Energy internet communication security system and method based on chaotic system array
A technology of energy Internet and chaotic system, which is applied in the direction of secure communication, transmission system, and digital transmission system through chaotic signals, which can solve the problems of low complexity of chaotic sequences, complex nonlinear behavior, and large key space, and achieve processing Strong data capability, rich key space, and safe and reliable system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
[0049] 1) In this example, according to the design principles of typical digital systems, the appropriate method will be selected as To implement, provide an implementation example that simply uses a difference equation, namely:
[0050] x(k+1)=(Ax(n)+gx(n)) dt+x(n)
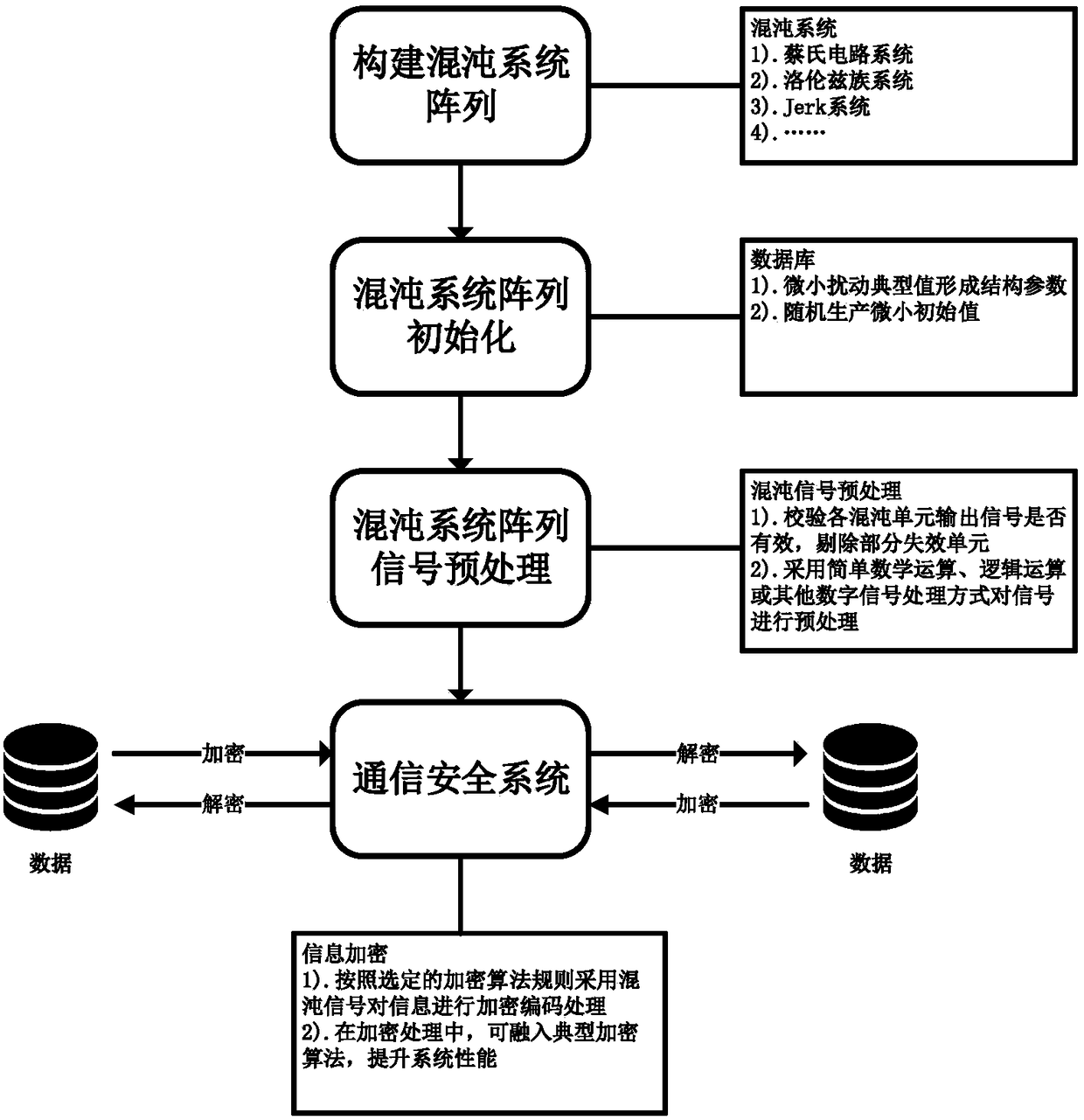
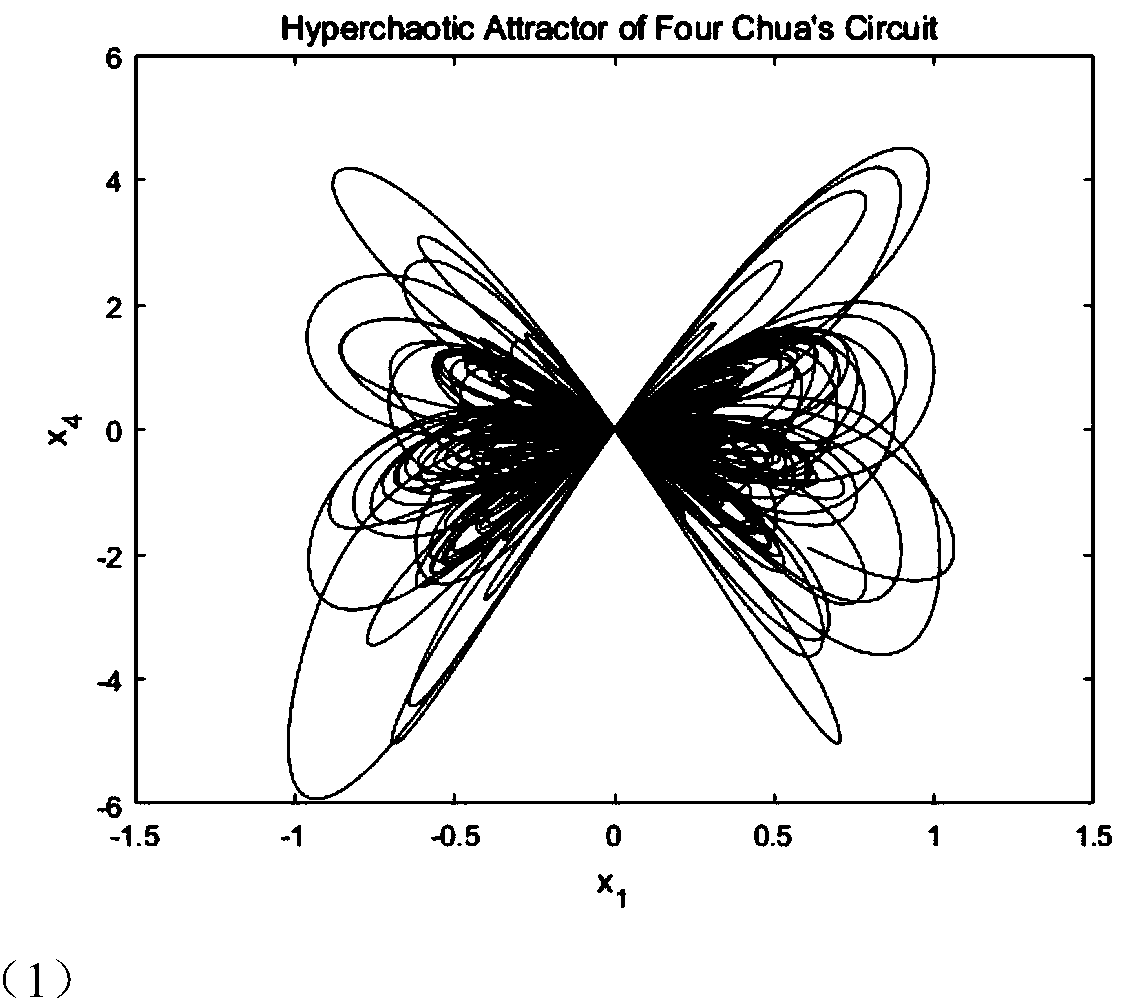
[0051] The realized system forms a chaotic array according to certain principles. The present invention selects Chua's circuit system, Lorentz system, Chen's system and Lu's system to form an m*n chaotic array.
[0052]
[0053] In the formula, i and j represent the row and column coordinates of the array, respectively.
[0054] 3) In order to realize the control of the chaotic system array, the present invention adopts the method of controlling the system structure parameters and system initial values of the chaotic units. The system structural parameters can be generated in the following ways, but not limited to, the parameter library is obtained by perturbing the typical structural parameters
[0055...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com