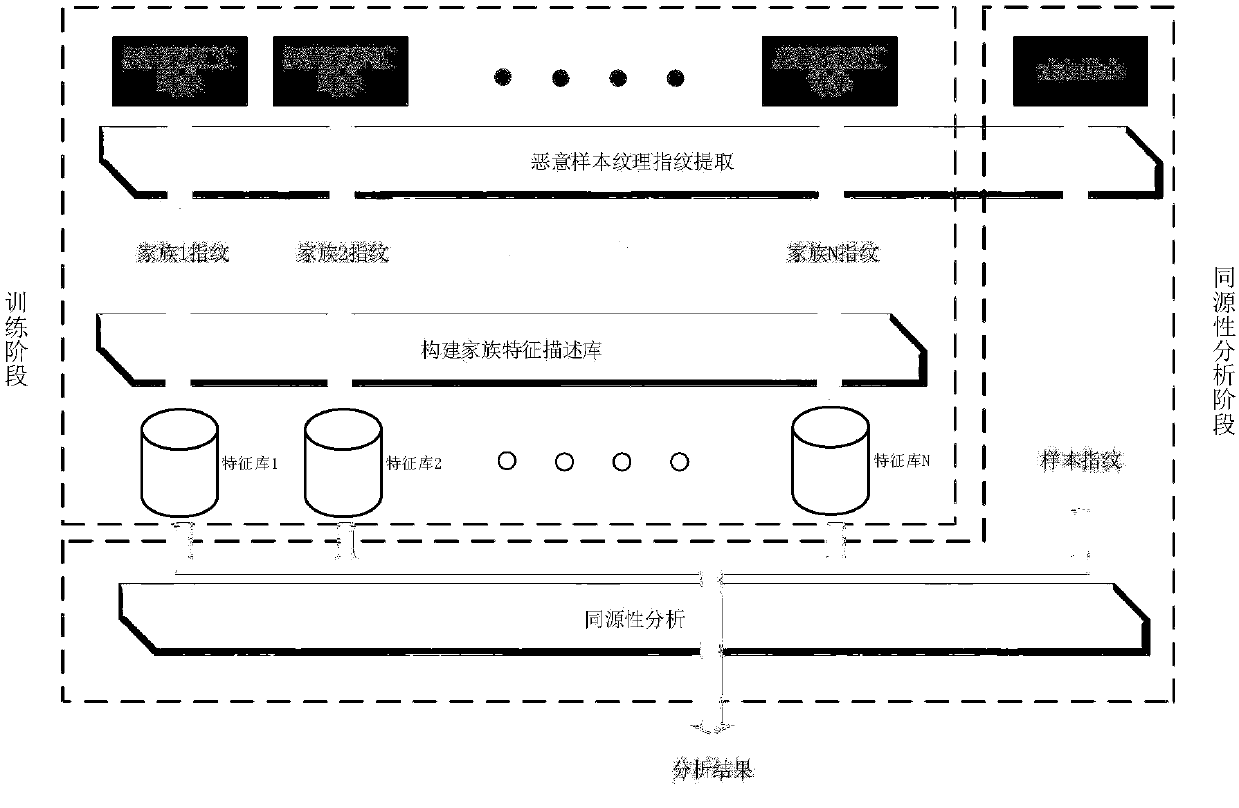
[0050] The present invention provides a malicious sample homologous detection method based on image feature descriptors, which can visualize binary malicious programs without source code, and use image feature extraction methods to locate all feature points of each picture and extract feature descriptors to generate Image texture fingerprint information, so as to accurately and efficiently analyze the type and family of malicious programs. The invention relates to network security, and has an important application in the homology analysis of malicious software.
[0051] Many existing malicious sample variant implementation technologies need complex technical means to avoid in the background of the existing same-source detection technology, and each interference factor requires specific means to eliminate. This invention studies the malicious sample and vari...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com