Method and apparatus for detecting network flooding attack
A flood attack and detection method technology, applied in the field of computer networks, can solve problems such as inaccurate threshold configuration, and achieve the effects of reducing customer complaints, great flexibility, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to detect the network flooding attack on the server, it is necessary to connect the detection device to the network to be detected, which can be accessed from the bypass or serially.
[0023] Bypass or serially connect the detection device to the network to be detected
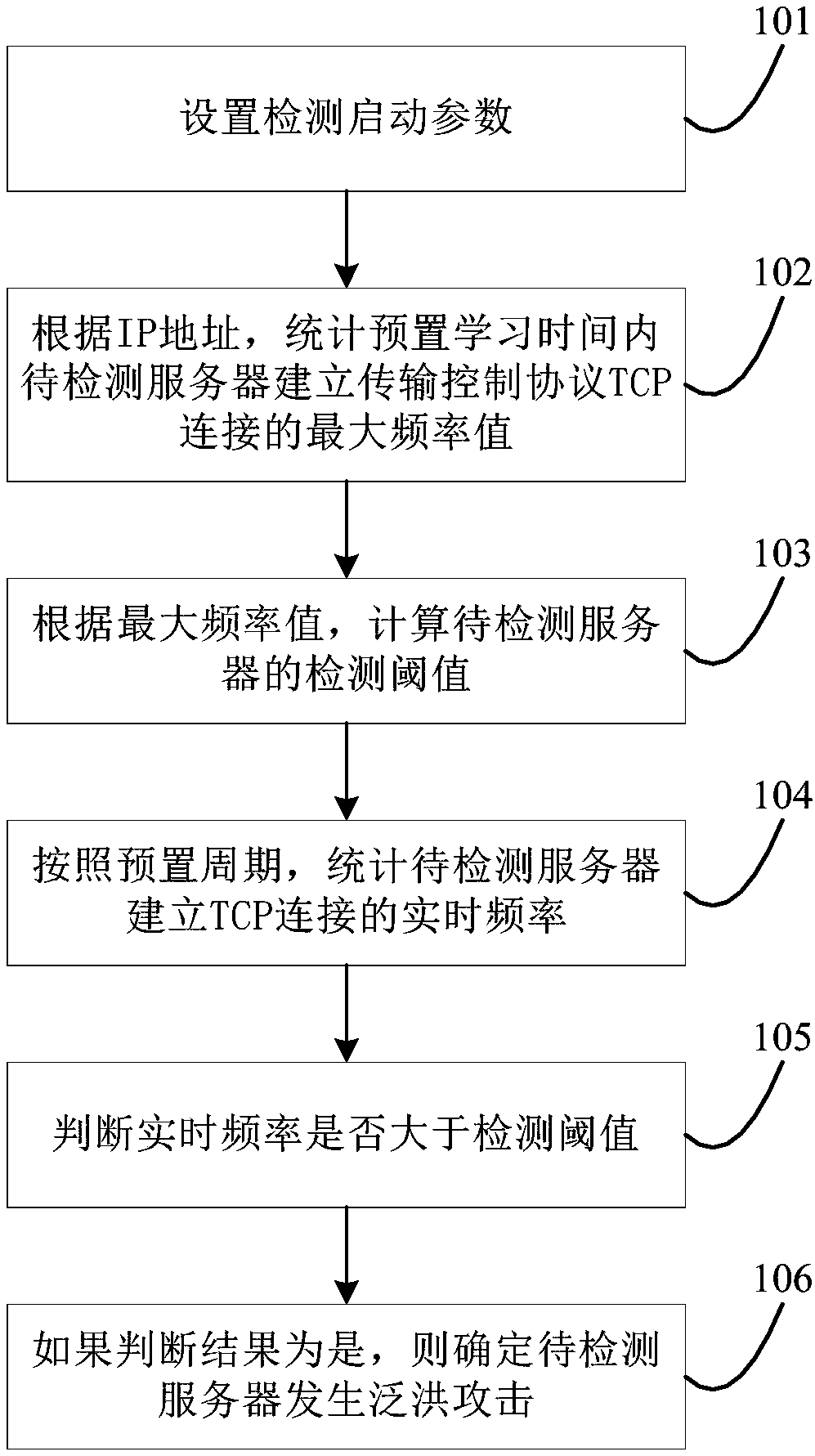
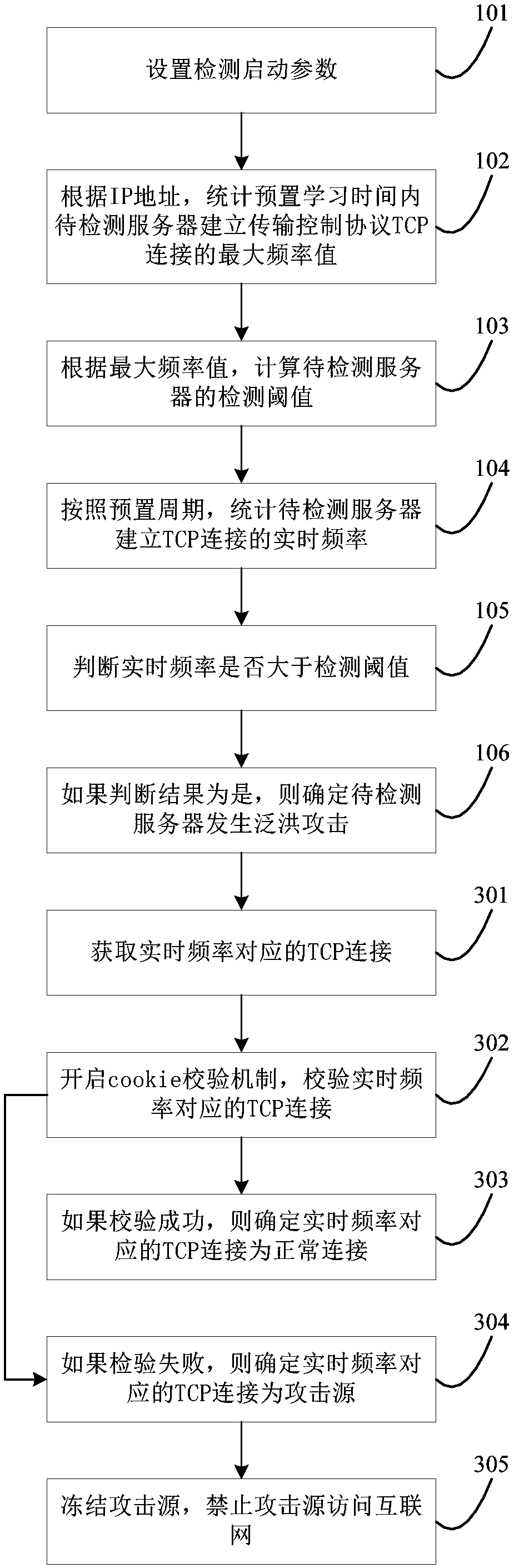
[0024] see figure 1 , is a flow chart of a method for detecting a network flood attack provided by the present application. like figure 1 As shown, the method includes:
[0025] 101. Set detection start parameters.
