Method for secure data transmission, access network, terminal and core network device
A technology of access network equipment and core network equipment, which is applied in the field of secure data transmission, and can solve problems such as threatening the security of network slices and cracking master secret keys, so as to improve flexibility and differentiation, realize security, and solve data loss Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
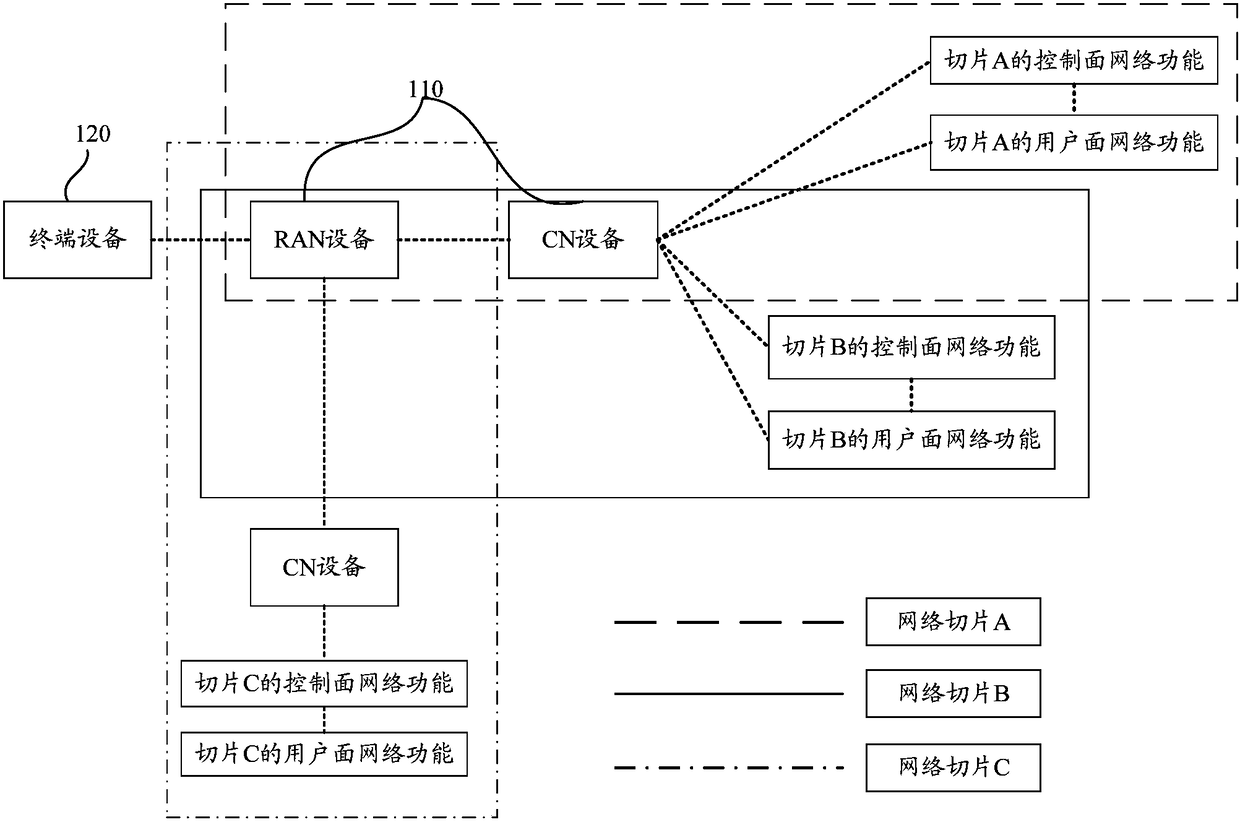
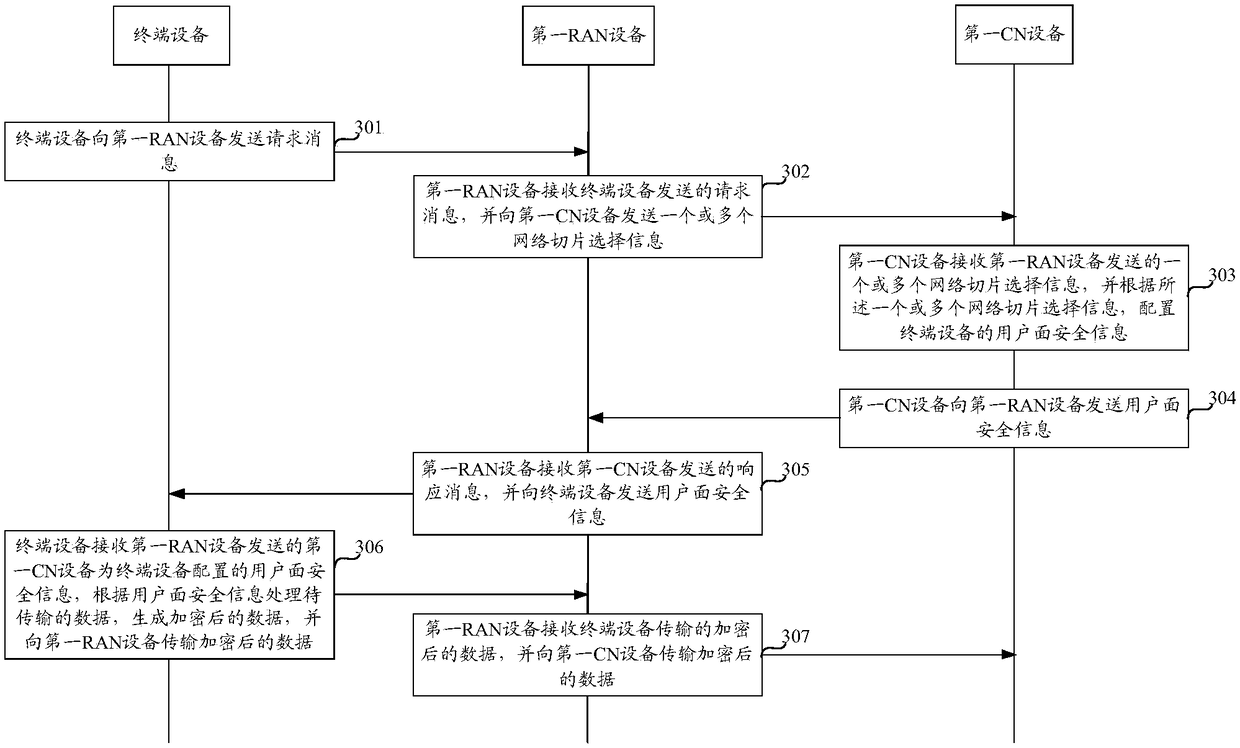
[0072] figure 2 It exemplarily shows a system architecture applicable to the embodiment of the present invention. Based on the system architecture, the process of secure data transmission can be realized. The system architecture of secure data transmission provided by the embodiment of the present invention may include network equipment 110 and terminal equipment 120.
