Method for automatically detecting core characteristics of malicious code
An automatic detection and malicious code technology, which is applied in the field of automatic detection of core features of malicious code and overall design of computer system security, can solve problems such as difficulty in extracting malicious code family features, and achieve the effect of not being easily confused and good detection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
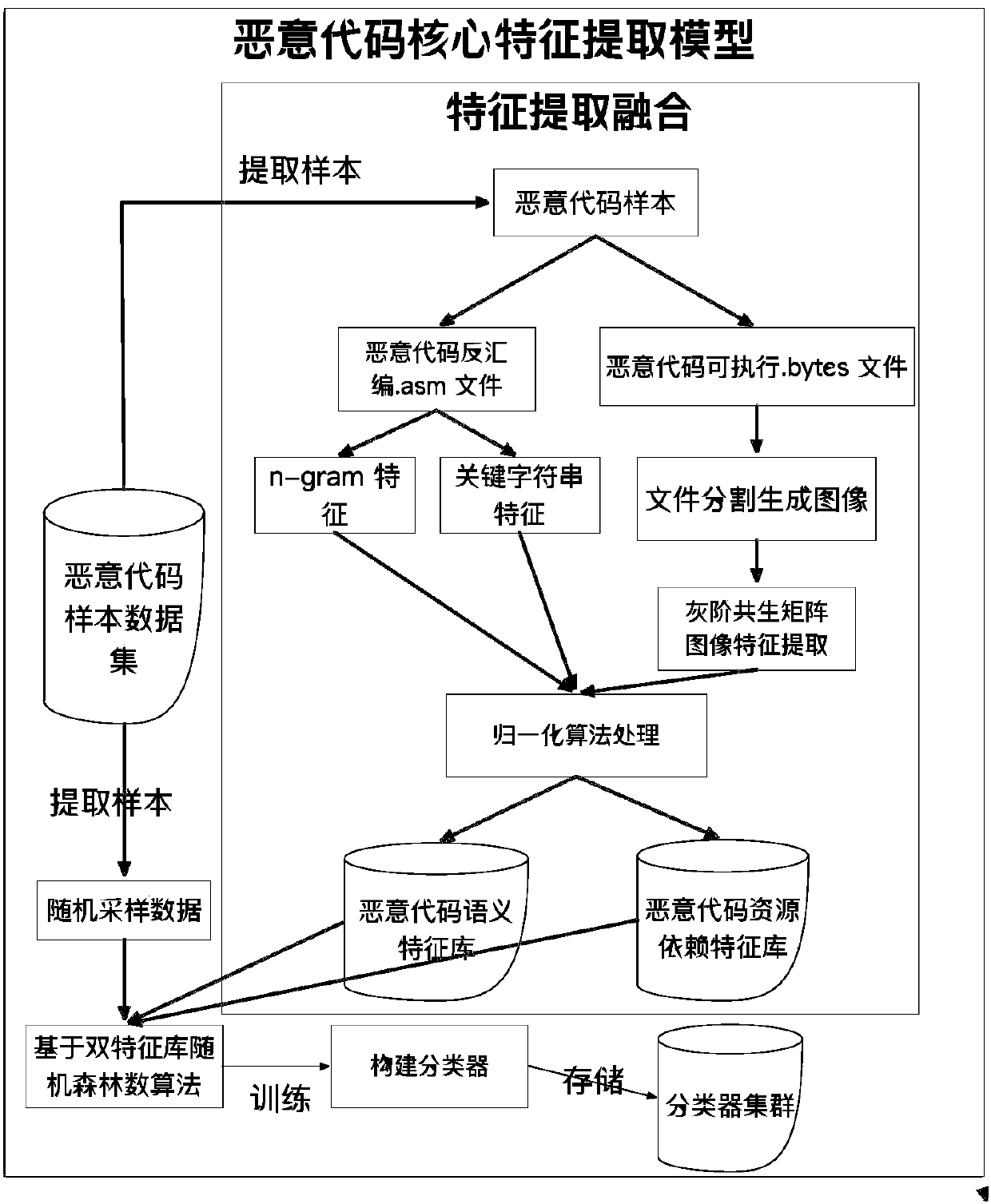
[0046] The technical solution adopted in the present invention is a method for automatically detecting core features of malicious codes, which is a method for core features of malicious codes based on machine learning algorithms. Through static analysis, this method extracts features such as image textures, key API calls, and key strings of malicious codes from the perspective of the actual security significance of malicious codes. The extracted features are learned through the random forest tree algorithm based on the normalized double feature library, and the core feature library of the malicious code family is obtained.
