A security system for securities transactions and a security verification method for securities transactions
A security system and transaction technology, applied in the field of securities transaction security system, can solve problems such as increased implementation and management, difficulties, and inability to fundamentally guarantee data security, and achieve the effect of accurate transaction data and protection security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
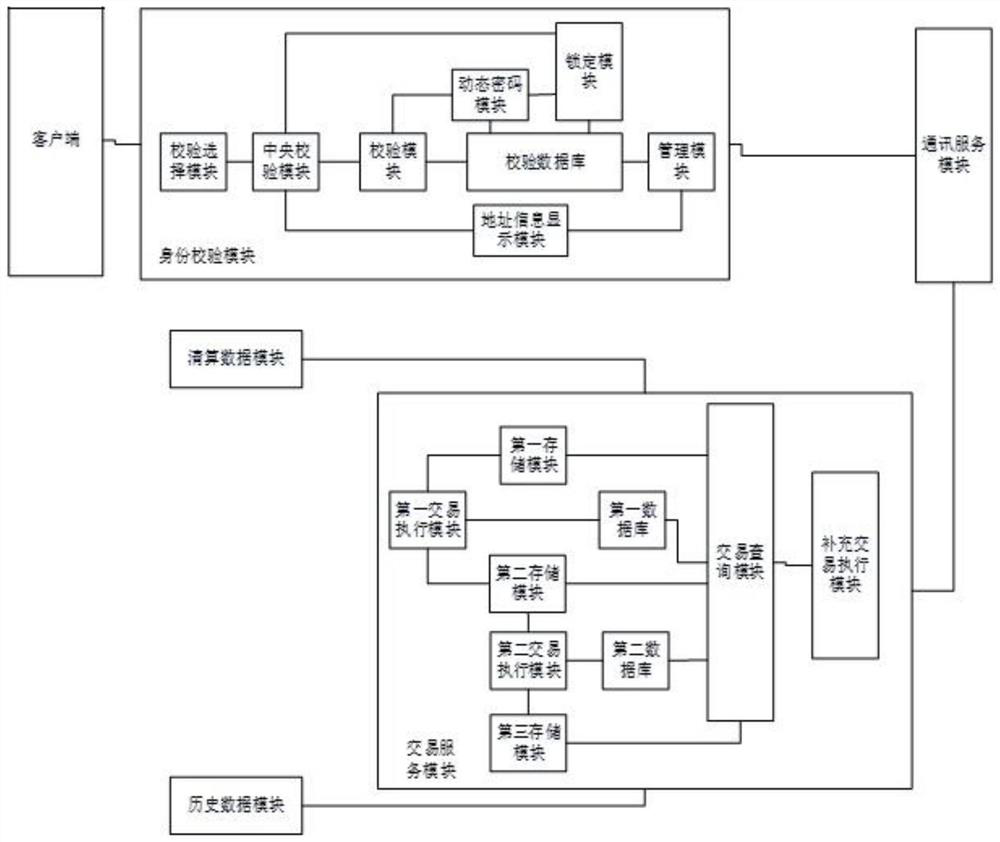
[0014] see figure 1 , is a structural block diagram of the security system for securities of the present invention, wherein the security system for securities transactions includes a client, an identity verification module, a communication service module, a transaction service module, a historical data module, and a clearing data module, wherein , the client terminal, the identity verification module, the communication service module, and the transaction service module are connected in sequence, and the historical data module and the clearing data module are respectively connected to the transaction module.
[0015] The following is a detailed description of the verification process and the specific structure of the verification module, see figure 1 , the identity verification module includes: a verification selection module, a central verification module, a verification module, a verification database, a locking module, a dynamic password module, an information module, a mana...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com