Windows remote desktop file transmission auditing method used for operation and maintenance auditing system
A remote desktop and file transfer technology, applied in the field of operation and maintenance audit, can solve the problems of inability to upload and download files after the operation, and achieve the effect of accurate post-event positioning and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
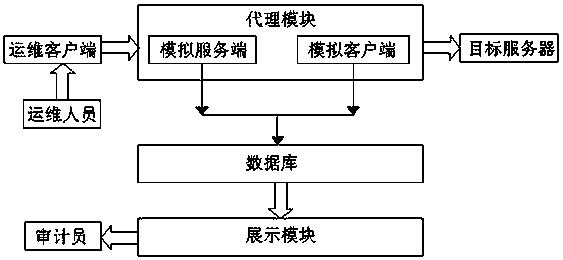
[0050] combined with figure 1 As shown, a Windows remote desktop file transfer audit method for the operation and maintenance audit system, comprising:
[0051] Step S100: establishing a proxy module between the operation and maintenance client and the target server;
[0052] Step S200: The proxy module collects the communication data between the operation and maintenance client and the target server, parses and extracts protocol data, the protocol data includes image data and file data, stores the image data in a database, and stores the File data is restored to file information data and stored in the database;
[0053] Step S300: Read the image data from the database and perform data display after restoring the data, read the file information data from the database and display.
[0054] working principle:
[0055] The operation and maintenance audit system includes an operation and maintenance client, an agent module, a target server, a database, and a display module. The...
Embodiment 2
[0057] On the basis of Example 1, in conjunction with the attached figure 1 As shown, the agent module in the step S100 includes a simulated server connected to the operation and maintenance client and a simulated client connected to the target server, and the specific steps include:
[0058] Step S110: the operation and maintenance personnel operate the client tool on the operation and maintenance client to connect to the simulated server, and the simulated server and the operation and maintenance client complete connection initialization and connection authority setting;
[0059] Step S120: The simulated client of the proxy module connects to the server, and the simulated client completes connection initialization and connection authority setting with the server;
[0060] Step S130: The simulation server of the proxy module calls the simulation client after receiving the data sent by the operation and maintenance client, and the simulation client forwards the data to the tar...
Embodiment 3
[0074] On the basis of embodiment 2, in conjunction with the attached figure 1 As shown, the step S200 specifically includes:
[0075] Step S210: the simulated server and the simulated client in the proxy module extract communication data during data forwarding between the operation and maintenance client and the target server;
[0076] Step S220: the proxy module uses the RDP protocol to parse the communication data to obtain protocol data;
[0077] Step S230: storing the image data in the protocol data into the database according to the original acquisition order;
[0078] Step S240: restore the file information data in the protocol data to a file operation record, the file operation record is identifiable file information, including file size, transmission start and end time, transmission rate, file operation result, and the file operation Records are stored in the database in the order in which they were originally collected.
[0079] working principle:
[0080] The si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com