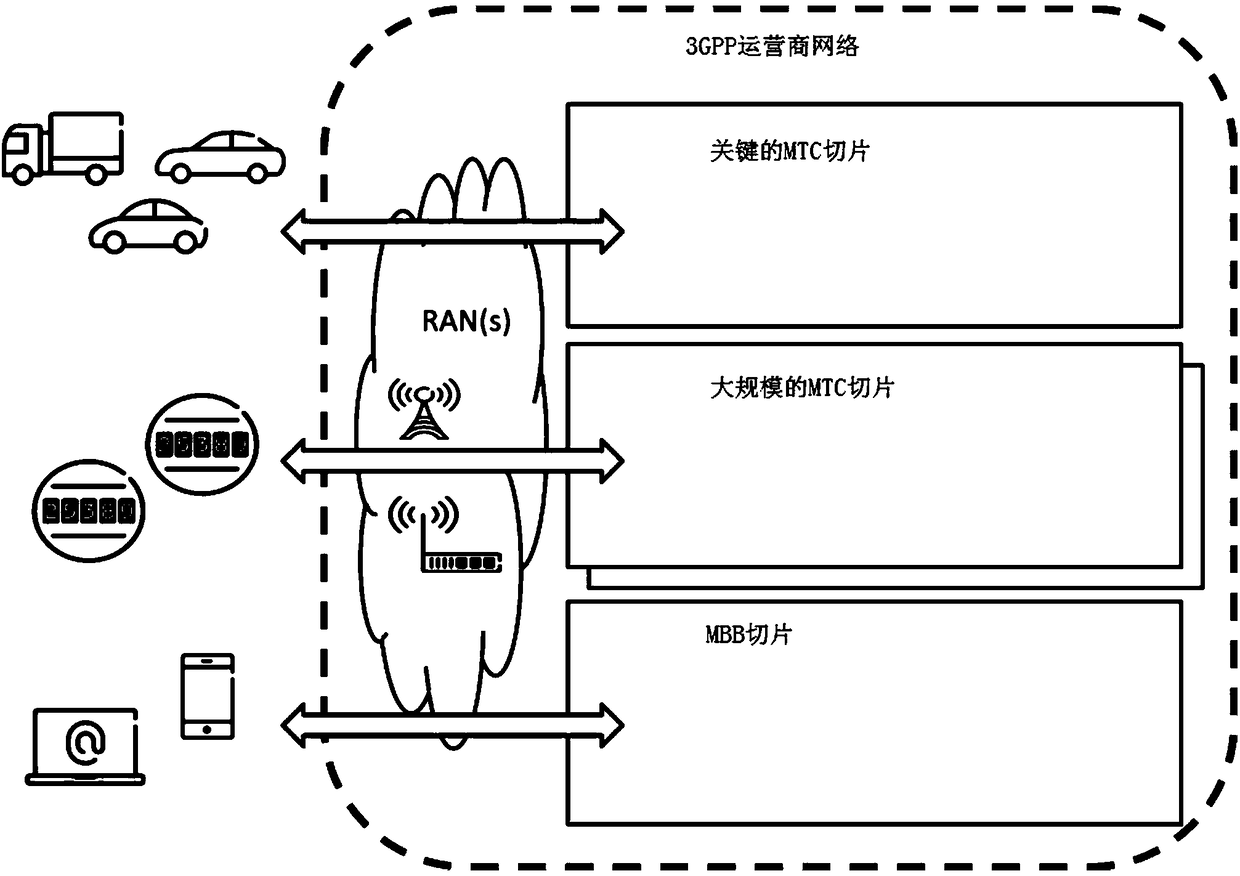
[0073] Wherein, the network device 110 may include an access network (Radio Access Network, RAN)) device and a core network (Core Network, CN) device communicating with the terminal device 120, and the RAN device may be an access point (ACCESS POINT, AP) in the WLAN. ), a base station (Base Transceiver Station, BTS) in GSM or CDMA, or a base station (NodeB, NB) in WCDMA, or an evolved base station (Evolutional Node B, eNB or eNodeB) in LTE, or a relay station Or access points, or vehicle-mounted devices, wearable devices, and network devices in future 5G networks or network devices in future evolved PLMN netw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com