Method and system for performing security control using security device
A technology of safety equipment and safety control, which is applied in the electronic field to achieve the effect of avoiding information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] This embodiment provides a method for performing security control by using a security device.
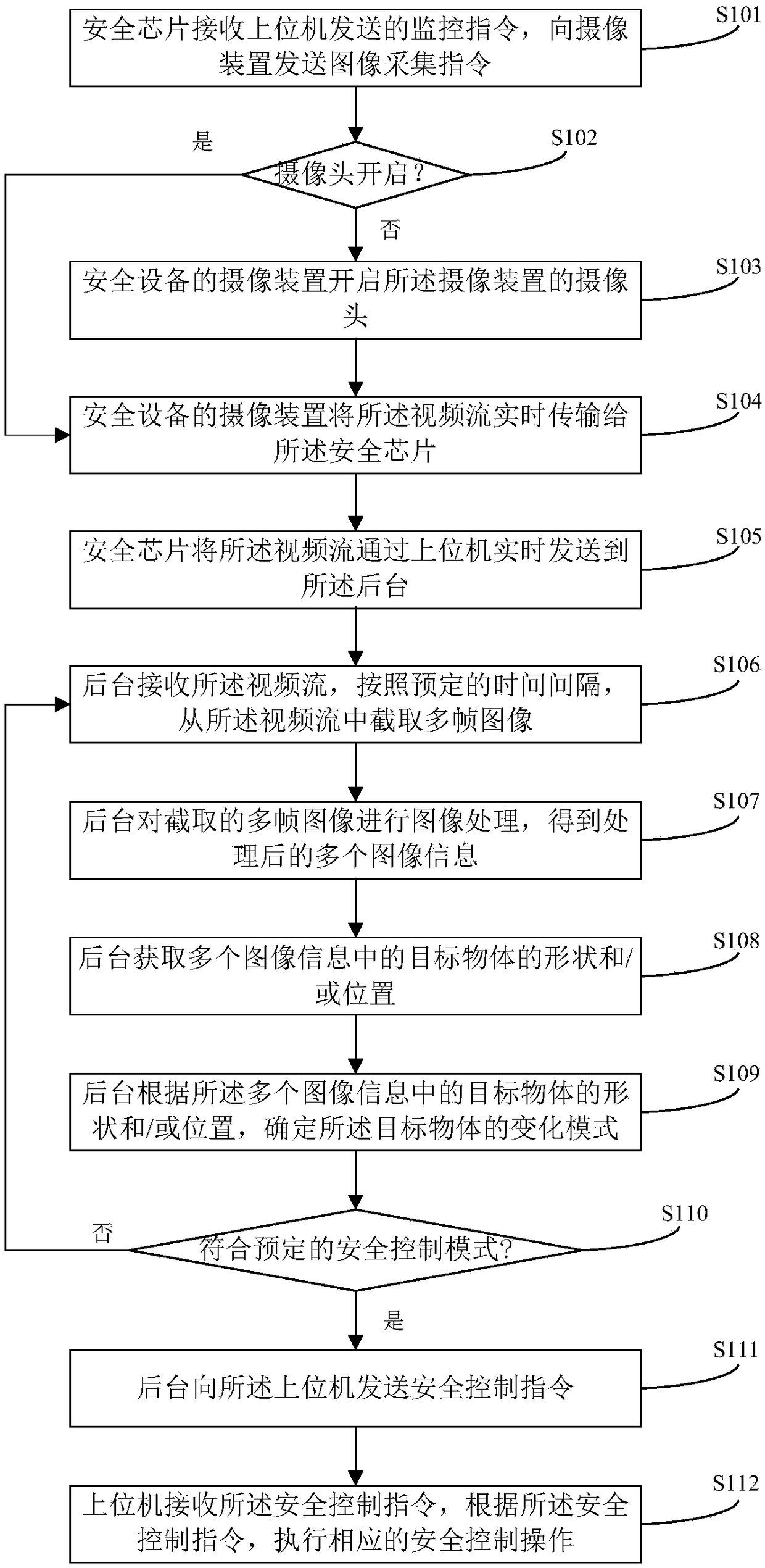
[0031] figure 1 A flow chart of a method for using security equipment to perform security control provided in this embodiment, as shown in figure 1 As shown, the method mainly includes the following steps:
[0032] In step S101, the security chip of the security device sends an image acquisition command to the camera device of the security device after receiving the monitoring command sent by the host computer after successfully logging in to the system client, instructing the camera device to perform image capture.
[0033] In this embodiment, the user logs in to the system through the system client of the upper computer. After logging in to the system, the user enters a security state and needs to monitor the user's current environment. The upper computer sends a monitoring command to the security chip of the security device.
[0034] In a specific application, the securi...
Embodiment 2
[0059] This embodiment provides a system for performing security control by using a security device, and the system can be used to implement the method provided in Embodiment 1 above.
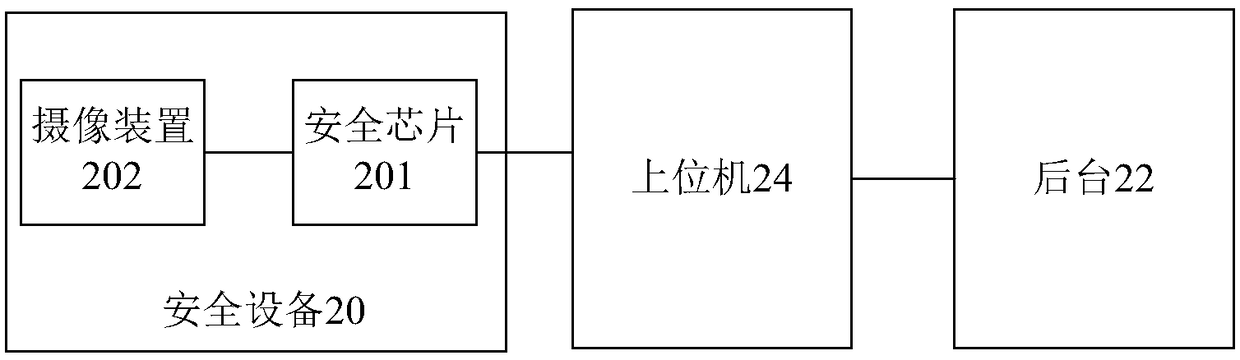
[0060] figure 2 A schematic diagram of the architecture of a system using security devices for security control provided in this embodiment, as shown in figure 2 As shown, the system mainly includes: a security device 20 , a background 22 and a host computer 24 . The functions of each component in the system will be described below, and other related matters can be referred to the description of Embodiment 1.
[0061] In this embodiment, the upper computer 24 is configured to send a monitoring instruction after successfully logging in to the system client.
[0062] Such as figure 2As shown, the safety device 20 mainly includes: a safety chip 201, configured to send an image acquisition instruction to the camera device 202 of the safety device 20 after receiving the monitoring instruction,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com