[0047] First, the overall structure of the core feature extraction method
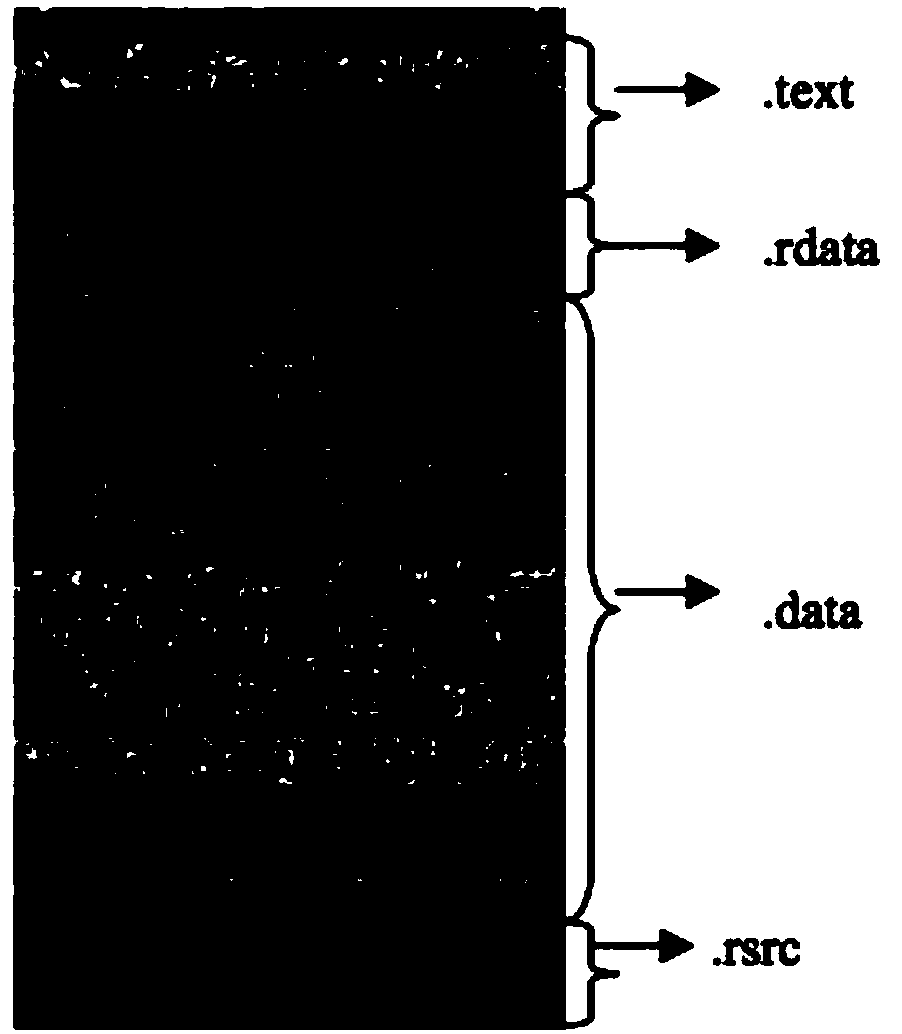
[0048] Nowadays, malicious code samples often use multiple obfuscation methods, and a single feature extraction method is very easy to break. In order to improve the anti-interference performance of the finally extracted core features, the present invention uses three feature extr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com