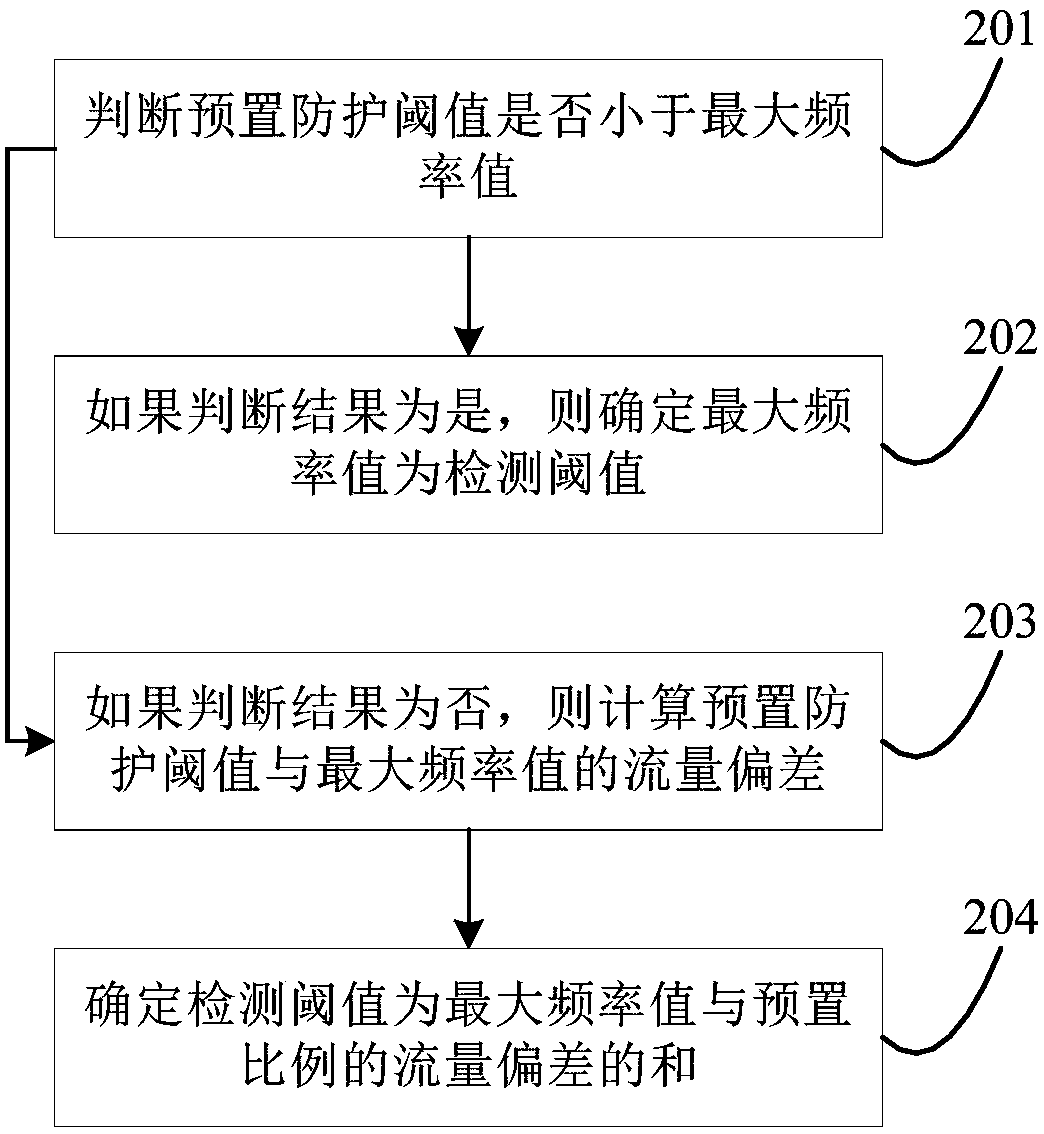
[0026] The detection startup parameters include the network interconnection protocol IP address of the server to be detected and the preset protection threshold. The IP address is used to select the server to be detected, and to detect the network flood attack on the server to be detected. The preset protection threshold is selected before detecting network flood attacks. It is an empirical value and a general value. The preset protection threshold is not a specific threshold...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com