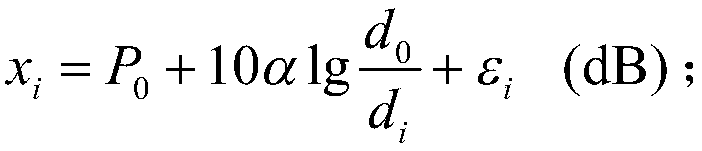Sensing data error attack detection method based on random sampling consistency
A random sampling and sensing data technology, which is applied in the direction of services, security devices, and electrical components based on specific environments, can solve the problems of high cost of deploying trusted nodes, large amounts of data, and the number and location of effective trusted nodes to be studied. Achieve the effect of improving system robustness and reducing communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
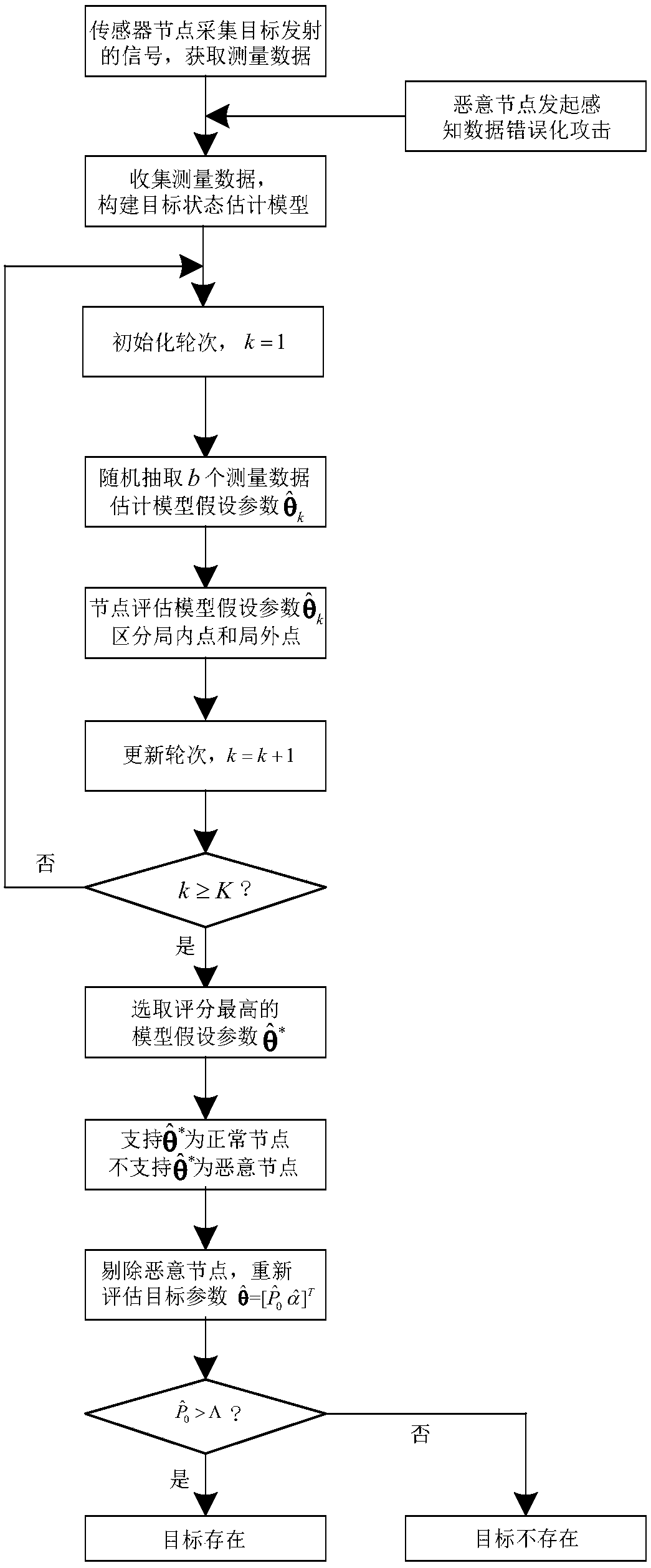
[0055] The technical solution of the present invention will be described in detail below with reference to the accompanying drawings and examples.
