Data transmission method and computer program
A data transmission method and data technology, applied in computer security devices, computing, digital data protection, etc., can solve problems such as inability to obtain data, no data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
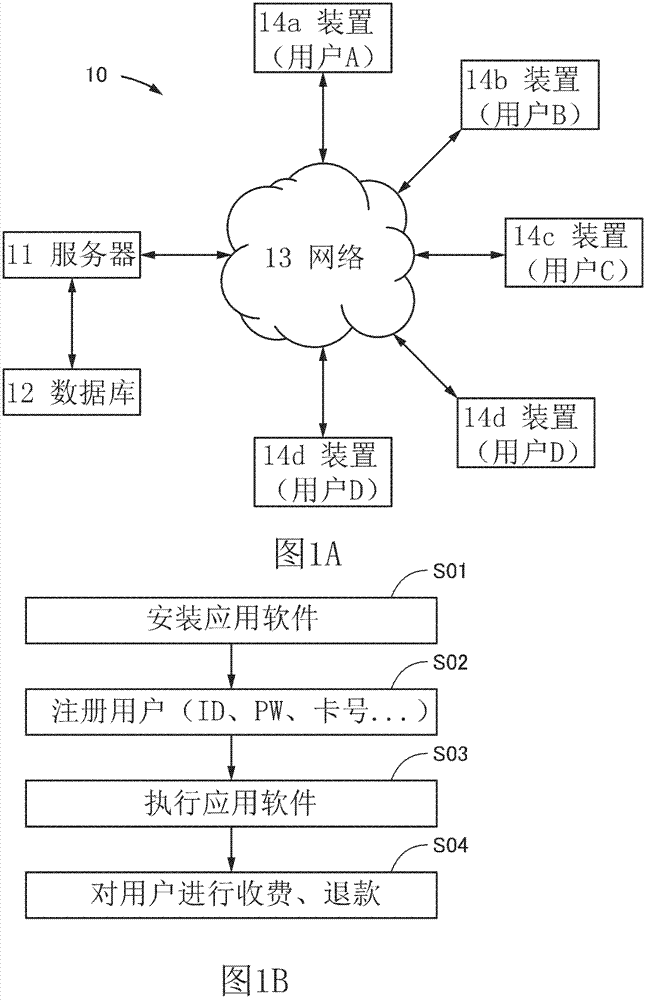
[0067] Figure 1A The configuration of the electronic device system described in this embodiment is shown. In the electronic equipment system 10, the server 11 communicates with multiple users (in Figure 1A , the portable terminals (device 14a to device 14e) of user A to user D) are connected. User D owns device 14d and device 14e.
[0068] The server 11 is operated by an information provider, and receives required data from a database 12 . The database stores data and the like necessary for execution of the application software. Although not shown, the server 11 sometimes receives data from other providers or the like via the network 13 and provides the data to the user. Details of the devices 14 a to 14 e will be described in Embodiment Mode 5. FIG.
[0069] Figure 1B Shows the order of use of application software. A user installs application software provided by an information provider in his own portable terminal (device) before receiving information from the server...
Embodiment approach 2
[0109] In the method described in Embodiment 1, the user's device transmits its unique information such as its serial number. Since the inherent information is transmitted through the network 13, it is necessary to prevent the information from being known by a third party. For this purpose, for example, the inherent information may be encrypted using a common encryption technology (eg, Transport Layer Security (TLS), etc.).
[0110]However, there is no guarantee that common encryption techniques are free from loopholes. Even if TSL is used for transmission, there is a possibility that the inherent information will be cracked and a third party may obtain the encryption key and decryption key. In order to prevent this from happening, it is preferable to update the encryption key and decryption key regularly. In general, decryption of encrypted data takes a considerably long time, and therefore, it is preferable to update the encryption key and the decryption key at intervals as...
Embodiment approach 3
[0122] In this embodiment, use Figure 7 Other examples illustrating encryption and decryption. The contents of Embodiment 1 can be appropriately referred to.
[0123] First, when the application software is executed, the device 14a generates an encryption key Key1 and a decryption key Key4 (encryption key and decryption key generation step S14a). The data encrypted with the encryption key Key1 needs to be decrypted with the decryption key Key4 as described below. In addition, the encryption key Key1 and the decryption key Key4 are different.
[0124] When generating the encryption key Key1 and the decryption key Key4, for example, the serial number (manufacturing number, individual identification number, etc.) of the device 14a can be used. The serial number is an example of information (specific information) for identifying the device 14a. Instead of the serial number, other information capable of identifying the device 14a may be used.
[0125] Other information may be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com