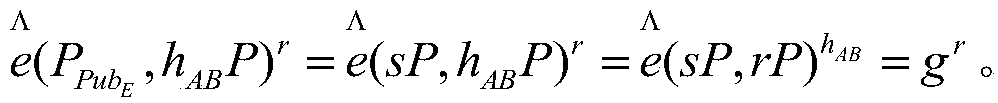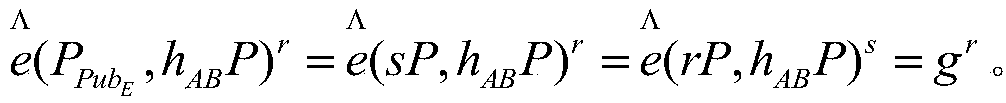Entrustable authentication encryption method
A technology of authentication encryption and custodian, applied in the field of file authentication and encryption, it can solve the problems of inability to satisfy non-repudiation, lose the meaning of digital signature, users cannot choose the custodian by themselves, and achieve non-repudiation and reduce the number of certificates by half. , the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
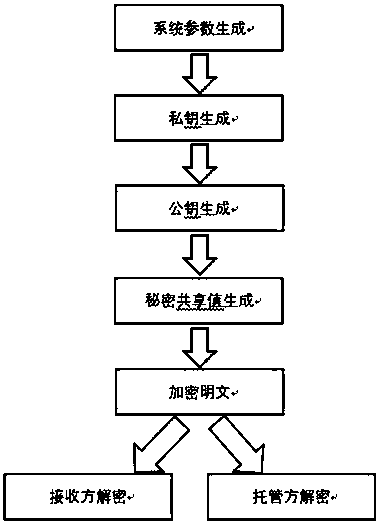
[0020] Further illustrate the technical scheme of the inventive method below in conjunction with accompanying drawing
[0021] A kind of trusteeship authentication encryption method of the present invention, comprises the following steps: system initialization (Setup), private key generation (Key-Gen), encryption algorithm (Encryption), decryption algorithm (Decryption), trusteeship decryption algorithm (Escrow-Decrypt) . Specifically include:
[0022] Step 1: Generate system parameters for encryption and decryption; given a security parameter k, where k is an integer, specify its size according to user security requirements; output two cyclic groups G with order q 1 with G 2 , while generating the group G 1 A generator P of and a bilinear map where q is a prime number. Choose a hash function H whose output is at least 160 bits. The plaintext space is M={0,1} n , the ciphertext space is Among them, n integer system public parameters are 1 ,G 2 ,n,P,H>;
[0023] Ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com