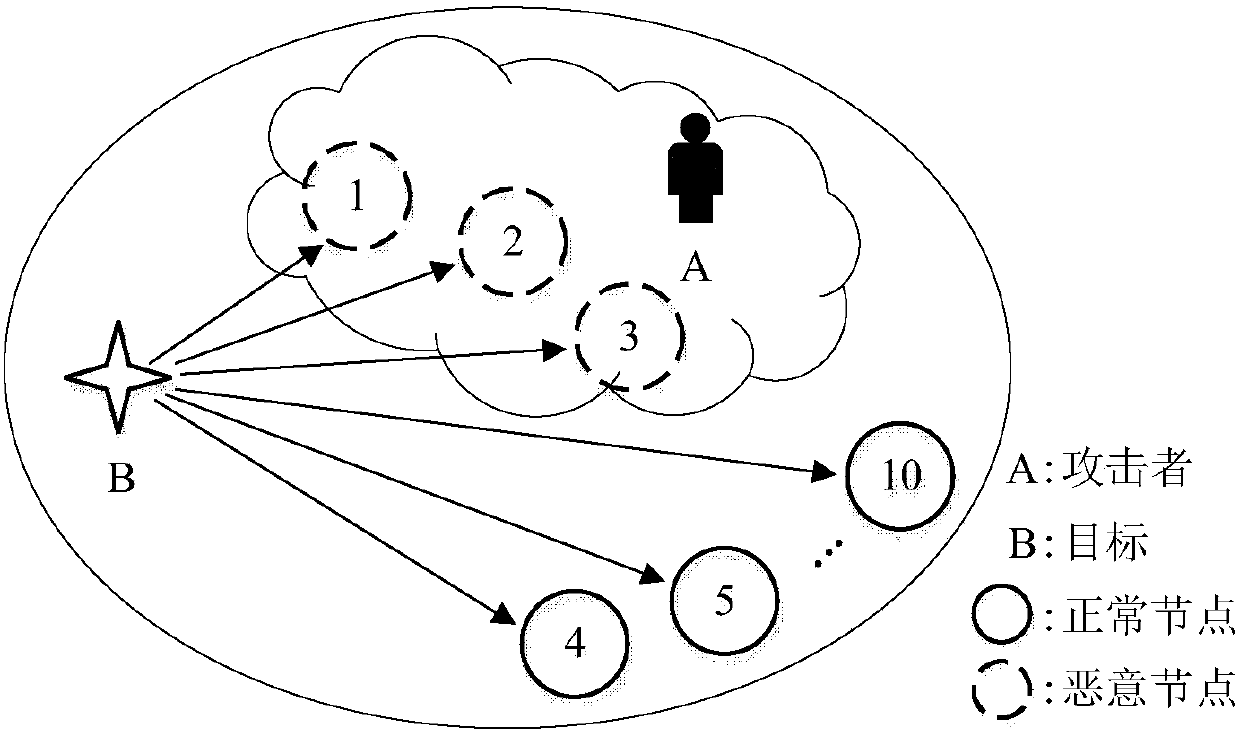
[0056] as attached figure 1 As shown, the system model of this embodiment is: there is a target in the network, as shown in the attached figure 1 As shown by the star in the middle; 10 sensor nodes are deployed in the network, as shown in the attached figure 1 As shown in the middle circle, the numbers are 1, 2, ..., 10. The attacker successfully captured the nodes numbered 1 to 3, making them malicious nodes, and the malicious nodes are as attached figure 1 Shown in the dotted circle. Nodes numbered 4 to 10 are normal nodes, as attached figure 1 Shown in solid circle. The power of the measurement noise at node i In this instance i=1,2,...,10. The distance d between node i and the target i And the distances are not equal to each other, in this example d 1 to d 10 1.5, 1.8, 2, 2.2, 2.5, 2.8, 3, 3.2, 3.6, 4 respectively...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com